A bastion in security perimeter design serves as a fortified gateway or checkpoint that controls access between an external network and an internal secure environment. It acts as a shielded intermediary point, often implemented as a dedicated server or firewall, ensuring that only authorized users can enter the protected area. Bastions typically monitor incoming traffic, filter potential threats, and log access attempts to enhance overall perimeter defense. In perimeter security, the bastion host is strategically positioned to reduce the attack surface by limiting direct exposure of critical systems to external threats. This entity enforces strict access policies and may employ multi-factor authentication and intrusion detection systems to strengthen security controls. Data passing through a bastion is scrutinized continuously to detect anomalies and prevent unauthorized data breaches or cyber attacks.
Table of Comparison
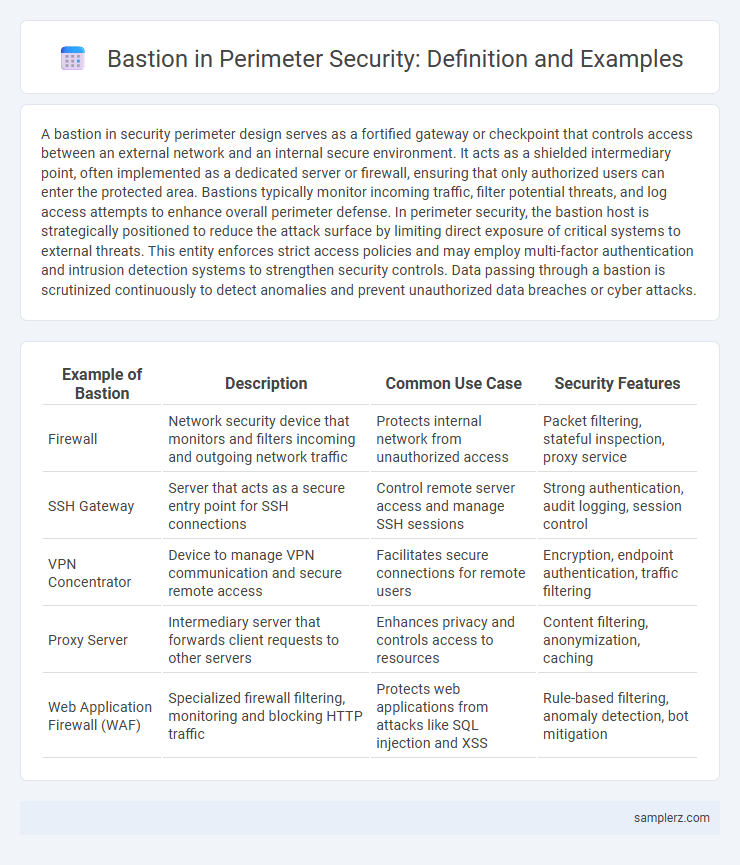
| Example of Bastion | Description | Common Use Case | Security Features |
|---|---|---|---|
| Firewall | Network security device that monitors and filters incoming and outgoing network traffic | Protects internal network from unauthorized access | Packet filtering, stateful inspection, proxy service |
| SSH Gateway | Server that acts as a secure entry point for SSH connections | Control remote server access and manage SSH sessions | Strong authentication, audit logging, session control |
| VPN Concentrator | Device to manage VPN communication and secure remote access | Facilitates secure connections for remote users | Encryption, endpoint authentication, traffic filtering |
| Proxy Server | Intermediary server that forwards client requests to other servers | Enhances privacy and controls access to resources | Content filtering, anonymization, caching |
| Web Application Firewall (WAF) | Specialized firewall filtering, monitoring and blocking HTTP traffic | Protects web applications from attacks like SQL injection and XSS | Rule-based filtering, anomaly detection, bot mitigation |
Introduction to Bastions in Perimeter Security
A bastion host serves as a critical security gateway in perimeter defense, providing controlled access to an internal network while isolating external threats. By limiting direct exposure of sensitive resources, bastions enforce strict authentication and monitoring, reducing the attack surface. Common examples include secure jump servers and proxy systems that regulate inbound and outbound traffic to enhance perimeter security.
Key Functions of a Bastion Host
A bastion host acts as a critical security gateway within a network perimeter, controlling and monitoring access to internal systems. Key functions include regulating inbound and outbound traffic through strict access control rules, logging and auditing all connection attempts for anomaly detection, and providing a hardened environment resistant to attacks. Its deployment ensures secure remote management by isolating the internal network from potential external threats.
Real-World Bastion Deployment Scenarios
A bastion host in perimeter security acts as a fortified gateway, typically deployed in a demilitarized zone (DMZ) to control external access to internal networks. Real-world deployment scenarios include cloud environments where a bastion server provides secure SSH or RDP access to virtual machines, reducing attack surfaces by tightly regulating and logging all administrative connections. Enterprises often pair bastion hosts with multi-factor authentication (MFA) and strict access control policies to enhance perimeter defenses and prevent lateral movement by attackers.
Architectural Role of Bastions in Network Perimeters
Bastions serve as fortified gateways within network perimeters, designed to withstand attacks and control traffic between untrusted external networks and internal systems. Their architectural role includes hosting hardened servers, such as firewalls or proxy servers, that inspect and filter incoming and outgoing data to enforce security policies. By isolating critical resources and minimizing direct exposure, bastions reduce the attack surface and enhance overall perimeter defense strategies.
Example: Bastion Host Protecting Corporate Servers
A bastion host acts as a fortified gateway between untrusted external networks and internal corporate servers, minimizing attack surfaces by strictly controlling access. Positioned in the network perimeter, it enforces stringent authentication and monitoring, ensuring only authorized traffic reaches sensitive resources. This security strategy significantly reduces vulnerabilities and mitigates risks associated with direct server exposure.
Configuring a Cloud-Based Bastion Instance
Configuring a cloud-based bastion instance involves deploying a hardened virtual machine within the network perimeter, specifically designed to control and monitor access to private resources. Key configurations include enforcing strict access controls with multi-factor authentication, setting up session logging for audit trails, and applying network security groups or firewall rules to restrict inbound connections to specified IP ranges. Properly implemented, a cloud-based bastion serves as a secure gateway, mitigating exposure of critical infrastructure while enabling safe administrative access.
Case Study: Bastion Use in Multi-Tier Architectures
In multi-tier architectures, bastion hosts serve as controlled entry points to enhance perimeter security by isolating and managing access to sensitive internal systems. A case study highlights how a bastion in a financial services network facilitated secure SSH access to backend servers, minimizing attack surfaces and preventing lateral movement. Configurations typically involve hardened operating systems, strict authentication mechanisms, and logging for auditability, exemplifying best practices in layered defense strategies.
Best Practices for Bastion Host Security
Deploy bastion hosts in a secure perimeter to control and monitor access to critical network segments, enforcing strict access policies and multi-factor authentication. Regularly update and patch the bastion host operating system and software to mitigate vulnerabilities, while restricting access using IP whitelisting and limiting user permissions to the minimum necessary. Enable detailed logging and continuous monitoring to detect unauthorized access attempts and ensure quick incident response.
Common Threats Mitigated by Bastions
Bastions in perimeter security effectively mitigate common threats such as unauthorized access, malware infiltration, and denial-of-service (DoS) attacks by acting as fortified gateways that monitor and control incoming traffic. They enforce strict authentication protocols and provide an additional layer of defense against external attackers targeting network entry points. By isolating sensitive systems, bastions also reduce the risk of lateral movement within the network during security breaches.
Future Trends in Bastion-Based Perimeter Defense
Future trends in bastion-based perimeter defense emphasize the integration of zero trust principles, enhancing identity verification and micro-segmentation to minimize attack surfaces. Machine learning-driven anomaly detection improves real-time threat identification at bastion hosts, proactively countering advanced persistent threats. Cloud-native bastion deployments enable scalable, flexible perimeter security, aligning with hybrid and multi-cloud environments to ensure consistent policy enforcement.
example of bastion in perimeter Infographic
 samplerz.com
samplerz.com