A watermark in a document serves as a security feature to protect against unauthorized copying and tampering. It typically appears as a faint, embedded image or text, such as a company logo or the word "Confidential," visible when the document is held up to a light source. This embedded data enhances document authenticity by linking it to a specific entity or usage context. Electronic watermarks provide an additional layer of security by embedding metadata within the document file itself. This metadata can include timestamps, digital signatures, or user identification data to track document access and modifications. Incorporating watermarks in sensitive documents like contracts, certificates, or financial reports significantly reduces the risk of fraud and unauthorized distribution.
Table of Comparison
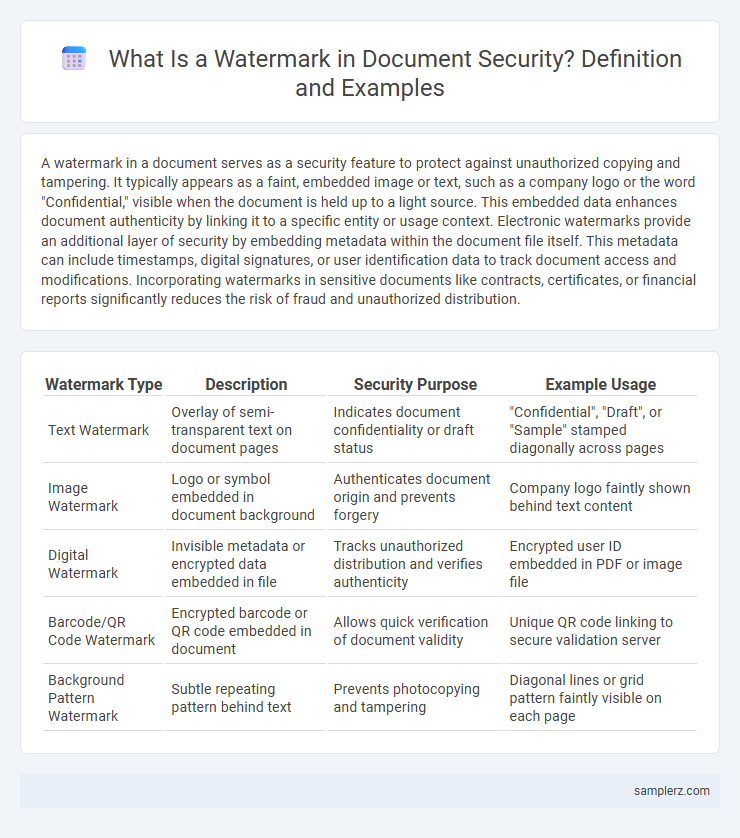
| Watermark Type | Description | Security Purpose | Example Usage |
|---|---|---|---|
| Text Watermark | Overlay of semi-transparent text on document pages | Indicates document confidentiality or draft status | "Confidential", "Draft", or "Sample" stamped diagonally across pages |
| Image Watermark | Logo or symbol embedded in document background | Authenticates document origin and prevents forgery | Company logo faintly shown behind text content |
| Digital Watermark | Invisible metadata or encrypted data embedded in file | Tracks unauthorized distribution and verifies authenticity | Encrypted user ID embedded in PDF or image file |
| Barcode/QR Code Watermark | Encrypted barcode or QR code embedded in document | Allows quick verification of document validity | Unique QR code linking to secure validation server |
| Background Pattern Watermark | Subtle repeating pattern behind text | Prevents photocopying and tampering | Diagonal lines or grid pattern faintly visible on each page |
Understanding Document Watermarking
Document watermarking embeds visible or invisible markers within a file to verify authenticity and prevent unauthorized copying. Techniques include digital watermarks that survive format changes, enhancing security by linking the document to its owner or source. This method is crucial in protecting sensitive information and maintaining document integrity across various platforms.
Types of Watermarks in Security Documents
Security documents employ various types of watermarks to enhance authenticity and prevent forgery, including visible, invisible, and digital watermarks. Visible watermarks are typically translucent images or patterns embedded during paper manufacturing, easily recognized under normal light. Invisible watermarks require special equipment like UV light or infrared scanners for detection, while digital watermarks involve embedding encrypted data within electronic documents for robust verification.
Purpose of Using Watermarks for Document Protection
Watermarks in document security serve as a crucial tool for verifying authenticity and deterring unauthorized copying or distribution. By embedding visible or invisible marks, organizations can trace document origins and detect tampering attempts, enhancing intellectual property protection. These watermarks maintain the integrity of sensitive information and reinforce compliance with regulatory standards.
Visual Watermark Examples in Digital Files
Visual watermarks in digital files serve as a crucial security feature by embedding transparent logos or text overlays that deter unauthorized use and distribution. Common examples include semi-transparent company logos placed diagonally across PDF documents or images, ensuring brand visibility while preserving content readability. These watermarks are often customized with metadata such as timestamps and user IDs to enhance traceability and authenticity verification.
Invisible Watermarks: How They Work
Invisible watermarks in documents embed hidden information within the digital content without altering its visible appearance, enhancing document security by enabling authentication and copyright protection. These watermarks use techniques such as frequency domain modulation or pixel value adjustments to encode data imperceptibly, detectable only with specialized software or algorithms. This method safeguards sensitive documents from unauthorized copying or tampering by providing a covert layer of verification.
Watermarks in Legal and Official Documents
Watermarks in legal and official documents serve as a critical security feature to prevent forgery and unauthorized duplication. These watermarks often consist of intricate patterns or text embedded into the paper during manufacturing, making alterations or counterfeiting easily detectable. Government-issued certificates, contracts, and notarized papers frequently utilize watermarks to ensure authenticity and maintain the document's integrity.
Digital Signature vs. Watermark: Key Differences
Digital signatures provide cryptographic security by verifying document authenticity and integrity, whereas watermarks serve as visible or invisible indicators to discourage unauthorized copying. Unlike watermarks, which can be removed or altered without detection, digital signatures create tamper-evident proofs linked to the signer's identity. This fundamental difference makes digital signatures essential for legally binding and secure transactions, while watermarks mainly offer deterrence and brand protection.
Case Studies: Watermarked Documents in Action
Watermarked documents have proven essential in safeguarding sensitive information across various industries, with case studies demonstrating their effectiveness in preventing unauthorized distribution and tampering. In financial institutions, watermarks embedded in confidential reports deter fraud by visibly marking each document with unique identifiers linked to the recipient. Legal firms utilize watermarked contracts to ensure authenticity and trace leaks, reinforcing document integrity throughout the litigation process.
Best Practices for Watermarking Sensitive Documents
Applying watermarks to sensitive documents enhances security by visibly marking ownership and deterring unauthorized distribution. Use semi-transparent, non-intrusive watermarks that include dynamic information such as user ID or timestamp to track document access effectively. Ensure watermarks are embedded within the document layers to prevent easy removal while maintaining document readability for legitimate users.
Future Trends in Document Watermark Security
Future trends in document watermark security emphasize the integration of blockchain technology for immutable watermark verification, enhancing authenticity and traceability. Advanced artificial intelligence algorithms enable dynamic and adaptive watermarking techniques that resist tampering and unauthorized removal. Quantum encryption methods are being researched to further secure watermark data against emerging cyber threats and sophisticated attacks.
example of watermark in document Infographic
 samplerz.com
samplerz.com