Pharming is a cyberattack that targets the Domain Name System (DNS) to redirect users from legitimate websites to fraudulent ones without their knowledge. Attackers manipulate DNS records, often by poisoning the DNS cache on a server or compromising the DNS server itself, causing the DNS resolver to return an incorrect IP address. This manipulated IP address directs users to a malicious website designed to steal sensitive information such as login credentials and financial data. A common example of pharming involves an attacker poisoning a DNS server's cache, causing all requests for a legitimate bank's website to resolve to the IP address of a fake site controlled by the attacker. Users attempting to visit their bank's website are unknowingly redirected to this fraudulent site, where attackers can capture usernames and passwords. This type of attack exploits the trust users place in DNS, highlighting the critical importance of DNS security measures such as DNSSEC to verify the authenticity of DNS responses.
Table of Comparison
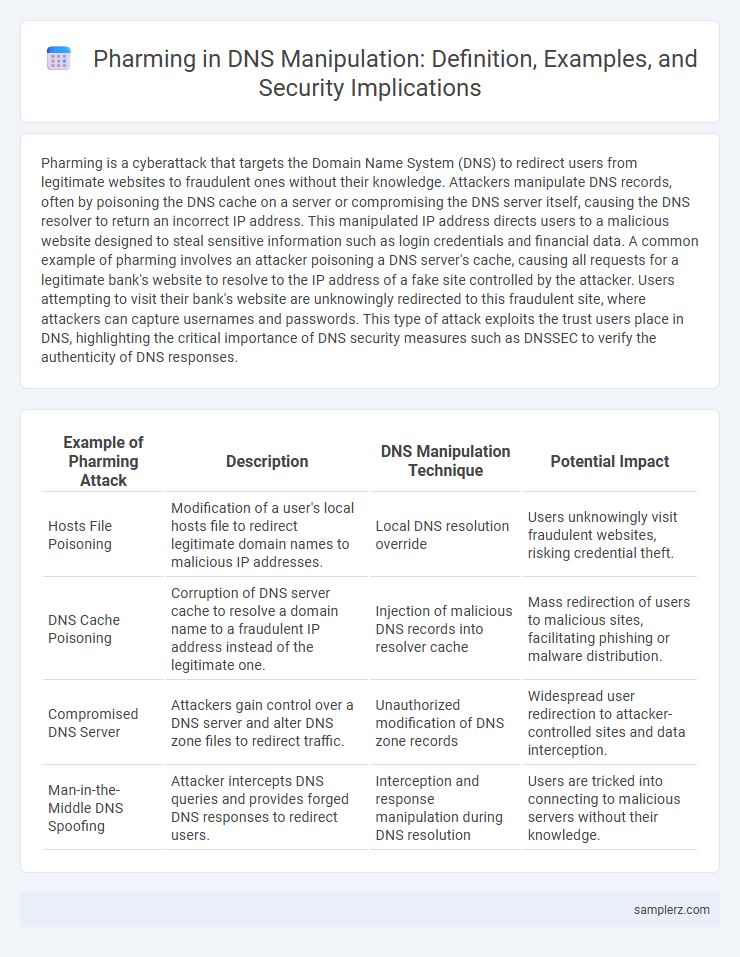
| Example of Pharming Attack | Description | DNS Manipulation Technique | Potential Impact |
|---|---|---|---|
| Hosts File Poisoning | Modification of a user's local hosts file to redirect legitimate domain names to malicious IP addresses. | Local DNS resolution override | Users unknowingly visit fraudulent websites, risking credential theft. |
| DNS Cache Poisoning | Corruption of DNS server cache to resolve a domain name to a fraudulent IP address instead of the legitimate one. | Injection of malicious DNS records into resolver cache | Mass redirection of users to malicious sites, facilitating phishing or malware distribution. |
| Compromised DNS Server | Attackers gain control over a DNS server and alter DNS zone files to redirect traffic. | Unauthorized modification of DNS zone records | Widespread user redirection to attacker-controlled sites and data interception. |
| Man-in-the-Middle DNS Spoofing | Attacker intercepts DNS queries and provides forged DNS responses to redirect users. | Interception and response manipulation during DNS resolution | Users are tricked into connecting to malicious servers without their knowledge. |
Understanding Pharming: A DNS Manipulation Threat
Pharming is a cyberattack that redirects users from legitimate websites to fraudulent ones by manipulating DNS servers or cache, often through DNS poisoning. Attackers exploit vulnerabilities in DNS software or compromise DNS resolvers to reroute traffic without the user's knowledge, leading to credential theft or malware installation. Understanding this threat is crucial for implementing DNSSEC and vigilant network monitoring to prevent unauthorized DNS redirection.
How Pharming Works in DNS Attacks
Pharming in DNS attacks works by redirecting users from legitimate websites to malicious ones without their knowledge. Attackers manipulate DNS cache or compromise DNS servers to alter IP address mappings, causing the victim's browser to resolve a trusted domain to a fraudulent IP address. This technique enables cybercriminals to steal sensitive information such as login credentials and financial data by exploiting the DNS resolution process.
Real-World Examples of DNS-based Pharming
Attackers manipulated the DNS settings of a major ISP in 2018, redirecting users to fraudulent banking sites mirroring legitimate ones and capturing login credentials. Pharming incidents targeting pharmaceutical domains have also diverted customers to counterfeit drug marketplaces, leading to significant financial and health risks. The 2020 COVID-19 pandemic saw a surge in pharming campaigns exploiting DNS vulnerabilities, redirecting users to fake health information portals to steal personal data.
Case Study: Compromised DNS Servers and User Redirection
Compromised DNS servers in pharming attacks redirect users to fraudulent websites by altering DNS records, enabling attackers to harvest sensitive data such as login credentials and financial information. In a notable case study, hackers manipulated DNS configurations to reroute traffic from legitimate banking sites to counterfeit domains, resulting in widespread data breaches and financial losses. Continuous monitoring of DNS integrity and implementation of DNSSEC protocols are critical to prevent exploitation through such DNS manipulation.
Notorious Pharming Incidents in Recent Years
Notorious pharming incidents include the 2020 attack on a major financial website where hackers manipulated DNS settings to redirect users to fraudulent websites, resulting in significant financial losses. The 2018 incident involving a global e-commerce platform saw cybercriminals exploit DNS cache poisoning to steal sensitive customer data. These cases highlight the critical vulnerabilities in DNS infrastructure that enable pharming attacks to compromise user trust and security.
Detecting DNS Manipulation in Pharming Schemes
Detecting DNS manipulation in pharming schemes involves monitoring DNS query patterns for unusual redirect behavior and verifying IP address consistency for known domains using DNSSEC validation. Employing anomaly detection tools to analyze sudden changes in DNS records or unexpectedly high traffic to unfamiliar IP addresses helps identify potential pharming attacks. Regular audits of DNS server configurations and implementing real-time alerts for unauthorized DNS record modifications enhance defense against manipulated DNS entries.
Impact of Pharming Attacks on Individuals and Organizations
Pharming attacks manipulate DNS settings to redirect users from legitimate websites to fraudulent ones, leading to unauthorized data access and financial loss. Individuals may unknowingly provide sensitive information such as passwords or credit card details, resulting in identity theft and compromised personal security. Organizations face reputational damage, operational disruption, and potential legal liabilities due to data breaches and customer trust erosion.
Common Techniques Used to Execute DNS Pharming
DNS pharming commonly exploits cache poisoning, where attackers inject malicious IP addresses into a DNS server's cache, redirecting users to fraudulent websites without their knowledge. Another frequent technique involves compromising a victim's host file, altering domain-to-IP mappings locally to intercept sensitive data. Attackers also utilize rogue DNS servers configured to provide false DNS responses, facilitating widespread redirection and data theft.
Preventive Measures Against DNS Pharming
Implementing DNSSEC (Domain Name System Security Extensions) significantly mitigates the risk of DNS pharming by ensuring DNS responses are authenticated and tamper-proof. Employing strong firewall rules and regularly updating DNS server software limits vulnerabilities that attackers exploit for DNS manipulation. Continuous monitoring of DNS traffic and user awareness training further enhance defenses against pharming threats by quickly detecting and responding to suspicious redirections.
Strengthening DNS Security to Thwart Pharming
Implementing DNS Security Extensions (DNSSEC) effectively prevents pharming attacks by authenticating DNS data and ensuring its integrity. Configuring DNS resolvers to validate DNSSEC signatures deters attackers from redirecting users to fraudulent websites. Continuous monitoring for unauthorized DNS changes and employing DNS filtering tools further strengthen defenses against DNS manipulation-based pharming.
example of pharming in DNS manipulation Infographic
 samplerz.com
samplerz.com