A canary trap in security is a strategic method used to identify insider threats by distributing slightly different versions of sensitive information to various suspects. Each unique version contains subtle, traceable alterations that act as identifiers if leaked. This technique helps pinpoint the exact individual responsible for unauthorized disclosures within an organization. For instance, a company might send out multiple versions of a confidential report to several employees suspected of potential leaks. Each report varies in specific data points such as project names, budget figures, or timelines. When the information is leaked externally, analysts can compare it against the unique versions to identify the source of the breach effectively.
Table of Comparison
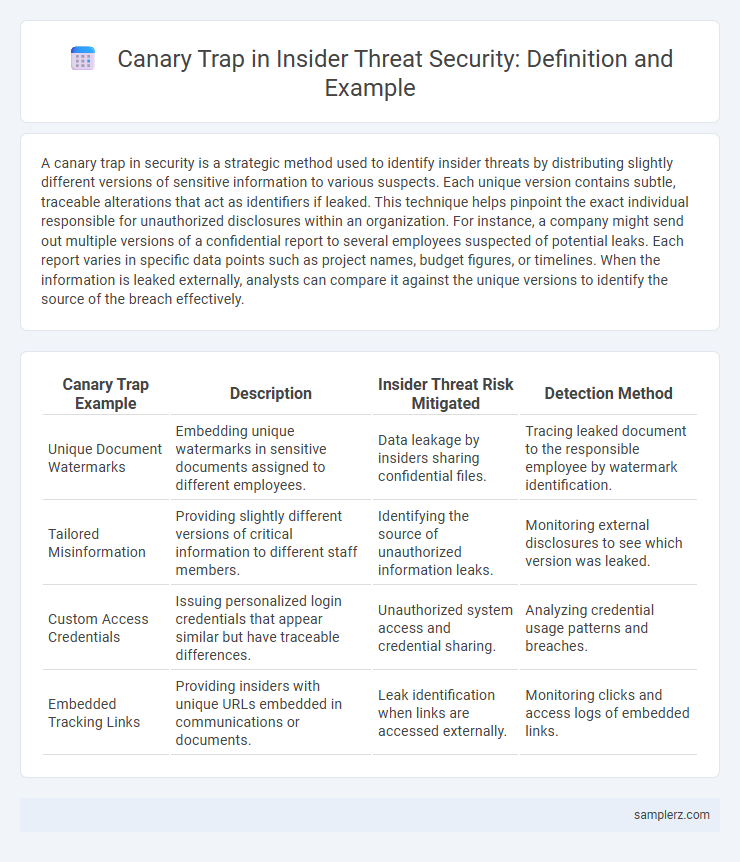
| Canary Trap Example | Description | Insider Threat Risk Mitigated | Detection Method |
|---|---|---|---|
| Unique Document Watermarks | Embedding unique watermarks in sensitive documents assigned to different employees. | Data leakage by insiders sharing confidential files. | Tracing leaked document to the responsible employee by watermark identification. |
| Tailored Misinformation | Providing slightly different versions of critical information to different staff members. | Identifying the source of unauthorized information leaks. | Monitoring external disclosures to see which version was leaked. |
| Custom Access Credentials | Issuing personalized login credentials that appear similar but have traceable differences. | Unauthorized system access and credential sharing. | Analyzing credential usage patterns and breaches. |
| Embedded Tracking Links | Providing insiders with unique URLs embedded in communications or documents. | Leak identification when links are accessed externally. | Monitoring clicks and access logs of embedded links. |
Understanding the Canary Trap in Insider Threat Scenarios
A canary trap in insider threat scenarios involves distributing unique, slightly altered versions of sensitive information to suspected employees, enabling detection when leaks occur. This technique helps security teams trace the source of insider threats by monitoring which version of the data is compromised. By embedding distinct markers in documents, organizations enhance their ability to identify and mitigate internal security breaches effectively.
Real-World Canary Trap Examples for Detecting Insider Threats
Real-world canary trap examples for detecting insider threats often involve embedding unique, fake data or access credentials within sensitive documents distributed to specific employees. When unauthorized leaks or actions occur, security teams can trace the breach back to the individual holding the unique "canary" information, effectively identifying the insider threat. Organizations like financial institutions and government agencies use canary traps to safeguard classified or proprietary information by monitoring these planted identifiers for illicit activity.
Deploying Canary Documents to Identify Data Leaks
Deploying canary documents embedded with unique identifiers is an effective strategy to detect insider threats by tracing unauthorized data leaks. Each canary document contains subtle variations that help security teams pinpoint the exact source of compromised information. This method enhances data loss prevention by providing actionable intelligence on malicious insiders attempting to exfiltrate sensitive information.
Case Study: Media Leaks and Canary Trap Effectiveness
A notable example of a canary trap in insider threat detection occurred in a media organization where confidential information was leaked. Unique variations of sensitive content were distributed to suspected employees, enabling identification of the insider when a particular version appeared publicly. This case study highlights the effectiveness of canary traps in tracing information leaks and mitigating insider threats within corporate security frameworks.
Leveraging Digital Watermarking as a Canary Trap Tool
Leveraging digital watermarking as a canary trap tool enables organizations to identify insider threats by embedding unique, traceable markers within sensitive data. These invisible watermarks can pinpoint the source of unauthorized disclosures by revealing which insider leaked specific information. This strategic use of digital watermarking enhances security protocols and supports early detection and mitigation of insider risks.
Role-Based Canary Traps in Sensitive Data Access
Role-based canary traps in sensitive data access involve assigning unique access credentials or datasets to different employees, enabling the identification of unauthorized data leaks by tracking which specific version is compromised. This method detects insider threats by embedding subtle variations or markers within data accessible only to particular roles, thereby isolating the source of the leak without alerting the individual. Implementing role-specific canary traps enhances security by providing precise attribution and deterring malicious insiders from unauthorized disclosure.
Canary Trap Implementation in Financial Institutions
Financial institutions implement canary traps by embedding unique, traceable information within sensitive documents distributed to employees or departments, enabling identification of the source in case of data leaks. This technique involves creating slight variations in account details, transaction records, or policy drafts to detect insider threats effectively. By analyzing the leaked data's unique markers, security teams swiftly pinpoint the compromised access points, enhancing overall cybersecurity resilience.
Legal and Ethical Considerations of Canary Trapping
Canary traps in insider threat detection involve embedding unique, traceable information to identify leaks, raising critical legal and ethical considerations. Organizations must ensure compliance with privacy laws such as GDPR and HIPAA, obtaining informed consent to avoid infringing on employee rights. Balancing effective security measures with transparency and respect for confidentiality is essential to uphold legal standards and maintain ethical integrity.
Lessons Learned from Successful Canary Trap Operations
Successful canary trap operations in insider threat detection reveal critical lessons such as the importance of creating unique yet plausible information variants to accurately identify leaks. Monitoring distinct data fingerprints allows security teams to trace unauthorized disclosures back to specific individuals with high confidence. These strategies emphasize proactive detection methods that enhance organizational resilience against internal breaches and reinforce accountability.
Best Practices for Canary Trap Deployment Against Insider Threats
Implementing canary traps to detect insider threats requires embedding unique, traceable information in documents shared with different employees to identify leaks. Segmentation of sensitive data combined with monitoring access patterns enhances early detection of unauthorized disclosures. Regularly updating canary markers and training employees on data handling protocols strengthens the overall effectiveness of this security strategy.
example of canary trap in insider threat Infographic
 samplerz.com
samplerz.com