Whaling in executive protection refers to highly targeted phishing attacks aimed at senior executives or high-profile individuals within an organization. Attackers often gather detailed personal and professional data about the executive to craft convincing emails or messages that appear legitimate. These messages may request sensitive information, authorize fund transfers, or install malware for unauthorized access. Data shows that whaling attacks exploit roles such as CEOs, CFOs, and other C-level executives due to their access to critical assets and decision-making power. Security teams implement advanced monitoring of email traffic and employ multi-factor authentication to mitigate risks associated with whaling. Incident response protocols focus on training executives to recognize suspicious communications and report potential threats immediately.
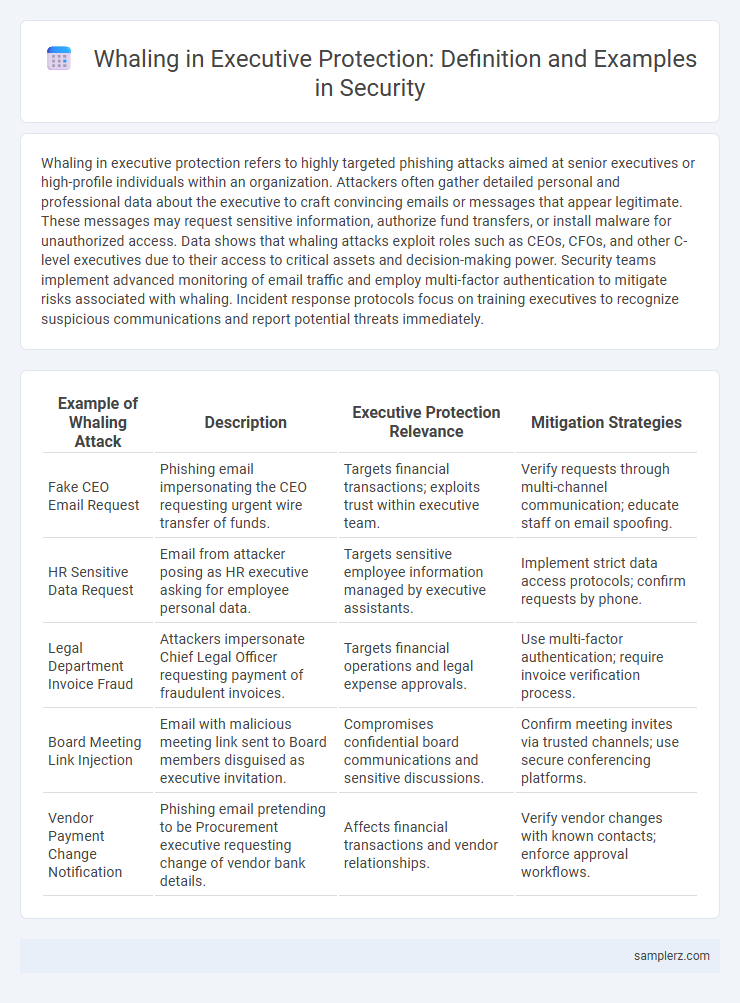
Table of Comparison
| Example of Whaling Attack | Description | Executive Protection Relevance | Mitigation Strategies |
|---|---|---|---|
| Fake CEO Email Request | Phishing email impersonating the CEO requesting urgent wire transfer of funds. | Targets financial transactions; exploits trust within executive team. | Verify requests through multi-channel communication; educate staff on email spoofing. |
| HR Sensitive Data Request | Email from attacker posing as HR executive asking for employee personal data. | Targets sensitive employee information managed by executive assistants. | Implement strict data access protocols; confirm requests by phone. |
| Legal Department Invoice Fraud | Attackers impersonate Chief Legal Officer requesting payment of fraudulent invoices. | Targets financial operations and legal expense approvals. | Use multi-factor authentication; require invoice verification process. |
| Board Meeting Link Injection | Email with malicious meeting link sent to Board members disguised as executive invitation. | Compromises confidential board communications and sensitive discussions. | Confirm meeting invites via trusted channels; use secure conferencing platforms. |
| Vendor Payment Change Notification | Phishing email pretending to be Procurement executive requesting change of vendor bank details. | Affects financial transactions and vendor relationships. | Verify vendor changes with known contacts; enforce approval workflows. |
Understanding Whaling Attacks in Executive Protection
Whaling attacks in executive protection target high-ranking individuals through highly personalized and deceptive emails designed to extract sensitive information or gain unauthorized access. These attacks exploit executives' trust by mimicking legitimate communications from trusted sources, often involving urgent requests or confidential business matters. Effective defense strategies include rigorous email authentication protocols, employee awareness training, and real-time monitoring of executive communications.
Real-World Whaling Incidents Targeting Executives
Whaling attacks in executive protection frequently involve highly targeted phishing schemes aimed at CEOs and CFOs to manipulate financial transactions or steal sensitive corporate data. A notable real-world incident occurred in 2016 when hackers impersonated a company's CFO to initiate fraudulent wire transfers exceeding $100 million. These attacks exploit the authority and access of top executives, emphasizing the need for robust verification protocols and advanced threat detection in corporate security frameworks.
High-Profile Cases of Whaling in Corporate Security
High-profile cases of whaling in corporate security involve targeted phishing attacks aimed directly at executives and high-ranking officials to steal sensitive information or initiate fraudulent transactions. One notable example is the CEO fraud incident at a multinational firm where attackers impersonated the CEO via email, successfully redirecting millions in wire transfers. These sophisticated whaling attempts exploit executive communication channels, emphasizing the need for robust multi-factor authentication and employee training in corporate security protocols.
Tactics Used by Cybercriminals in Whaling Scams
Cybercriminals in whaling scams targeting executive protection often employ spear-phishing emails disguised as urgent requests from top-level management, leveraging social engineering to exploit trust and authority. They use spoofed email addresses and domain impersonation to deceive security teams into revealing sensitive information or authorizing unauthorized financial transactions. Advanced tactics include embedding malicious links or attachments to deploy malware, enabling attackers to gain persistent access to confidential organizational data.
How Executives Become Primary Targets for Whaling
Executives become primary targets for whaling due to their access to sensitive corporate information and high-level financial assets, making them lucrative victims for cybercriminals. Threat actors exploit their public profiles and leverage social engineering tactics to craft convincing, personalized phishing emails that appear legitimate. These attacks often aim to gain unauthorized access to confidential data or initiate fraudulent financial transactions, compromising organizational security at the highest levels.
Impact of Whaling Attacks on Organizational Security
Whaling attacks targeting high-level executives expose organizations to significant security risks, including unauthorized access to sensitive data and financial fraud. These sophisticated spear-phishing attempts often result in compromised corporate email accounts, leading to breaches in confidential communications and strategic plans. The financial and reputational damage inflicted by successful whaling exploits can undermine overall organizational security posture and trust.
Preventative Measures Against Whaling in Executive Protection
Implementing multi-factor authentication and regular employee training significantly reduces the risk of whaling attacks in executive protection by ensuring only verified personnel access sensitive communications. Advanced email filtering systems and AI-driven threat detection tools monitor for impersonation and phishing attempts targeting high-profile executives. Establishing strict protocols for verifying financial transactions and sensitive requests further mitigates the chances of successful whaling breaches.
Training Executives to Recognize Whaling Attempts
Training executives to recognize whaling attempts involves educating them on identifying highly targeted phishing attacks that exploit their role and authority. Emphasizing the analysis of email addresses, scrutinizing unusual requests for sensitive information, and verifying communication through secondary channels reduces the risk of data breaches. Implementing simulated whaling scenarios during security training enhances executive awareness and response effectiveness.
Lessons Learned from Whaling Attacks in Business Leadership
Whaling attacks in executive protection expose vulnerabilities in high-level business leadership by targeting CEOs and CFOs through sophisticated social engineering tactics that exploit trust and authority. Lessons learned emphasize the necessity of comprehensive cybersecurity training, multi-factor authentication, and vigilance in verifying communication channels to prevent unauthorized access and financial loss. Implementing these strategies strengthens organizational resilience against targeted whaling threats.
Security Technologies Mitigating Whaling Risks for Executives
Whaling attacks targeting executives exploit personalized spear-phishing strategies to breach sensitive corporate information. Advanced security technologies such as AI-driven email filtering, multi-factor authentication, and behavioral analytics play crucial roles in detecting and preventing these high-profile phishing attempts. Implementing endpoint security solutions and continuous monitoring significantly reduces the risk of whaling-related breaches in executive protection environments.
example of whaling in executive protection Infographic
 samplerz.com
samplerz.com