A rootkit is a type of malicious software designed to gain unauthorized access to a computer system while hiding its presence to avoid detection. One well-known example of a rootkit is the Sony BMG rootkit scandal in 2005, where the rootkit was embedded in music CDs to prevent copying. This rootkit compromised users' systems by creating hidden files and processes that were difficult to detect with traditional antivirus software, exposing vulnerabilities in system security. Rootkits can manipulate system files, processes, and drivers to maintain control and avoid removal, often targeting operating system kernels. The Stuxnet rootkit, discovered in 2010, specifically targeted industrial control systems and showcased sophisticated techniques for stealth and persistence. Monitoring system behavior for unusual activity and using specialized rootkit detection tools are essential for identifying and mitigating threats posed by rootkits in secure environments.
Table of Comparison
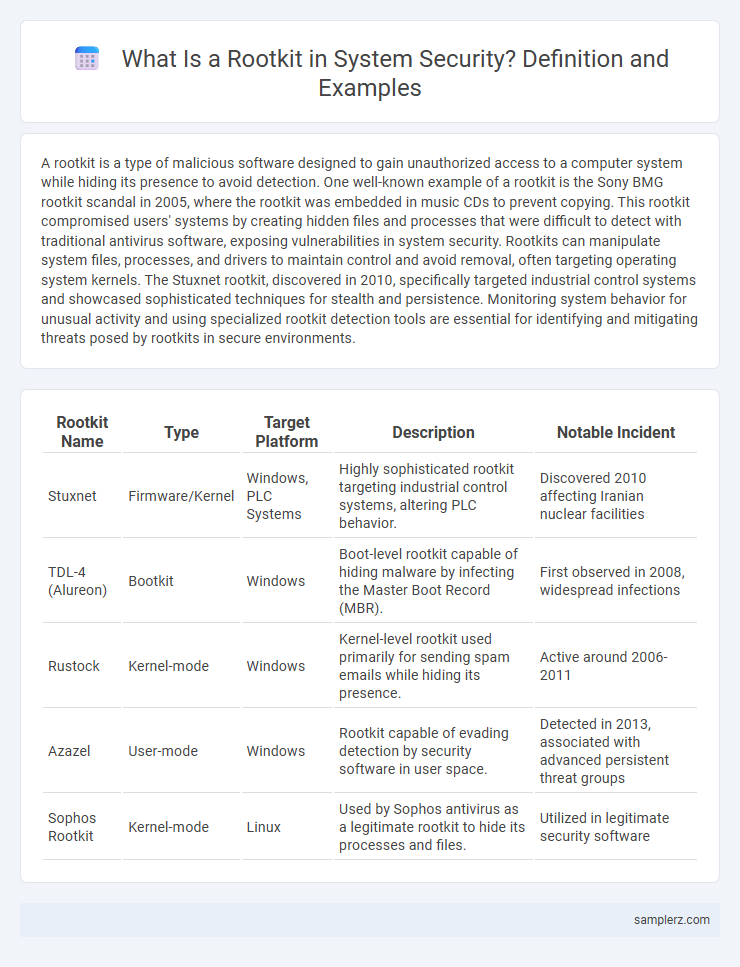
| Rootkit Name | Type | Target Platform | Description | Notable Incident |
|---|---|---|---|---|
| Stuxnet | Firmware/Kernel | Windows, PLC Systems | Highly sophisticated rootkit targeting industrial control systems, altering PLC behavior. | Discovered 2010 affecting Iranian nuclear facilities |
| TDL-4 (Alureon) | Bootkit | Windows | Boot-level rootkit capable of hiding malware by infecting the Master Boot Record (MBR). | First observed in 2008, widespread infections |
| Rustock | Kernel-mode | Windows | Kernel-level rootkit used primarily for sending spam emails while hiding its presence. | Active around 2006-2011 |
| Azazel | User-mode | Windows | Rootkit capable of evading detection by security software in user space. | Detected in 2013, associated with advanced persistent threat groups |
| Sophos Rootkit | Kernel-mode | Linux | Used by Sophos antivirus as a legitimate rootkit to hide its processes and files. | Utilized in legitimate security software |
Introduction to Rootkits in System Security
Rootkits are sophisticated malware designed to gain unauthorized access and hide their presence within an operating system, often targeting kernel-level processes to maintain persistent control. Common examples include the Sony BMG rootkit, which concealed itself to prevent unauthorized copying, and the Stuxnet rootkit, used for industrial sabotage by manipulating system processes undetected. Effective rootkit detection requires advanced techniques such as behavioral analysis, kernel integrity checks, and real-time monitoring to mitigate their stealth capabilities in system security.
Historical Examples of Rootkits
The 2005 Sony BMG rootkit scandal revealed how rootkits can be embedded in consumer software to evade detection and control user systems covertly. The Stuxnet worm, discovered in 2010, utilized rootkit techniques to hide its malicious code within industrial control systems, marking a significant evolution in cyberwarfare tools. Another notable example, the Sony PlayStation 3 rootkit exploit in 2010, demonstrated how rootkits could be employed to bypass security measures in gaming consoles.
Notable Windows Rootkit Incidents
Notable Windows rootkit incidents include the Sony BMG copy protection scandal in 2005, where rootkits were covertly installed on users' systems, leading to serious security vulnerabilities and privacy concerns. The Rustock rootkit, active in the late 2000s, was one of the most prolific Windows botnets, using rootkit techniques to evade detection while distributing massive volumes of spam. Stuxnet, discovered in 2010, employed sophisticated rootkit components targeting Windows systems to sabotage industrial control systems, marking a significant evolution in cyber warfare tactics.
Famous Linux Rootkit Attacks
Famous Linux rootkit attacks include the "Adore" rootkit, which stealthily modifies system binaries and backdoors network services, compromising kernel integrity. The "Azazel" rootkit targets Linux systems by hooking system calls and hiding malicious processes, enabling persistent unauthorized access. These rootkits exploit kernel vulnerabilities to bypass security mechanisms, emphasizing the need for robust detection tools in Linux environments.
Firmware and Hardware Rootkits in the Wild
Firmware and hardware rootkits represent some of the most insidious security threats, embedding themselves into system components like BIOS, UEFI, or network cards to persist beyond OS reinstallations. Notorious examples include the LoJax firmware rootkit, which targets UEFI firmware to maintain stealthy control of compromised systems, and the BadUSB hardware rootkit that manipulates USB device firmware to inject malicious code. These rootkits exploit low-level firmware vulnerabilities, making detection extremely challenging and requiring specialized tools for firmware integrity verification.
High-Profile Rootkits: Sony BMG Scandal
The Sony BMG scandal exposed a high-profile rootkit embedded in millions of music CDs to enforce digital rights management, which covertly installed hidden software on users' computers. This rootkit compromised system security by hiding processes and files, making detection and removal extremely difficult while creating vulnerabilities for malware exploitation. The incident highlighted significant risks associated with stealthy rootkits in commercial software and spurred broader awareness of rootkit threats in cybersecurity.
Advanced Persistent Threats Leveraging Rootkits
Advanced Persistent Threats (APTs) frequently leverage rootkits such as Stuxnet and Turla to maintain covert, long-term access to targeted systems, enabling evasion of traditional detection methods. These rootkits manipulate kernel-level processes to hide malicious activities, making remediation complex and necessitating advanced forensic analysis. Effective defense requires continuous monitoring with behavior-based detection technologies that identify anomalies indicative of rootkit presence within critical infrastructure environments.
Rootkit Detection Failures: Real-World Cases
Rootkit detection failures have been documented in cases such as the Sony BMG DRM scandal, where a rootkit buried itself deep in Windows systems, evading initial security tools. The Stuxnet worm also demonstrated sophisticated rootkit techniques by hiding its presence within industrial control systems, avoiding detection for months. These real-world cases highlight the challenges in identifying stealthy rootkits embedded at kernel levels, emphasizing the need for advanced heuristic and behavior-based detection methods.
Rootkit Use in Malware Campaigns
Rootkits like Sony BMG's Extended Copy Protection (XCP) have demonstrated how stealthy code can persist undetected by embedding deeply into operating system components. In malware campaigns, rootkits enable hackers to maintain prolonged access by hiding processes, files, and network connections from security tools. This covert control complicates threat detection and remediation, often leading to significant data breaches and system compromise.
Lessons Learned from Rootkit Exploits
Rootkit exploits, such as the infamous Sony BMG rootkit incident, demonstrated the critical need for rigorous system integrity verification and transparent software practices. These exploits revealed how stealthy kernel-level access can undermine security, emphasizing the importance of continuous monitoring and timely patch management. Organizations learned that proactive detection mechanisms and user education are essential to mitigate the risks posed by advanced persistent threats like rootkits.
example of rootkit in system Infographic
 samplerz.com
samplerz.com