Cache poisoning in DNS occurs when an attacker injects false information into a DNS resolver's cache, causing it to return an incorrect IP address for a domain name. This attack exploits vulnerabilities in the DNS protocol, allowing malicious actors to redirect users to fraudulent websites without their knowledge. A common example involves an attacker sending forged DNS responses to a resolver, poisoning its cache with a fake record that points a legitimate domain to a malicious server. The impact of DNS cache poisoning can be severe, facilitating phishing attacks, malware distribution, or data interception. Organizations may experience compromised user trust, data breaches, and financial loss due to redirected traffic. Defenses against cache poisoning include implementing DNSSEC, using randomized source ports, and regularly flushing DNS cache to limit the lifespan of potentially corrupted entries.
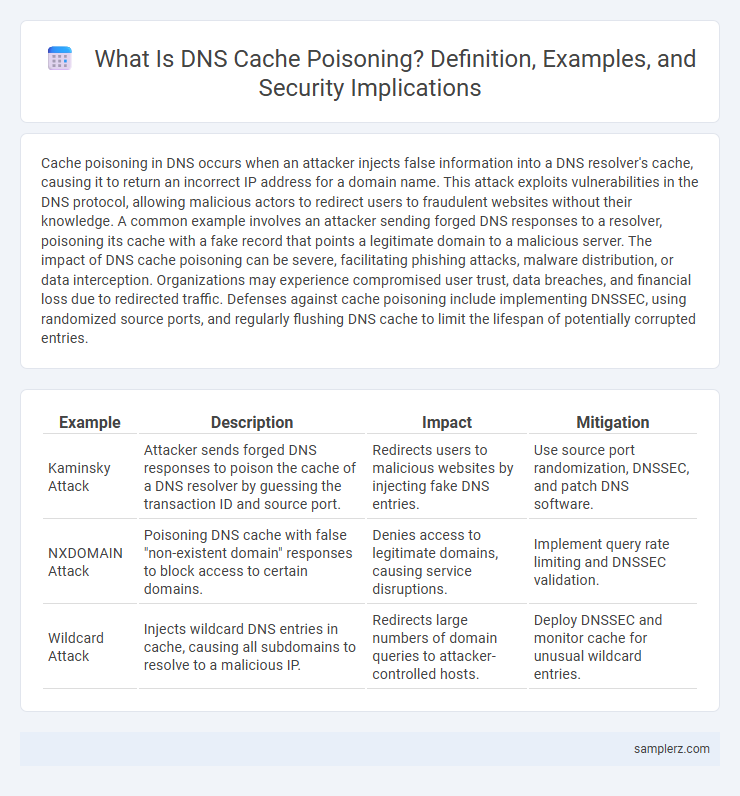
Table of Comparison
| Example | Description | Impact | Mitigation |
|---|---|---|---|
| Kaminsky Attack | Attacker sends forged DNS responses to poison the cache of a DNS resolver by guessing the transaction ID and source port. | Redirects users to malicious websites by injecting fake DNS entries. | Use source port randomization, DNSSEC, and patch DNS software. |
| NXDOMAIN Attack | Poisoning DNS cache with false "non-existent domain" responses to block access to certain domains. | Denies access to legitimate domains, causing service disruptions. | Implement query rate limiting and DNSSEC validation. |
| Wildcard Attack | Injects wildcard DNS entries in cache, causing all subdomains to resolve to a malicious IP. | Redirects large numbers of domain queries to attacker-controlled hosts. | Deploy DNSSEC and monitor cache for unusual wildcard entries. |
Understanding DNS Cache Poisoning
DNS cache poisoning occurs when attackers inject false information into a DNS resolver's cache, redirecting users to malicious websites. By exploiting vulnerabilities in DNS query responses, attackers can manipulate cached records to serve incorrect IP addresses, facilitating phishing, malware distribution, or traffic interception. Understanding DNS cache poisoning is crucial for implementing security measures such as DNSSEC to validate DNS responses and protect against cache manipulation attacks.
Common Methods of DNS Cache Poisoning
DNS cache poisoning commonly exploits vulnerabilities through methods such as DNS spoofing, where attackers inject false DNS responses into the cache to redirect users to malicious sites. Another prevalent technique involves exploiting predictable transaction IDs and source ports, allowing attackers to masquerade as legitimate DNS servers. These methods compromise DNS integrity, leading to serious security risks like phishing, malware distribution, and data interception.
Real-World DNS Cache Poisoning Incidents
In 2008, the Kaminsky DNS cache poisoning vulnerability exposed millions of DNS servers worldwide, allowing attackers to inject false IP addresses into DNS caches. The attack manipulated DNS queries, redirecting users to malicious websites without their knowledge, resulting in widespread phishing and malware distribution. This incident highlighted critical flaws in DNS security protocols, prompting urgent deployment of DNSSEC to authenticate DNS responses and prevent cache poisoning.
Example: Kaminsky DNS Cache Poisoning Attack
The Kaminsky DNS Cache Poisoning Attack exploited a flaw in DNS protocol by injecting false DNS responses to redirect users to malicious sites. Attacker sends multiple forged responses with varying transaction IDs to a DNS resolver before it receives the legitimate reply, poisoning the cache. This attack demonstrates the critical risk of DNS cache poisoning in compromising internet security and the need for robust validation mechanisms such as DNSSEC.
Anatomy of a DNS Cache Poisoning Example
DNS cache poisoning occurs when an attacker injects fraudulent DNS data into a resolver's cache, redirecting users to malicious sites. In a typical example, the attacker sends forged responses with false IP addresses before the legitimate DNS server replies, exploiting predictable transaction IDs and source ports. This manipulation corrupts the DNS cache, causing subsequent user queries to resolve to attacker-controlled IPs, leading to phishing or malware distribution.
Step-by-Step DNS Cache Poisoning Scenario
DNS cache poisoning occurs when an attacker introduces false DNS records into a resolver's cache, redirecting users to malicious sites. The attack begins with the attacker sending a forged DNS response containing counterfeit IP addresses before the legitimate response arrives, exploiting the resolver's lack of strict validation. This manipulated entry remains cached, causing subsequent user requests to resolve to the attacker-controlled IP, enabling phishing, malware distribution, or data interception.
Exploiting Vulnerabilities in DNS Resolver Caches
Cache poisoning in DNS involves injecting false information into a DNS resolver's cache, causing it to return incorrect IP addresses. Attackers exploit vulnerabilities such as predictable transaction IDs or lack of source port randomization, enabling them to redirect users to malicious websites. This technique undermines the integrity of DNS resolution, leading to phishing, malware distribution, or man-in-the-middle attacks.
Impact of DNS Cache Poisoning Attacks
DNS cache poisoning attacks undermine the integrity of DNS responses by injecting malicious IP addresses into the cache, redirecting users to fraudulent websites. This manipulation can lead to widespread data theft, phishing, and malware distribution, significantly compromising network security. Organizations often experience service interruptions and loss of user trust, resulting in financial damage and reputational harm.
Detection Techniques for DNS Cache Poisoning
Detecting DNS cache poisoning involves monitoring DNS traffic for anomalous patterns such as unexpected or duplicate DNS responses and mismatched transaction IDs. Techniques like DNSSEC validation and anomaly-based intrusion detection systems (IDS) enhance detection by verifying DNS record authenticity and identifying unusual query-response behavior. Real-time log analysis and correlation with threat intelligence feeds also provide effective detection of cache poisoning attempts.
Preventive Measures Against DNS Cache Poisoning
Effective preventive measures against DNS cache poisoning include implementing DNSSEC (Domain Name System Security Extensions) to authenticate DNS data integrity and origin, thereby preventing attackers from injecting malicious records. Regularly updating DNS software and applying patches close known vulnerabilities, while configuring DNS resolvers to use random source ports and query IDs enhances resistance against spoofing attempts. Employing split-horizon DNS and monitoring DNS traffic patterns can also detect and mitigate cache poisoning threats proactively.
example of cache poisoning in DNS Infographic
 samplerz.com
samplerz.com