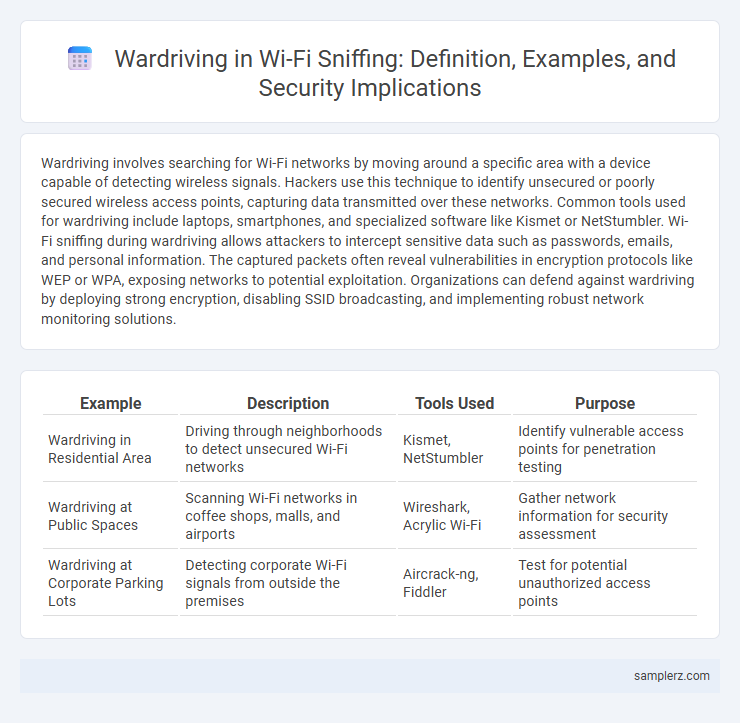
Wardriving involves searching for Wi-Fi networks by moving around a specific area with a device capable of detecting wireless signals. Hackers use this technique to identify unsecured or poorly secured wireless access points, capturing data transmitted over these networks. Common tools used for wardriving include laptops, smartphones, and specialized software like Kismet or NetStumbler. Wi-Fi sniffing during wardriving allows attackers to intercept sensitive data such as passwords, emails, and personal information. The captured packets often reveal vulnerabilities in encryption protocols like WEP or WPA, exposing networks to potential exploitation. Organizations can defend against wardriving by deploying strong encryption, disabling SSID broadcasting, and implementing robust network monitoring solutions.
Table of Comparison
| Example | Description | Tools Used | Purpose |
|---|---|---|---|
| Wardriving in Residential Area | Driving through neighborhoods to detect unsecured Wi-Fi networks | Kismet, NetStumbler | Identify vulnerable access points for penetration testing |
| Wardriving at Public Spaces | Scanning Wi-Fi networks in coffee shops, malls, and airports | Wireshark, Acrylic Wi-Fi | Gather network information for security assessment |
| Wardriving at Corporate Parking Lots | Detecting corporate Wi-Fi signals from outside the premises | Aircrack-ng, Fiddler | Test for potential unauthorized access points |
Understanding Wardriving: A Modern Security Threat
Wardriving involves using a portable device to scan and map wireless networks, exposing unsecured Wi-Fi networks to potential cyberattacks such as data interception or unauthorized access. Attackers exploit weak encryption protocols like WEP and outdated security configurations to sniff network traffic and gather sensitive information. Recognizing wardriving techniques is crucial for implementing robust Wi-Fi security measures, including WPA3 encryption and regular network monitoring to mitigate risks.
How Wardriving Exploits Wi-Fi Networks
Wardriving exploits Wi-Fi networks by locating and capturing unsecured wireless signals using GPS-enabled devices and specialized software. Attackers identify vulnerable access points with weak encryption or default configurations, allowing unauthorized access to network resources. This technique enables interception of sensitive data, network traffic analysis, and potential deployment of malware or man-in-the-middle attacks on compromised Wi-Fi networks.
Common Tools Used in Wi-Fi Sniffing Attacks
Common tools used in Wi-Fi sniffing attacks include Kismet, Aircrack-ng, and Wireshark, which enable attackers to capture and analyze wireless traffic effectively. These tools can detect hidden networks, intercept authentication handshakes, and decrypt WEP and WPA/WPA2 encrypted data under certain conditions. By leveraging such software, cybercriminals exploit vulnerabilities in wireless protocols to gain unauthorized access and harvest sensitive information.
Real-World Examples of Wardriving Incidents
Wardriving incidents often involve attackers using specialized software like Kismet or NetStumbler to detect unsecured Wi-Fi networks in urban areas. A notable example happened in 2006 when hackers in New York City exploited wardriving to infiltrate corporate networks, leading to unauthorized access and data theft. These real-world cases highlight the dangers of poorly secured wireless networks and the importance of robust encryption protocols such as WPA3.
Wardriving Techniques: Scanning and Mapping Wireless Networks
Wardriving techniques involve using GPS-enabled devices combined with Wi-Fi scanners like Kismet or NetStumbler to detect and map wireless networks by capturing SSID, signal strength, and encryption type. Attackers systematically drive through areas, logging network data to create detailed maps of vulnerable access points, which can be exploited for unauthorized access or data interception. The effectiveness of these techniques relies on automated tools for passive scanning and real-time geolocation data integration.
Data Collected During Wardriving Activities
Wardriving activities involve collecting detailed data such as SSIDs, MAC addresses, encryption types, and signal strengths from nearby Wi-Fi networks. Attackers capture network configurations and traffic metadata without authorization, often logging timestamps and geographic locations using GPS. This gathered information aids in identifying vulnerable access points for potential exploitation or unauthorized access.
Legal and Ethical Implications of Wardriving
Wardriving involves searching for Wi-Fi networks by moving through an area, often using GPS and wireless devices, which raises significant legal and ethical concerns regarding unauthorized access and privacy violations. In many jurisdictions, capturing data from unsecured networks without explicit permission can lead to criminal charges under computer misuse and privacy laws. Ethical wardriving practices emphasize transparency, obtaining consent, and focusing solely on identifying network vulnerabilities for legitimate security assessments.
Impact of Wardriving on Corporate and Home Wi-Fi Security
Wardriving exposes vulnerabilities in both corporate and home Wi-Fi networks by identifying unsecured or poorly secured access points, increasing the risk of unauthorized access and data breaches. Cybercriminals exploit these weak points to intercept sensitive information, launch man-in-the-middle attacks, and deploy malware within targeted environments. Strengthening Wi-Fi encryption protocols such as WPA3 and implementing robust network monitoring are essential defenses against the impact of wardriving on security.
Detection and Prevention of Wardriving Attacks
Effective detection of wardriving attacks involves monitoring wireless network traffic for unusual signal patterns and identifying unauthorized access points using specialized Wi-Fi scanning tools. Prevention measures include enabling WPA3 encryption, implementing network access control (NAC) systems, and regularly updating firmware to close vulnerabilities exploited by wardrivers. Deploying intrusion detection systems (IDS) tailored for wireless environments enhances real-time alerts, enabling prompt response to suspicious scanning activities.
Best Practices to Safeguard Wi-Fi Networks Against Sniffing
Implement strong WPA3 encryption and complex, unique passwords to protect Wi-Fi networks from wardriving attacks, which exploit unsecured access points through Wi-Fi sniffing. Regularly update firmware on routers and enable MAC address filtering to restrict unauthorized devices from connecting. Employ network segmentation and use VPNs to encrypt traffic, minimizing the risk of data interception during wardriving activities.
example of wardriving in Wi-Fi sniffing Infographic
 samplerz.com
samplerz.com