A common example of a side-channel attack in cryptography is the timing attack. This attack exploits variations in the time taken to execute cryptographic algorithms, revealing sensitive information such as secret keys. Attackers measure the time required for operations like encryption or decryption to infer key bits based on execution time differences. Power analysis attacks represent another important category of side-channel attacks targeting cryptographic devices. These attacks analyze the power consumption patterns during cryptographic processing to extract secret keys or other confidential data. Techniques like Differential Power Analysis (DPA) allow adversaries to correlate power usage data with intermediate cryptographic values, undermining the security of hardware implementations.
Table of Comparison
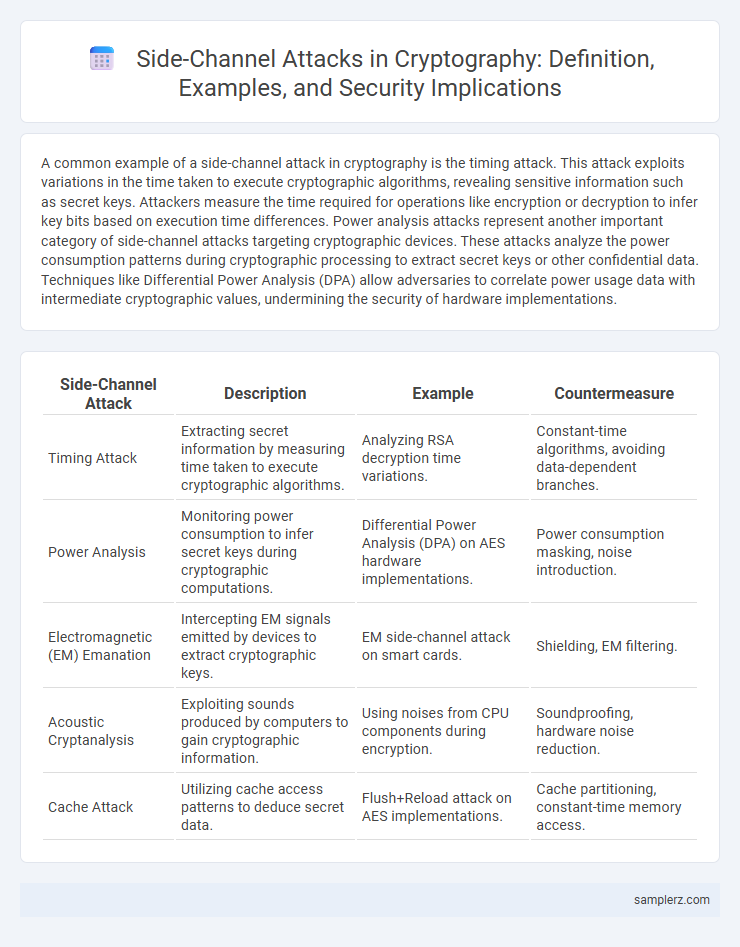
| Side-Channel Attack | Description | Example | Countermeasure |
|---|---|---|---|
| Timing Attack | Extracting secret information by measuring time taken to execute cryptographic algorithms. | Analyzing RSA decryption time variations. | Constant-time algorithms, avoiding data-dependent branches. |
| Power Analysis | Monitoring power consumption to infer secret keys during cryptographic computations. | Differential Power Analysis (DPA) on AES hardware implementations. | Power consumption masking, noise introduction. |
| Electromagnetic (EM) Emanation | Intercepting EM signals emitted by devices to extract cryptographic keys. | EM side-channel attack on smart cards. | Shielding, EM filtering. |
| Acoustic Cryptanalysis | Exploiting sounds produced by computers to gain cryptographic information. | Using noises from CPU components during encryption. | Soundproofing, hardware noise reduction. |
| Cache Attack | Utilizing cache access patterns to deduce secret data. | Flush+Reload attack on AES implementations. | Cache partitioning, constant-time memory access. |
Power Analysis Attacks in Cryptographic Hardware
Power Analysis Attacks exploit variations in the electrical power consumption of cryptographic hardware to extract secret keys and sensitive data. Differential Power Analysis (DPA) and Simple Power Analysis (SPA) are prominent techniques that analyze power traces during encryption operations to identify cryptographic key-dependent patterns. Countermeasures such as masking, hiding, and noise injection are essential to mitigate these side-channel vulnerabilities and enhance hardware security.
Timing Attacks on Encryption Algorithms
Timing attacks exploit variations in the time taken by encryption algorithms to process data, revealing sensitive information such as secret keys. These attacks analyze execution time differences caused by conditional branches or memory access patterns during cryptographic operations. Countermeasures like constant-time algorithms and masking techniques are critical to defend encryption systems from timing-based side-channel vulnerabilities.
Electromagnetic Emanations in Cryptographic Devices
Electromagnetic emanations from cryptographic devices leak sensitive information through unintentional radiation patterns captured by attackers. Techniques like electromagnetic analysis exploit these signals to recover encryption keys without direct access to the device. Mitigating these side-channel attacks requires shielding, signal filtering, and implementing secure hardware designs to minimize data leakage.
Acoustic Side-Channel Leaks in Password Recovery
Acoustic side-channel leaks in password recovery occur when sensitive information is unintentionally emitted as sound during cryptographic operations, such as keystroke sounds or electronic component vibrations. Attackers can analyze these acoustic signals to extract partial or full passwords, bypassing traditional cryptographic protections. Research demonstrates that microphones and machine learning algorithms can successfully recover cryptographic keys by exploiting these acoustic signatures.
Cache Timing Attacks in Software Implementations
Cache timing attacks exploit variations in cache access times to infer sensitive cryptographic keys during software execution. These attacks leverage timing differences caused by cache hits and misses when processing secret data, enabling attackers to reconstruct encryption keys without direct access. Implementations of AES and RSA have demonstrated vulnerability to cache timing attacks in shared computing environments.
Differential Fault Analysis in Smart Cards
Differential Fault Analysis (DFA) targets cryptographic implementations in smart cards by inducing faults during encryption processes to reveal secret keys. By comparing correct and faulty ciphertext pairs, attackers exploit discrepancies to recover private keys without detecting algorithmic weaknesses. This side-channel attack exploits physical vulnerabilities in hardware to compromise secure cryptographic storage in embedded devices.
Cold Boot Attacks on Encrypted Storage
Cold boot attacks exploit data remanence in DRAM by rapidly cooling memory modules to preserve encryption keys after system shutdown. Attackers can then physically extract sensitive key material from memory, bypassing software-based encryption protections on storage devices. This side-channel vulnerability highlights the importance of hardware-level defenses and secure key management in cryptographic systems.
Rowhammer Exploits in Memory Modules
Rowhammer exploits target vulnerabilities in DRAM memory modules by rapidly accessing (hammering) specific rows, causing bit flips in adjacent memory cells, which can lead to unauthorized data corruption or privilege escalation. This side-channel attack leverages physical hardware properties to breach cryptographic protections by inducing faults in memory-stored cryptographic keys or sensitive information. Defensive measures include implementing error-correcting code (ECC) memory, increasing refresh rates, and deploying hardware-level mitigations to detect and prevent Rowhammer-induced tampering.
Optical Side-Channel Attacks on Embedded Systems
Optical side-channel attacks exploit electromagnetic emissions or light patterns from embedded systems to extract cryptographic keys without direct access to the device. Techniques such as photonic emission analysis and laser fault injection leverage minute variations in LED indicators, LCD displays, or optical sensors to reveal sensitive data during encryption processes. These attacks highlight vulnerabilities in embedded cryptographic modules, emphasizing the need for shielding and noise generation countermeasures to protect against optical information leakage.
Key Extraction via Branch Prediction Side-Channels
Key extraction through branch prediction side-channels exploits the CPU's speculative execution to reveal sensitive cryptographic keys by analyzing variations in branch prediction behavior. Attackers monitor cache timing and branch predictor states to infer the path taken during cryptographic operations, enabling the recovery of secret keys without direct access to the secure memory. This technique highlights critical vulnerabilities in modern processors that demand robust countermeasures such as constant-time algorithms and hardware-level mitigations.
example of side-channel in cryptography Infographic
 samplerz.com
samplerz.com