A blackhole in traffic filtering refers to a network security technique where unwanted or malicious network traffic is deliberately dropped or discarded without notifying the source. This method is often used to mitigate Distributed Denial of Service (DDoS) attacks by routing harmful traffic into a "blackhole," effectively isolating it from the rest of the network. Network devices like routers and firewalls implement blackhole filtering by redirecting traffic destined for specific IP addresses or ranges into a null route. Blackhole filtering enhances security by preventing the propagation of harmful data packets that could disrupt services or compromise systems. Organizations deploy blackhole routes as part of their traffic management strategies to ensure network resilience and protect critical infrastructure. Data from network monitoring tools help identify attack patterns and determine which IP blocks should be blackholed, optimizing defensive measures.
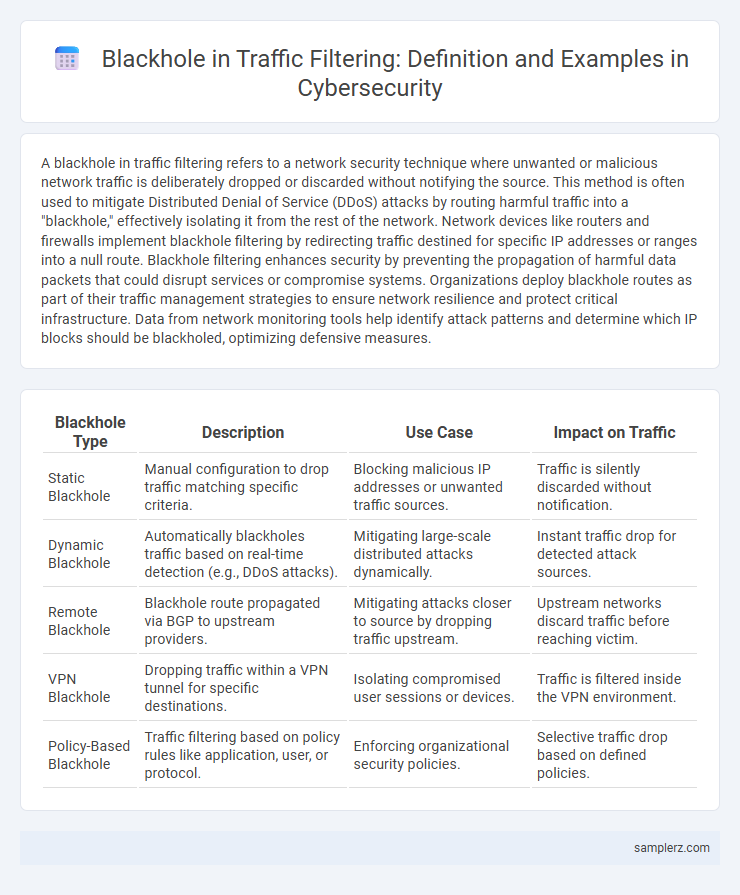
Table of Comparison
| Blackhole Type | Description | Use Case | Impact on Traffic |
|---|---|---|---|
| Static Blackhole | Manual configuration to drop traffic matching specific criteria. | Blocking malicious IP addresses or unwanted traffic sources. | Traffic is silently discarded without notification. |
| Dynamic Blackhole | Automatically blackholes traffic based on real-time detection (e.g., DDoS attacks). | Mitigating large-scale distributed attacks dynamically. | Instant traffic drop for detected attack sources. |
| Remote Blackhole | Blackhole route propagated via BGP to upstream providers. | Mitigating attacks closer to source by dropping traffic upstream. | Upstream networks discard traffic before reaching victim. |
| VPN Blackhole | Dropping traffic within a VPN tunnel for specific destinations. | Isolating compromised user sessions or devices. | Traffic is filtered inside the VPN environment. |
| Policy-Based Blackhole | Traffic filtering based on policy rules like application, user, or protocol. | Enforcing organizational security policies. | Selective traffic drop based on defined policies. |
Introduction to Blackhole Filtering in Network Security
Blackhole filtering in network security refers to the practice of routing unwanted or malicious traffic into a null route or "black hole," effectively dropping it to prevent network congestion and protect resources. This technique is commonly used to mitigate Distributed Denial-of-Service (DDoS) attacks by directing attack traffic away from critical infrastructure. Efficient blackhole filtering relies on access control lists (ACLs) and routing policies to identify and isolate harmful packets before they reach sensitive network segments.
How Blackhole Filtering Works in Traffic Management
Blackhole filtering works in traffic management by directing unwanted or malicious data packets to a null route, effectively isolating them from the network and preventing further propagation. This technique relies on routing configurations that discard traffic destined for specific IP addresses or ranges associated with attack sources, such as DDoS attacks. By employing blackhole filtering, network administrators can maintain service availability and reduce the impact of overwhelming or harmful traffic on critical infrastructure.
Common Scenarios for Blackhole Deployment
Common scenarios for blackhole deployment in traffic filtering include mitigating Distributed Denial of Service (DDoS) attacks by diverting malicious traffic away from targeted servers to preserve network performance. Service providers often implement blackhole routing to isolate compromised IP addresses involved in network scanning or spamming activities. Enterprises also use blackholes to block traffic from suspicious sources identified through threat intelligence feeds, enhancing overall network security posture.
Blackhole Filtering vs Traditional Firewalls
Blackhole filtering directs malicious or unwanted traffic into a non-routable IP address, effectively dropping packets without inspection, which reduces the load on network devices. Traditional firewalls analyze packets based on predefined rules and inspect traffic for threats, providing granular control but requiring more processing resources. Blackhole filtering excels in mitigating volumetric DDoS attacks by quickly discarding traffic, whereas firewalls offer detailed security policies and monitoring capabilities.
Real-World Example: Mitigating DDoS Attacks with Blackholing
Blackholing is widely used by major ISPs like Cloudflare and Akamai to mitigate large-scale DDoS attacks by diverting malicious traffic into a null route, effectively nullifying the threat without impacting legitimate users. During the 2018 GitHub DDoS attack, over 1.35 Tbps of traffic was directed into blackholes, rapidly neutralizing the attack's impact and maintaining service availability. This technique allows network administrators to protect critical infrastructure by absorbing and discarding harmful traffic before it reaches targeted servers.
Step-by-Step Example of Blackhole Implementation
In traffic filtering, blackhole implementation begins by identifying malicious or unwanted IP addresses generating excessive traffic. Network administrators configure routers or firewalls to route traffic destined for these IPs to a null interface or discard route, effectively dropping packets without processing. Continuous monitoring and updating of blackhole filters ensure efficient mitigation of distributed denial-of-service (DDoS) attacks and unwanted traffic floods.
Pros and Cons of Using Blackhole Filtering
Blackhole filtering in network security involves directing unwanted traffic to a null route, effectively dropping malicious packets before they can impact critical infrastructure. This method significantly reduces the load on network resources and mitigates the risk of distributed denial-of-service (DDoS) attacks by isolating harmful traffic. However, blackhole filtering can inadvertently block legitimate traffic if misconfigured, potentially disrupting services and causing network downtime.
Blackhole Filtering in Cloud Environments
Blackhole filtering in cloud environments effectively routes malicious or unwanted traffic to a virtual null interface, preventing it from reaching critical infrastructure and reducing the risk of Distributed Denial of Service (DDoS) attacks. This technique leverages cloud provider capabilities such as AWS Route 53 or Azure Firewall to dynamically isolate and drop suspicious packets at the network edge. By implementing blackhole filtering, organizations can maintain high availability and protect cloud-hosted applications from volumetric traffic floods without impacting legitimate users.
Risks and Challenges Associated with Blackholing
Blackholing in traffic filtering can inadvertently block legitimate traffic, causing service disruptions and potential loss of critical communications. This technique risks creating network blind spots, hindering the ability to monitor and respond to evolving cyber threats effectively. Managing false positives and ensuring precise targeting is crucial to avoid collateral damage and maintain overall network integrity.
Best Practices for Effective Blackhole Filtering
Effective blackhole filtering in network security involves directing unwanted or malicious traffic to a null route to prevent network congestion and potential outages. Implementing precise criteria for traffic identification, such as IP addresses or protocols associated with attacks, ensures minimal disruption to legitimate traffic. Regular monitoring and updating blackhole rules enhance protection against evolving threats while maintaining optimal network performance.
example of blackhole in traffic filtering Infographic
 samplerz.com
samplerz.com