In the realm of cybersecurity, pwnage refers to the successful exploitation of vulnerabilities within a system, leading to unauthorized control or access. One common example involves buffer overflow attacks, where an attacker sends excessive data to a program, overwriting memory and executing arbitrary code. This exploit grants the attacker the ability to run malicious commands as if they were a legitimate user, compromising the system's integrity. Another instance of pwnage occurs in web application exploits, such as SQL injection. Attackers inject malicious SQL code into input fields, manipulating the backend database to extract sensitive information or alter data. These attacks often result in data breaches, exposing user credentials and confidential records, and highlighting the critical need for robust input validation and security measures.
Table of Comparison
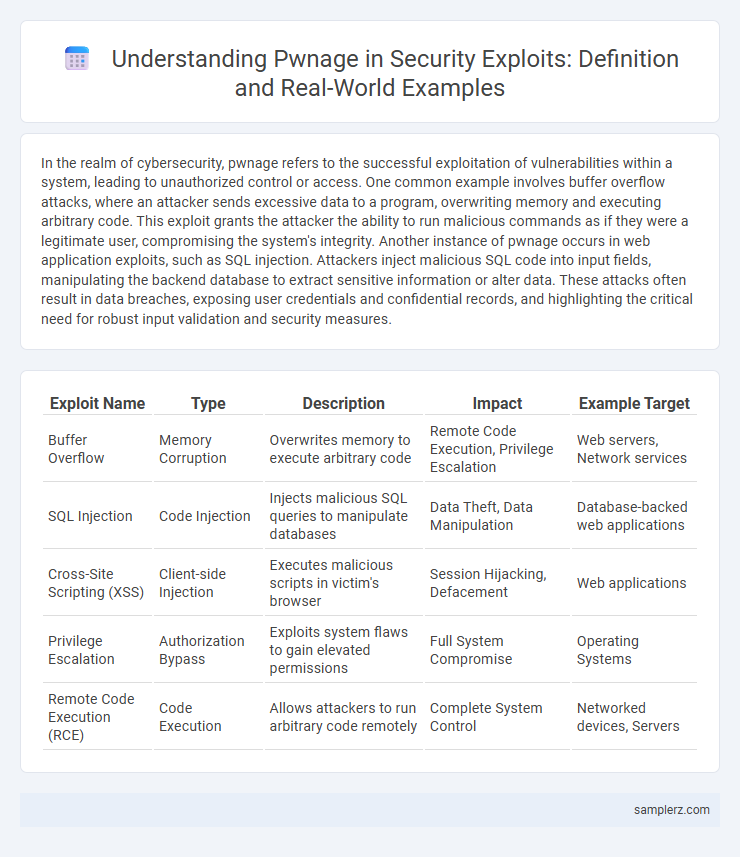
| Exploit Name | Type | Description | Impact | Example Target |
|---|---|---|---|---|
| Buffer Overflow | Memory Corruption | Overwrites memory to execute arbitrary code | Remote Code Execution, Privilege Escalation | Web servers, Network services |
| SQL Injection | Code Injection | Injects malicious SQL queries to manipulate databases | Data Theft, Data Manipulation | Database-backed web applications |
| Cross-Site Scripting (XSS) | Client-side Injection | Executes malicious scripts in victim's browser | Session Hijacking, Defacement | Web applications |
| Privilege Escalation | Authorization Bypass | Exploits system flaws to gain elevated permissions | Full System Compromise | Operating Systems |
| Remote Code Execution (RCE) | Code Execution | Allows attackers to run arbitrary code remotely | Complete System Control | Networked devices, Servers |
Defining Pwnage in Cybersecurity
Pwnage in cybersecurity refers to the complete compromise and control of a target system by an attacker after exploiting a vulnerability. This term often implies unauthorized access, privilege escalation, and the implanting of malicious payloads, leading to data breaches or system manipulation. High-profile examples include the 2017 Equifax breach, where attackers gained pwnage by exploiting an Apache Struts vulnerability.
Real-World Exploit Pwnage Incidents
Real-world exploit pwnage incidents such as the 2017 Equifax breach demonstrated the devastating impact of unpatched Apache Struts vulnerabilities, exposing sensitive data of over 147 million users. The 2021 Colonial Pipeline ransomware attack highlighted exploitation through weak network security, resulting in significant fuel supply disruptions across the U.S. These cases underscore the critical importance of timely patch management and robust cybersecurity defenses to prevent severe pwnage consequences.
Classic Buffer Overflow Attacks
Classic buffer overflow attacks manipulate memory by overwriting a program's buffer boundaries, allowing attackers to execute arbitrary code or crash the system. This exploit targets insecure coding practices in languages like C and C++, where input validation is insufficient and bounds checking is absent. Successful pwnage often leads to privilege escalation, unauthorized access, and system compromise, making it a critical vulnerability in cybersecurity defense.
Privilege Escalation Pwn Examples
Privilege escalation pwn examples often involve exploiting vulnerabilities in system processes or software services to gain unauthorized administrative access, such as exploiting Windows Kernel flaws or Linux SUID binaries. Attackers leverage buffer overflows, race conditions, or improperly configured permissions to escalate privileges from a standard user to root or SYSTEM. Notable cases include CVE-2021-3156 (Sudo vulnerability) and CVE-2019-14287, which allow attackers to execute arbitrary commands with elevated privileges.
Remote Code Execution in Action
Remote Code Execution (RCE) is a critical security vulnerability allowing attackers to execute arbitrary code on a target system remotely. For example, the WannaCry ransomware exploited a Windows SMB protocol vulnerability (EternalBlue) to perform RCE, rapidly spreading across networks and encrypting files. This exploit highlights the importance of timely patching and robust intrusion detection systems to prevent system compromise.
Notorious Zero-Day Exploits
Notorious zero-day exploits like Stuxnet and EternalBlue demonstrate severe vulnerabilities in critical infrastructure and widespread systems, enabling attackers to execute arbitrary code remotely before patches are available. These exploits often leverage undisclosed vulnerabilities, allowing threat actors to gain unauthorized access, escalate privileges, and deploy malware with devastating consequences. The rapid exploitation of zero-day flaws underscores the urgent need for proactive threat intelligence and robust endpoint protection measures in cybersecurity.
Social Engineering Leading to Pwnage
Social engineering exploits human psychology to gain unauthorized access, often resulting in pwnage by tricking victims into divulging sensitive information or executing malicious actions. Phishing attacks, spear-phishing emails, and pretexting are common techniques that manipulate trust and urgency, enabling attackers to bypass technical security measures. These tactics frequently lead to credential theft, unauthorized system access, and full compromise of targeted networks.
Pwnage via Web Application Vulnerabilities
Pwnage via web application vulnerabilities commonly exploits flaws such as SQL injection, cross-site scripting (XSS), and remote code execution to gain unauthorized access or control. Attackers leverage these weaknesses to steal sensitive data, escalate privileges, or deploy malware, compromising the entire system integrity. Effective mitigation includes regular security testing, input validation, and timely patch management to prevent exploitation.
Lessons Learned from Famous Pwns
The infamous 2017 Equifax breach exploited a vulnerability in the Apache Struts framework, highlighting the critical importance of timely patch management and proper input validation. The Stuxnet worm demonstrated how sophisticated malware leveraging zero-day exploits can target industrial control systems, emphasizing the need for robust network segmentation. The WannaCry ransomware attack illustrated the dangers of unpatched software and the necessity of comprehensive backup strategies and incident response planning.
Prevention Tactics Against Exploit Pwnage
Effective prevention tactics against exploit pwnage include implementing robust endpoint security solutions that detect anomalous behaviors indicative of an attack. Regularly applying security patches and updates to software reduces vulnerabilities that attackers can exploit for pwnage. Employing multifactor authentication and network segmentation limits unauthorized access and contains potential breaches.
example of pwnage in exploit Infographic
 samplerz.com
samplerz.com