A dropper in malware is a type of malicious software designed to install other harmful programs onto a target system. This entity functions by delivering payloads such as ransomware, spyware, or keyloggers, thereby compromising the device's security. Droppers often evade detection by remaining dormant until activated, making them a critical threat in cybersecurity. One common example of a dropper is the Emotet malware, which initially appeared as a banking Trojan before evolving into a versatile dropper that spreads various payloads. Emotet infiltrates systems through phishing emails containing malicious attachments or links, then downloads additional malware components. Security teams focus on identifying dropper behavior to halt multi-stage attacks and mitigate potential data breaches.
Table of Comparison
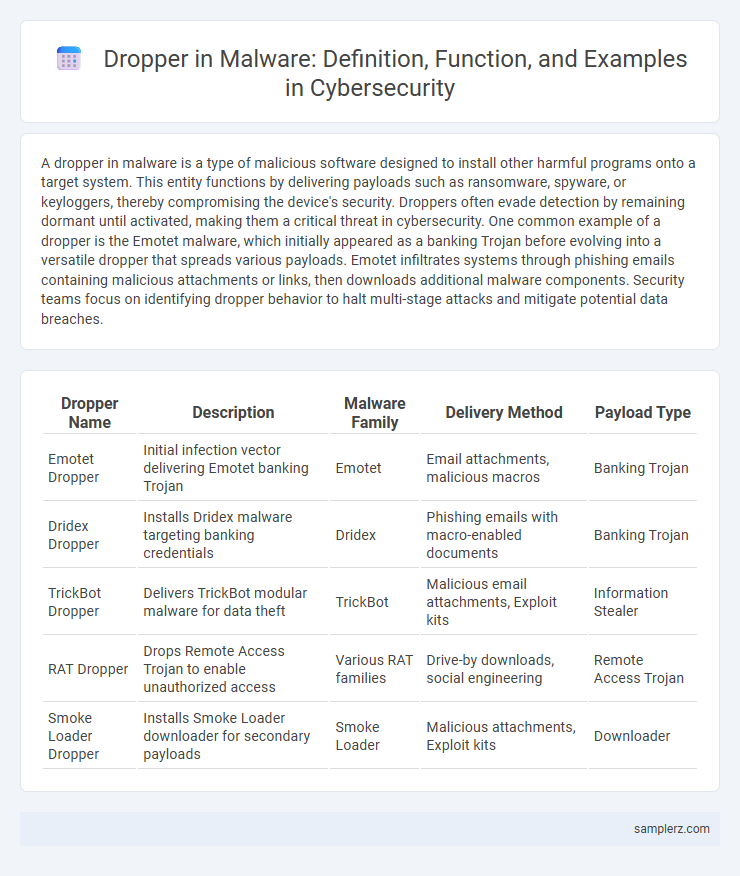
| Dropper Name | Description | Malware Family | Delivery Method | Payload Type |
|---|---|---|---|---|
| Emotet Dropper | Initial infection vector delivering Emotet banking Trojan | Emotet | Email attachments, malicious macros | Banking Trojan |
| Dridex Dropper | Installs Dridex malware targeting banking credentials | Dridex | Phishing emails with macro-enabled documents | Banking Trojan |
| TrickBot Dropper | Delivers TrickBot modular malware for data theft | TrickBot | Malicious email attachments, Exploit kits | Information Stealer |
| RAT Dropper | Drops Remote Access Trojan to enable unauthorized access | Various RAT families | Drive-by downloads, social engineering | Remote Access Trojan |
| Smoke Loader Dropper | Installs Smoke Loader downloader for secondary payloads | Smoke Loader | Malicious attachments, Exploit kits | Downloader |
Introduction to Droppers in Malware
Droppers are specialized malware designed to infiltrate a system and install additional malicious payloads covertly. Common examples include Emotet and TrickBot, which deploy secondary malware such as ransomware or spyware after initial infection. These droppers exploit vulnerabilities in software or use social engineering techniques to evade detection and ensure persistent compromise within targeted environments.
How Droppers Work in Cyber Attacks
Droppers in malware serve as stealthy installers that deliver and activate malicious payloads on a victim's device by bypassing security defenses. They often exploit vulnerabilities or social engineering tactics to execute code that downloads or unpacks additional malware components, enabling full compromise. This process allows attackers to maintain persistence, escalate privileges, and evade detection in complex cyber attack campaigns.
Common Techniques Used by Droppers
Droppers commonly employ techniques such as code obfuscation, encryption, and the use of packers to evade detection by antivirus software. They often leverage social engineering tactics, including phishing emails and fake software updates, to trick users into executing the malicious payload. Fileless dropper methods exploit legitimate system processes and memory-resident malware to avoid leaving traces on the disk.
Real-World Examples of Dropper Malware
Emotet is a notorious dropper malware known for distributing banking Trojans and ransomware by embedding itself in email attachments and exploiting vulnerabilities in Microsoft Office macros. TrickBot operates as a modular dropper that delivers a wide range of payloads, including credential stealers and lateral movement tools, often used in coordinated cyberattacks targeting financial institutions. Another example, LokiBot, functions as a dropper by infiltrating systems through phishing campaigns, enabling attackers to harvest sensitive information such as login credentials and cryptocurrency wallets.
Notorious Dropper Variants in History
Notorious dropper variants in malware history include Emotet, which initially spread as a banking Trojan but evolved into a modular dropper deploying various payloads. Another example is Dridex, known for its sophisticated dropper mechanism that delivers credential-stealing malware targeting financial institutions. The Ursnif dropper is also significant, utilizing multi-stage infection techniques to distribute information-stealing and ransomware payloads efficiently.
Detection Methods for Droppers
Detection methods for droppers in malware primarily involve behavior-based analysis, leveraging sandbox environments to observe suspicious file execution and network activity. Signature-based detection remains vital through the use of updated antivirus databases that identify known dropper code patterns and associated payloads. Machine learning models enhance detection efficacy by analyzing anomalous system behaviors and code characteristics indicative of dropper activity.
Prevention Strategies Against Droppers
Preventing droppers in malware requires implementing robust endpoint protection solutions that detect and block suspicious file downloads and executions. Employing behavior-based malware detection systems can identify and quarantine dropper activity before payload installation occurs. Regularly updating software and enforcing strict access controls minimizes vulnerabilities that droppers exploit to infiltrate systems.
The Role of Droppers in Advanced Persistent Threats
Droppers in malware serve as initial infection vectors that deliver payloads stealthily in Advanced Persistent Threats (APTs), enabling attackers to maintain prolonged, undetected access. These dropper components often utilize obfuscation and encryption to bypass security defenses and deploy multiple stages of malicious modules. Their critical role lies in facilitating lateral movement, privilege escalation, and persistent command-and-control communication within targeted networks.
How Droppers Evade Security Solutions
Droppers evade security solutions by using polymorphic code techniques that continuously change their appearance, making signature-based detection ineffective. They often employ obfuscation methods and encrypted payloads to conceal malicious intentions from sandbox analysis and antivirus heuristics. Advanced droppers also exploit zero-day vulnerabilities to bypass endpoint protection and inject malware directly into trusted processes, minimizing detection risks.
Future Trends in Dropper Malware Development
Future trends in dropper malware development emphasize increased use of polymorphic techniques to evade signature-based detection. Emerging droppers leverage AI-based obfuscation and multi-stage infection chains to enhance stealth and persistence. Integration with cloud services for dynamic payload delivery is projected to amplify their adaptability and global reach.
example of dropper in malware Infographic
 samplerz.com
samplerz.com