Shimming in hardware security refers to the insertion of a small piece of code or a layer between the operating system and the hardware or firmware to intercept and potentially manipulate system operations. A common example is the use of a shim in the Secure Boot process, where a signed shim loader allows the execution of unsigned or third-party bootloaders while maintaining the chain of trust verified by the hardware's Trusted Platform Module (TPM). This technique enables compatibility but can also introduce vulnerabilities if exploited by malicious actors to bypass security measures. In hardware debugging and reverse engineering, shimming involves placing a thin electrical interface or adapter between hardware components to monitor or modify signal transmission without altering the original device. For instance, engineers use shims in embedded systems to intercept communication between microcontrollers and peripheral devices, capturing data for security analysis or firmware extraction. Shimming in this context serves as a valuable tool for identifying hardware vulnerabilities and ensuring compliance with security protocols.
Table of Comparison
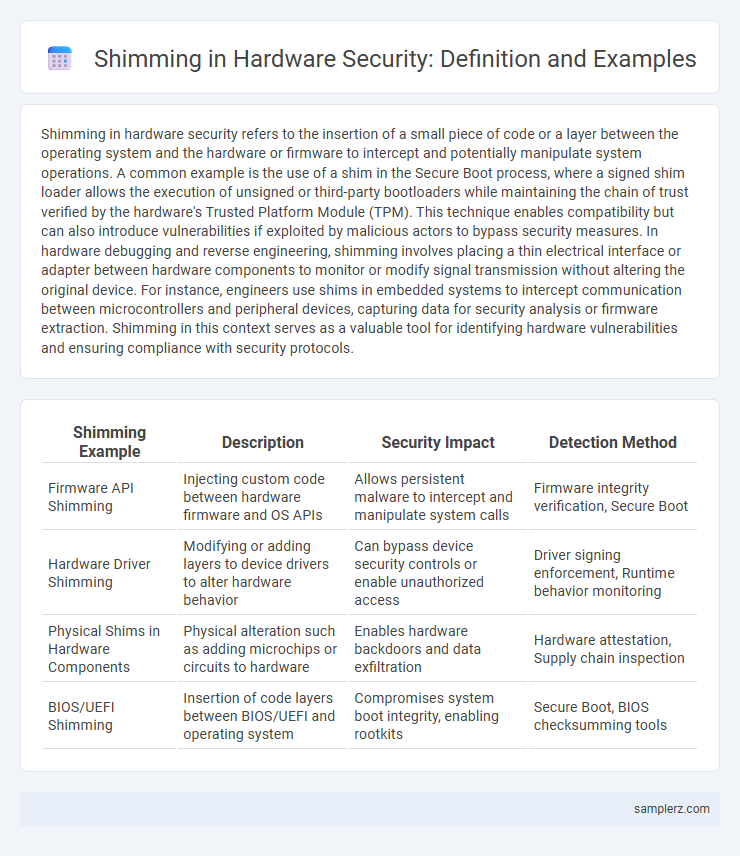
| Shimming Example | Description | Security Impact | Detection Method |
|---|---|---|---|
| Firmware API Shimming | Injecting custom code between hardware firmware and OS APIs | Allows persistent malware to intercept and manipulate system calls | Firmware integrity verification, Secure Boot |
| Hardware Driver Shimming | Modifying or adding layers to device drivers to alter hardware behavior | Can bypass device security controls or enable unauthorized access | Driver signing enforcement, Runtime behavior monitoring |
| Physical Shims in Hardware Components | Physical alteration such as adding microchips or circuits to hardware | Enables hardware backdoors and data exfiltration | Hardware attestation, Supply chain inspection |
| BIOS/UEFI Shimming | Insertion of code layers between BIOS/UEFI and operating system | Compromises system boot integrity, enabling rootkits | Secure Boot, BIOS checksumming tools |
Introduction to Shimming in Hardware Security
Shimming in hardware security refers to the insertion of a thin layer, or shim, between components to subtly alter system behavior or introduce hidden functionalities. This technique can be exploited to bypass security controls or inject malicious code at the hardware level, posing significant risks to embedded systems and trusted computing environments. Detecting shim attacks requires advanced forensic analysis and hardware integrity verification methods.
Common Types of Hardware Shimming Attacks
Hardware shimming attacks commonly include electromagnetic fault injection, voltage glitching, and laser fault injection, which manipulate device operations by altering electrical signals or timing. These techniques exploit vulnerabilities in microcontrollers, secure elements, and cryptographic chips to bypass security checks or extract sensitive information. Attackers often target IoT devices, smartcards, and automotive ECUs due to their widespread deployment and the critical nature of their security functions.
Real-World Examples of ATM Card Reader Shimming
ATM card reader shimming involves installing a thin device inside the card slot to capture data from the magnetic stripe during legitimate transactions. Real-world cases include shimming attacks on ATMs in countries like the United States, Canada, and the United Kingdom, where criminals retrieve card information along with PINs by combining shimming with hidden cameras. These sophisticated hardware-based skimming techniques exploit vulnerabilities in the card reader's internal components, emphasizing the need for enhanced ATM security measures such as encryption and tamper-resistant designs.
Shimming Techniques in Point-of-Sale (POS) Systems
Shimming techniques in Point-of-Sale (POS) systems involve inserting malicious hardware devices between the card reader and the internal processing unit to capture sensitive payment data such as magnetic stripe information and PIN codes. These methods exploit vulnerabilities in card reader designs by mimicking legitimate components, enabling attackers to collect transaction data undetected. Detecting and mitigating these attacks requires enhanced physical security measures and regular hardware inspections in retail environments.
Shimming in Access Control Hardware Devices
Shimming in access control hardware devices involves inserting thin, unauthorized materials between components to bypass security mechanisms, such as door locks or card readers. Attackers exploit vulnerabilities in physical barriers by manipulating the internal sensors or electronic circuits, allowing unauthorized access without triggering alarms. This method poses significant risks to secure facilities, emphasizing the need for robust tamper-resistant hardware and regular device inspections.
Magnetic Stripe Readers and Shimming Exploits
Magnetic stripe readers are vulnerable to shimming exploits, where attackers insert a thin device between the card and reader to capture sensitive data such as track information and PINs. These shims often contain microprocessors and memory chips capable of recording data without physical damage to the reader, making detection difficult. Security measures like encryption and tamper-resistant designs are essential to mitigate the threat of shim-based skimming attacks.
Examples of Hardware Shimming in IoT Devices
Hardware shimming in IoT devices often involves inserting malicious microchips or modifying existing circuitry to intercept data or bypass security controls. For instance, attackers implant tiny hardware shims between integrated circuits on a motherboard to eavesdrop on communications or manipulate firmware updates. Such physical tampering techniques enable stealthy exploitation of IoT devices, compromising confidentiality and integrity without detection by software defenses.
Shimming Attacks Targeting Smartcard Interfaces
Shimming attacks targeting smartcard interfaces exploit the insertion of malicious hardware or software layers between the smartcard and reader to intercept or manipulate data. These attacks can lead to unauthorized access, data extraction, and manipulation of cryptographic operations within secure elements. Effective countermeasures include secure channel protocols, hardware tamper detection, and robust authentication mechanisms designed to prevent unauthorized interfacing.
Detection Methods for Hardware Shims
Detection methods for hardware shims include side-channel analysis, which monitors power consumption and electromagnetic emissions to identify anomalies caused by malicious modifications. Optical inspection techniques using high-resolution microscopy or X-ray imaging reveal physical alterations in chip layers that indicate the presence of shims. Additionally, functional testing with machine learning models compares device behavior against known baselines to detect deviations caused by unauthorized hardware inserts.
Mitigation Strategies Against Hardware Shimming
Mitigation strategies against hardware shimming include implementing tamper-evident seals, secure boot processes, and physical intrusion detection mechanisms to prevent unauthorized hardware modifications. Employing hardware security modules (HSMs) and trusted platform modules (TPMs) enhances device integrity by safeguarding cryptographic keys from tampering. Regular hardware audits and real-time monitoring systems provide early detection of shimming attempts, reducing the risk of data breaches and maintaining system security.
example of shimming in hardware Infographic
 samplerz.com
samplerz.com