A black bag operation in security refers to a covert mission involving clandestine entry into a property to gather intelligence or obtain sensitive data without the owner's knowledge. These operations often employ advanced tools such as lock picks, surveillance devices, and digital extraction equipment to bypass security systems. Intelligence agencies and law enforcement units conduct black bag operations to intercept communications, plant bugs, or acquire physical or digital evidence critical for national security or criminal investigations. In practice, a typical black bag operation might involve breaking into an adversary's office to retrieve confidential documents or installing hidden cameras to monitor activities. These missions require meticulous planning to avoid detection and preserve operational secrecy. Data obtained during black bag missions must be securely handled and analyzed to support counterterrorism, espionage, or criminal prosecution efforts effectively.
Table of Comparison
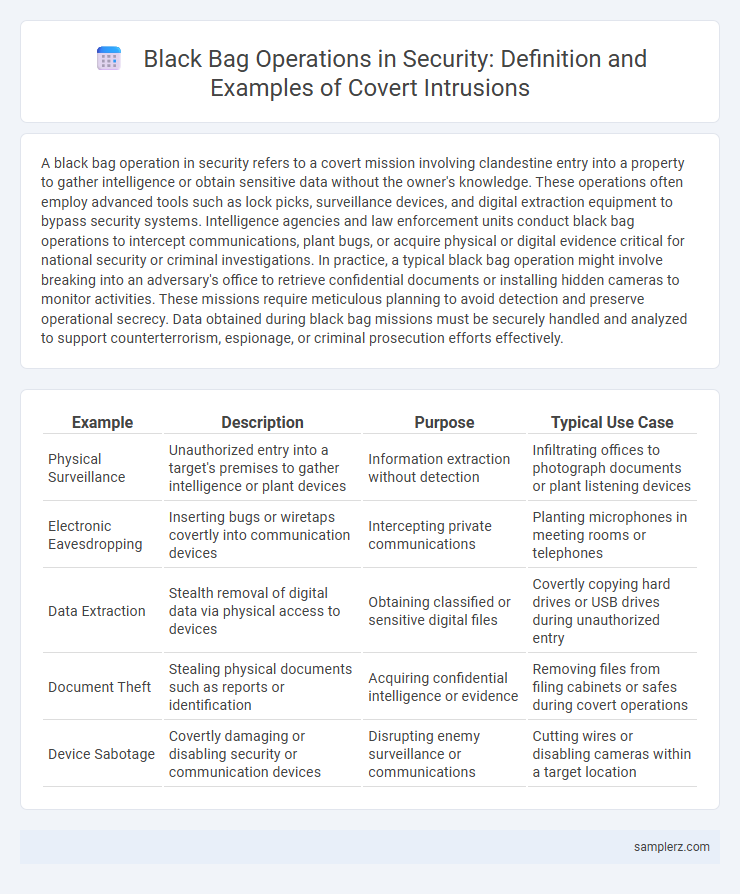
| Example | Description | Purpose | Typical Use Case |
|---|---|---|---|
| Physical Surveillance | Unauthorized entry into a target's premises to gather intelligence or plant devices | Information extraction without detection | Infiltrating offices to photograph documents or plant listening devices |
| Electronic Eavesdropping | Inserting bugs or wiretaps covertly into communication devices | Intercepting private communications | Planting microphones in meeting rooms or telephones |
| Data Extraction | Stealth removal of digital data via physical access to devices | Obtaining classified or sensitive digital files | Covertly copying hard drives or USB drives during unauthorized entry |
| Document Theft | Stealing physical documents such as reports or identification | Acquiring confidential intelligence or evidence | Removing files from filing cabinets or safes during covert operations |
| Device Sabotage | Covertly damaging or disabling security or communication devices | Disrupting enemy surveillance or communications | Cutting wires or disabling cameras within a target location |
Introduction to Black Bag Operations in Security
Black bag operations involve covert entry techniques used by security and intelligence agencies to gather evidence or conduct surveillance without the knowledge or consent of the target. These operations typically include lock picking, safe cracking, and electronic bugging to access sensitive information or monitor activities discreetly. Employed in counterterrorism and criminal investigations, black bag operations require meticulous planning and adherence to legal frameworks to ensure operational success and minimize detection.
Defining Black Bag Jobs in Covert Contexts
Black bag jobs in covert operations refer to clandestine activities involving unauthorized entry into premises to obtain information or materials without detection. These tasks often include surveillance, bugging, document theft, or installing covert listening devices, executed by intelligence or security agencies. The primary objective of black bag jobs is to gather critical intelligence while maintaining absolute secrecy and avoiding legal exposure.
Historical Examples of Black Bag Techniques
Historical examples of black bag techniques include covert entries used by the FBI during the 1970s COINTELPRO operations targeting political activists. These operations involved stealthy break-ins to gather intelligence, plant surveillance devices, and seize documents without warrants. Such black bag jobs exemplify clandestine tactics employed in security and intelligence to achieve objectives while minimizing detection.
Common Tools Used in Black Bag Operations
Common tools used in black bag operations include lock-picking sets for covert entry, concealed surveillance devices such as mini cameras and audio bugs, and electronic signal interceptors to capture communications discreetly. Operators often rely on advanced forensic kits to collect trace evidence without detection and portable data extraction devices for rapidly copying digital information. High-end disguises and tamper-proof storage containers are also essential to maintain operational security and conceal sensitive materials.
Entry Methods: How Agents Infiltrate Targets
Black bags in covert operations often utilize advanced lock-picking tools and electronic bypass devices to silently gain entry without leaving traceable damage. Agents employ techniques such as forced entry with precision tools, manipulation of security systems, and exploitation of architectural weaknesses to infiltrate high-security locations. The use of discreet entry methods ensures operational secrecy while maintaining the element of surprise during target infiltration.
Case Study: Famous Black Bag Operation Successes
The 1972 Watergate scandal serves as a quintessential example of a successful black bag operation, where covert entry into the Democratic National Committee headquarters enabled extensive surveillance that ultimately exposed political misconduct. Another notable case is the CIA's Operation CHAOS during the Vietnam War, which utilized clandestine surveillance and intelligence gathering to monitor dissident groups and foreign agents. These operations highlight the critical role of black bag techniques in obtaining actionable intelligence while maintaining operational secrecy.
Legal and Ethical Considerations of Black Bag Activities
Black bag operations, involving covert entry to gather intelligence, raise significant legal concerns under Fourth Amendment protections against unreasonable searches and seizures. Courts require strict judicial oversight, typically through validated warrants, to legitimize these activities and prevent unlawful surveillance or privacy violations. Ethically, agencies must balance national security interests with respect for civil liberties, ensuring transparency and accountability to avoid abuses of power.
Countermeasures Against Black Bag Intrusions
Countermeasures against black bag intrusions include advanced surveillance systems, biometric access controls, and encrypted communication channels to prevent unauthorized data extraction. Deploying tamper-evident seals and regular security audits enhances the detection of covert entry attempts during black bag operations. Integration of cyber threat intelligence with physical security protocols minimizes risks associated with clandestine break-ins targeting sensitive information.
Black Bag Tactics in the Digital Age
Black Bag tactics in the digital age involve covert operations such as surreptitious data extraction from secure networks, stealthy deployment of malware for intelligence gathering, and discreet interception of encrypted communications. Modern black bag operations leverage advanced cyber tools like zero-day exploits and hardware keyloggers to infiltrate target systems without detection. These techniques emphasize maintaining stealth while accessing critical digital assets, reflecting a shift from physical break-ins to sophisticated cyber intrusions.
Training and Skills Required for Black Bag Operatives
Black bag operatives require advanced training in lock-picking, electronic surveillance, and stealth tactics to execute covert entries without detection. Proficiency in situational awareness, secure communication, and rapid problem-solving is essential to adapt to dynamic environments during operations. Continuous skill development through live simulations and scenario-based exercises ensures operatives maintain high levels of precision and operational security.
example of black bag in covert operation Infographic
 samplerz.com
samplerz.com