Cryptolocker is a type of ransomware that targets servers by encrypting critical files and demanding a ransom for their decryption. This malware often infiltrates servers through phishing emails or compromised Remote Desktop Protocol (RDP) connections, leading to significant data loss if backups are not maintained. Infected servers exhibit locked files with extensions changed, accompanied by ransom notes demanding payment in cryptocurrency. Organizations facing Cryptolocker attacks witness disruptions in business operations and potential exposure of sensitive data. Effective mitigation strategies include regular data backups, stringent access controls, and deployment of advanced endpoint protection. Monitoring network traffic for unusual activities can help detect early signs of Cryptolocker infection on servers.
Table of Comparison
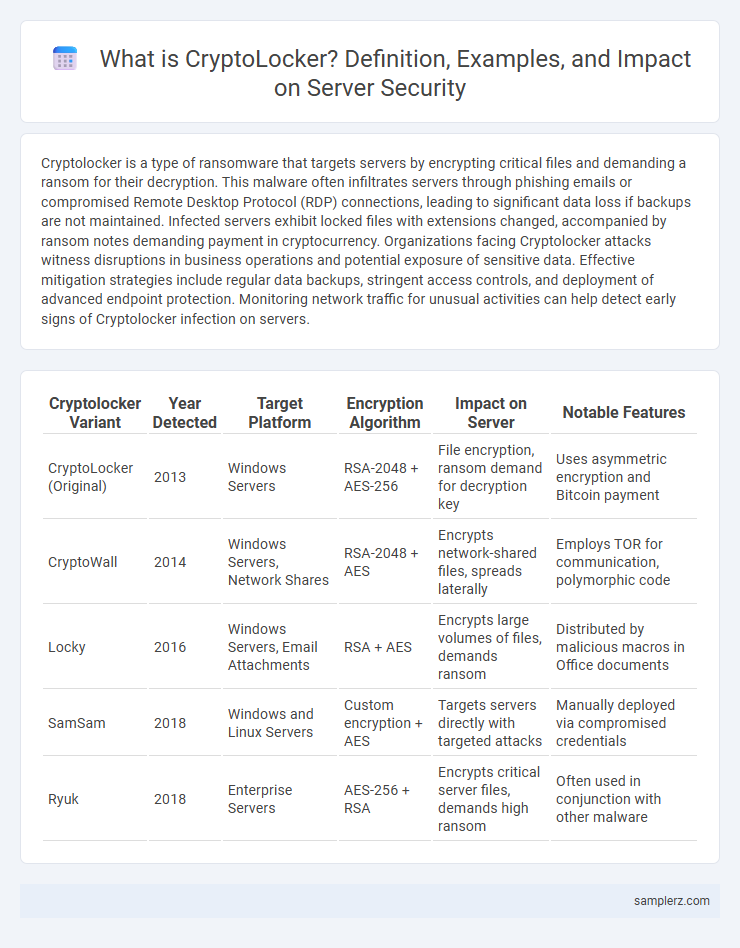
| Cryptolocker Variant | Year Detected | Target Platform | Encryption Algorithm | Impact on Server | Notable Features |
|---|---|---|---|---|---|
| CryptoLocker (Original) | 2013 | Windows Servers | RSA-2048 + AES-256 | File encryption, ransom demand for decryption key | Uses asymmetric encryption and Bitcoin payment |
| CryptoWall | 2014 | Windows Servers, Network Shares | RSA-2048 + AES | Encrypts network-shared files, spreads laterally | Employs TOR for communication, polymorphic code |
| Locky | 2016 | Windows Servers, Email Attachments | RSA + AES | Encrypts large volumes of files, demands ransom | Distributed by malicious macros in Office documents |
| SamSam | 2018 | Windows and Linux Servers | Custom encryption + AES | Targets servers directly with targeted attacks | Manually deployed via compromised credentials |
| Ryuk | 2018 | Enterprise Servers | AES-256 + RSA | Encrypts critical server files, demands high ransom | Often used in conjunction with other malware |
Overview of Cryptolocker Ransomware Attacks on Servers
Cryptolocker ransomware attacks on servers involve malicious encryption of critical data, rendering files inaccessible until a ransom is paid, often demanding payment in cryptocurrency like Bitcoin. These attacks typically exploit vulnerabilities in server operating systems or unpatched software, spreading rapidly across network shares and backup systems. Effective mitigation strategies include regular data backups, patch management, endpoint protection, and robust access controls to prevent unauthorized lateral movement.
How Cryptolocker Infiltrates Enterprise Server Environments
Cryptolocker infiltrates enterprise server environments primarily through phishing emails containing malicious attachments or links that exploit user vulnerabilities. Once executed, the ransomware leverages elevated permissions to propagate through network shares, encrypting critical server files and backups. Its ability to disguise communication with command-and-control servers enables persistent infiltration and complicates detection efforts.
Real-World Incidents of Cryptolocker Targeting Servers
Cryptolocker ransomware has notably targeted enterprise servers, encrypting critical data and demanding hefty ransoms to restore access, as seen in the 2013 attack on a major UK law firm that led to prolonged operational downtime. In another incident, healthcare organizations experienced severe disruptions when Cryptolocker infiltrated their backup servers, compromising patient records and forcing costly recovery efforts. These real-world attacks highlight the vulnerability of server infrastructures to ransomware and underscore the necessity for robust cybersecurity measures and regular data backups.
Common Vulnerabilities Exploited by Cryptolocker in Servers
Cryptolocker primarily exploits Remote Desktop Protocol (RDP) vulnerabilities, weak passwords, and unpatched operating systems on servers. It often gains access through phishing emails that deliver malicious attachments, enabling the ransomware to encrypt critical server files. Failure to secure RDP ports and neglecting timely software updates significantly increase the risk of Cryptolocker infection on enterprise servers.
Chain of Infection: Cryptolocker Lifecycle within Server Networks
Cryptolocker infiltrates server networks primarily through phishing emails containing malicious attachments or links, initiating the infection chain. Once executed, the ransomware encrypts critical files across connected servers and shared drives, spreading laterally by exploiting remote desktop protocols and unsecured network shares. The lifecycle culminates in ransom demand delivery and persistence mechanisms that disable security tools, ensuring ongoing encryption activity and preventing recovery without payment.
Impact Assessment: Consequences of a Cryptolocker Attack on Servers
A Cryptolocker attack on servers can lead to severe data encryption, rendering critical files inaccessible and causing significant operational downtime. The ransom demand often forces organizations to weigh the cost of payment against potential data loss and recovery expenses. Such attacks compromise data integrity, disrupt business continuity, and can result in financial losses reaching millions due to halted services and recovery efforts.
Case Study: Cryptolocker Outbreak in a Corporate Server Infrastructure
The Cryptolocker outbreak infiltrated a corporate server infrastructure by exploiting outdated remote desktop protocols and weak administrative passwords, rapidly encrypting essential business files and disrupting operations. Incident response teams isolated affected servers and restored data from segmented backups, emphasizing the necessity of multifactor authentication and real-time threat monitoring in corporate environments. Post-incident analysis revealed critical gaps in patch management and employee cybersecurity awareness, leading to enhanced network segmentation and aggressive phishing defense measures.
Incident Response Steps for Cryptolocker-Compromised Servers
Immediate isolation of the affected server from the network prevents further ransomware propagation and limits data loss. Incident response steps include preserving volatile evidence, identifying the ransomware variant through hash analysis, and initiating offline backups restoration to recover encrypted files. Coordinating with cybersecurity teams to update threat intelligence feeds and applying enhanced endpoint detection controls ensures containment and strengthens defenses against future Cryptolocker attacks.
Prevention Strategies Against Cryptolocker on Servers
Implement stringent access controls and regular patch management to prevent Cryptolocker infections on servers by minimizing vulnerabilities that ransomware exploits. Deploy advanced endpoint protection solutions with real-time threat detection and behavior-based analysis to identify and block malicious encryption activities before data is compromised. Implement frequent, isolated backups with secure, off-site storage to ensure rapid recovery from Cryptolocker attacks without paying ransom demands.
Lessons Learned from Cryptolocker Server Breaches
Cryptolocker ransomware attacks on servers highlight the critical necessity of implementing robust backup strategies, rigorous patch management, and real-time monitoring systems to detect anomalies early. Server breaches caused by Cryptolocker emphasize the importance of segmenting networks and enforcing strict access controls to limit the lateral movement of malware. Effective incident response plans and employee cybersecurity training are essential lessons learned to mitigate damage and accelerate recovery from server-based ransomware incidents.
example of cryptolocker in server Infographic
 samplerz.com
samplerz.com