Wardriving involves searching for Wi-Fi networks by moving through a specific area with a device such as a laptop or smartphone equipped with wireless network detection software. Attackers use wardriving to identify vulnerable Wi-Fi access points that lack strong encryption or proper security settings. This technique enables cybercriminals to map out networks that can be targeted for unauthorized access or data theft. During wardriving, tools like NetStumbler or Kismet gather information about SSIDs, signal strength, and security protocols of available wireless networks. The data collected helps identify unsecured or poorly secured Wi-Fi hotspots, often exploiting networks using outdated WEP encryption or no encryption at all. Effective countermeasures involve using WPA3 encryption, disabling SSID broadcasting, and implementing strong password policies.
Table of Comparison
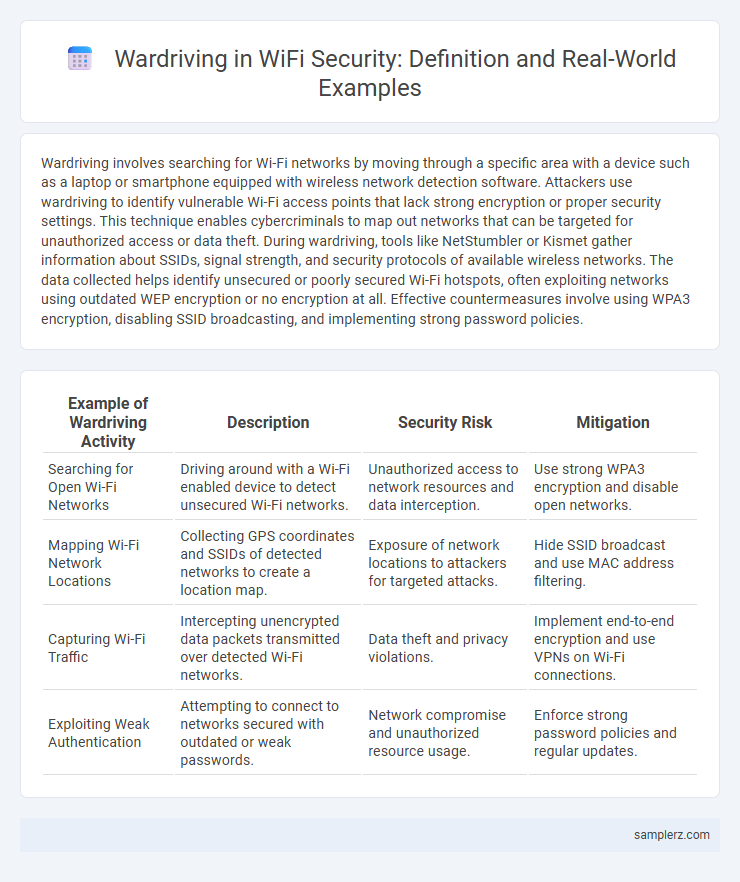
| Example of Wardriving Activity | Description | Security Risk | Mitigation |
|---|---|---|---|
| Searching for Open Wi-Fi Networks | Driving around with a Wi-Fi enabled device to detect unsecured Wi-Fi networks. | Unauthorized access to network resources and data interception. | Use strong WPA3 encryption and disable open networks. |
| Mapping Wi-Fi Network Locations | Collecting GPS coordinates and SSIDs of detected networks to create a location map. | Exposure of network locations to attackers for targeted attacks. | Hide SSID broadcast and use MAC address filtering. |
| Capturing Wi-Fi Traffic | Intercepting unencrypted data packets transmitted over detected Wi-Fi networks. | Data theft and privacy violations. | Implement end-to-end encryption and use VPNs on Wi-Fi connections. |
| Exploiting Weak Authentication | Attempting to connect to networks secured with outdated or weak passwords. | Network compromise and unauthorized resource usage. | Enforce strong password policies and regular updates. |
What is Wardriving?
Wardriving involves searching for Wi-Fi networks by moving through a specific area with a wireless-enabled device, often a laptop or smartphone, to identify unsecured or poorly protected networks. Hackers use this technique to detect vulnerabilities in wireless networks that can be exploited for unauthorized access or data theft. Effective security measures such as strong encryption protocols (WPA3) and disabling SSID broadcasting help prevent wardriving attacks.
How Wardriving Exploits WiFi Networks
Wardriving exploits WiFi networks by scanning for unsecured or poorly secured wireless access points using GPS-enabled devices, allowing attackers to identify vulnerable hotspots. By leveraging weak encryption protocols such as WEP or default SSIDs, cybercriminals can gain unauthorized access to network resources and intercept sensitive data. This technique poses significant security risks to both personal and enterprise wireless networks, emphasizing the need for robust encryption and strong authentication methods.
Common Tools Used in Wardriving
Common tools used in wardriving include WiFi scanning software such as NetStumbler, Kismet, and Aircrack-ng, which enable the detection of unsecured wireless networks. These tools capture network information like SSIDs, encryption types, and signal strength to map WiFi hotspots. Hardware components often involve laptops or smartphones equipped with high-gain antennas to increase the range and accuracy of network detection.
Real-World Examples of Wardriving Attacks
Wardriving attacks often exploit unsecured or poorly protected Wi-Fi networks in urban areas, as seen in incidents like the 2017 data breach of a retail chain where attackers accessed customer data through unencrypted wireless access points. In another case, hackers executed wardriving to locate vulnerable corporate Wi-Fi networks, enabling unauthorized entry into sensitive internal systems at a financial institution. These real-world examples underscore the critical importance of robust encryption protocols and continuous monitoring of wireless network security.
Signs Your WiFi Network May Have Been Targeted
Unusual network activity such as unexplained data spikes or sudden disconnects can indicate your WiFi network has been targeted in wardriving attacks. Discovery of unknown devices connected to your router or changes in router settings without user authorization often signal unauthorized access. Frequent WiFi dead spots or noticeable drops in performance may also suggest external efforts to intercept or manipulate your wireless signal.
Legal Implications of Wardriving
Wardriving involves the practice of searching for and mapping Wi-Fi networks while in motion, often using GPS devices combined with wireless network scanners. Legal implications arise since unauthorized access to networks during wardriving can violate laws such as the Computer Fraud and Abuse Act (CFAA) in the United States and data protection regulations in other jurisdictions. Penalties for illegal wardriving activities may include fines, criminal charges, and liability for damages caused by unauthorized intrusion or data interception.
Methods Hackers Use to Crack WiFi Passwords
Hackers employ wardriving by driving around with specialized software and WiFi adapters to identify unsecured or weakly secured networks. Techniques such as packet sniffing and capturing handshake data enable attackers to perform offline brute-force or dictionary attacks on WiFi passwords. Exploiting vulnerabilities in outdated encryption protocols like WEP and weak WPA/WPA2 keys remains a common method to crack network access.
Impact of Wardriving on Personal and Business Security
Wardriving exposes vulnerable Wi-Fi networks by mapping their locations, enabling attackers to intercept sensitive data or launch cyberattacks. Personal security risks include identity theft and unauthorized access to private information, while businesses face potential data breaches, financial loss, and reputational damage. The practice highlights the critical need for strong encryption protocols, secure passwords, and regular network monitoring.
Preventative Measures Against Wardriving
Implementing strong encryption protocols such as WPA3 on Wi-Fi networks significantly reduces vulnerabilities exploited during wardriving attacks. Regularly updating router firmware and disabling SSID broadcasting help obscure network visibility, making unauthorized access more difficult. Employing MAC address filtering and enabling network intrusion detection systems further enhance protection against malicious wardriving activities.
Best Practices for WiFi Security in a Wardriving World
Wardriving exploits unsecured WiFi networks by scanning for vulnerable access points while in motion, making robust encryption protocols like WPA3 essential for protection. Regularly updating router firmware and disabling SSID broadcasting minimize network visibility and reduce attack surfaces. Implementing strong, unique passwords and enabling network segmentation further safeguard sensitive data against unauthorized wardriving intrusions.
example of wardriving in wifi Infographic
 samplerz.com
samplerz.com