Tailgating in facility access occurs when an unauthorized individual gains entry by closely following an authorized person without proper identification. This security breach often happens in high-traffic areas such as building entrances equipped with card readers or biometric scanners. Data from security audits reveal that tailgating incidents account for a significant percentage of unauthorized access attempts in corporate environments. Video surveillance and access control logs are essential data sources for detecting tailgating incidents. Security reports indicate that implementing anti-tailgating technologies such as turnstiles, mantraps, and alarmed doors reduces unauthorized entries by up to 70%. Entities responsible for facility security use these data points to enhance protocols and train personnel against tailgating risks.
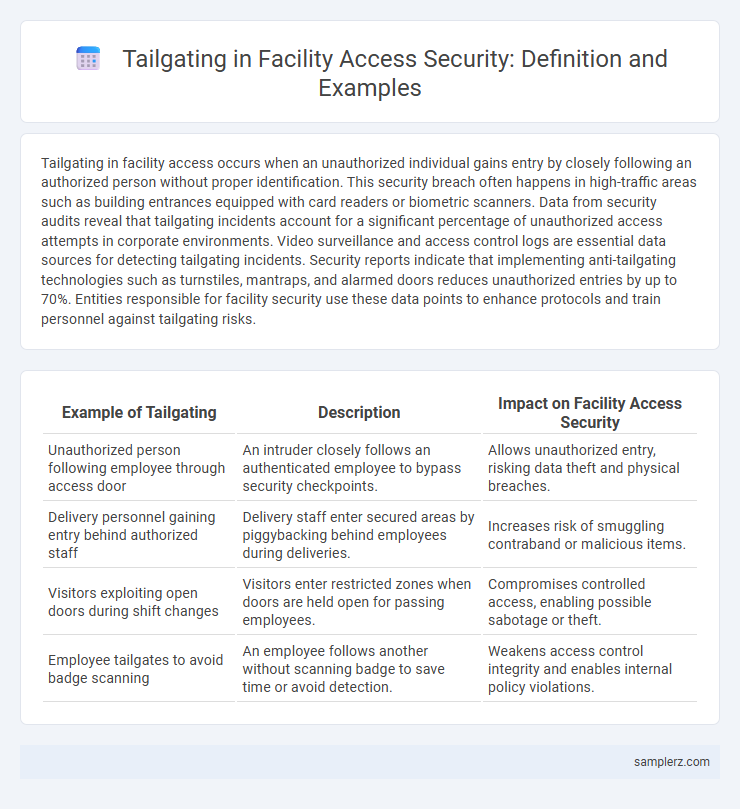
Table of Comparison
| Example of Tailgating | Description | Impact on Facility Access Security |
|---|---|---|
| Unauthorized person following employee through access door | An intruder closely follows an authenticated employee to bypass security checkpoints. | Allows unauthorized entry, risking data theft and physical breaches. |
| Delivery personnel gaining entry behind authorized staff | Delivery staff enter secured areas by piggybacking behind employees during deliveries. | Increases risk of smuggling contraband or malicious items. |
| Visitors exploiting open doors during shift changes | Visitors enter restricted zones when doors are held open for passing employees. | Compromises controlled access, enabling possible sabotage or theft. |
| Employee tailgates to avoid badge scanning | An employee follows another without scanning badge to save time or avoid detection. | Weakens access control integrity and enables internal policy violations. |
Common Tailgating Scenarios in Facility Access
Common tailgating scenarios in facility access include unauthorized individuals following authorized personnel through secure entry points without using access credentials. This often occurs during busy shift changes or when employees hold doors open for others, compromising physical security protocols. Tailgating exploits weaknesses in access control systems, increasing the risk of data breaches and theft.
Real-World Examples of Tailgating Breaches
Tailgating breaches in facility access often occur when unauthorized individuals follow authorized employees through secure entry points without using credentials. A notable example includes a 2019 incident where an attacker entered a corporate office by closely trailing an employee through a mantrap door, bypassing multifactor authentication. Such real-world events highlight the critical need for implementing anti-tailgating technologies like security turnstiles and biometric verification systems.
How Tailgating Compromises Physical Security
Tailgating occurs when an unauthorized individual follows an authorized person into a secured facility without proper credentials, bypassing access control measures. This practice compromises physical security by allowing intruders to exploit human error or social norms, increasing the risk of theft, espionage, or unauthorized access to sensitive areas. Effective countermeasures include installing turnstiles, implementing multi-factor authentication, and training employees to recognize and prevent tailgating incidents.
Case Studies: Tailgating Incidents in Corporate Environments
In a 2022 case study at a multinational corporation, unauthorized individuals gained access to secure areas by closely following employees through access-controlled doors, exploiting human error in badge usage. Another incident involved repeated tailgating at a financial institution where attackers used social engineering to appear authorized, leading to data breaches and financial loss. These examples emphasize the critical need for strict enforcement of access protocols and employee training in corporate facility security.
Insider vs. Outsider Tailgating Examples
Insider tailgating occurs when authorized employees hold doors open for colleagues, bypassing security protocols, while outsider tailgating involves unauthorized individuals following employees into secure areas without proper identification. Common insider examples include staff members allowing friends or contractors to enter restricted zones, whereas outsider examples often involve strangers exploiting moments when doors are momentarily ajar. Both types of tailgating pose significant security risks by compromising controlled access systems within facilities.
Tailgating in High-Security Areas: Notable Cases
Tailgating in high-security areas often involves unauthorized individuals closely following authorized personnel through secure doors, bypassing authentication measures. Notable cases include incidents at data centers where attackers gained access by tailgating employees during shift changes, leading to data breaches. Such breaches highlight vulnerabilities in physical access controls that require multi-factor authentication and employee vigilance to mitigate risks effectively.
Social Engineering Techniques Facilitating Tailgating
Social engineering techniques facilitating tailgating often involve impersonation of authorized personnel, such as delivery workers or IT staff, to exploit trust and gain unauthorized entry into secure facilities. Attackers may engage employees in casual conversation or carry bulky items to encourage door-holders to unknowingly grant access. These manipulative strategies bypass physical security measures by targeting human behavior rather than technical defenses.
Unauthorized Access: Tailgating in Government Facilities
Unauthorized access through tailgating in government facilities occurs when an individual follows an authorized person into a secured area without proper authentication, bypassing security checkpoints. This common security breach compromises sensitive information and critical infrastructure, increasing the risk of espionage, theft, or sabotage. Effective countermeasures include deploying anti-tailgating door systems, biometric scanners, and enforcing strict physical access protocols.
Consequences of Facility Access Tailgating
Facility access tailgating significantly compromises security protocols by allowing unauthorized individuals to enter restricted areas unnoticed, increasing the risk of theft, espionage, and physical harm. This breach can result in severe financial losses, damage to organizational reputation, and potential legal liabilities. Facilities must implement stringent measures such as biometric authentication and employee awareness training to mitigate the risks associated with tailgating.
Mitigation Failures: Tailgating Through Unsecured Entrances
Tailgating through unsecured entrances occurs when unauthorized individuals follow authorized personnel into restricted areas without proper validation, exploiting weak or absent access controls. Mitigation failures often stem from lack of physical barriers like turnstiles, insufficient employee training on access protocols, and absence of monitoring systems such as CCTV or security personnel. Effective prevention requires integrating multi-factor authentication technologies and enforcing strict access management policies to close vulnerabilities exploited during tailgating incidents.
example of tailgating in facility access Infographic
 samplerz.com
samplerz.com