Cryptojacking is a form of resource hijacking where attackers secretly use a victim's computing power to mine cryptocurrency. This type of cyberattack exploits processing resources such as CPUs and GPUs without the user's consent. Often, cryptojacking scripts are embedded in websites or delivered through malicious software, causing significant performance degradation and increased energy consumption. In security contexts, detecting cryptojacking requires monitoring CPU usage spikes and network traffic anomalies. Organizations must implement strong endpoint protection and regular system audits to identify unauthorized mining activities. Effective response strategies include blocking malicious scripts and updating security policies to mitigate future threats.
Table of Comparison
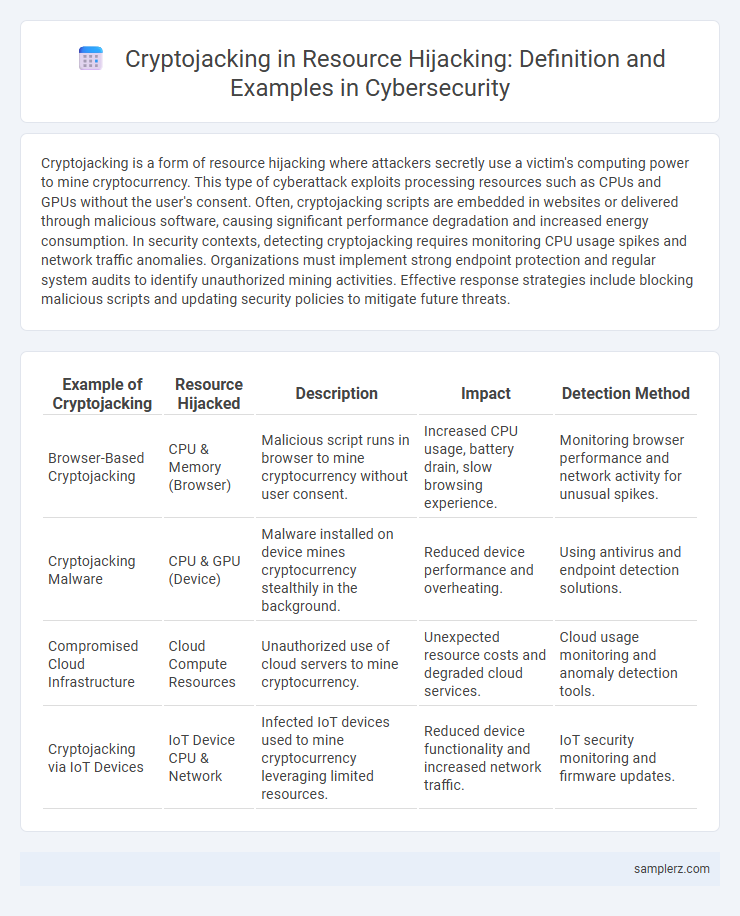
| Example of Cryptojacking | Resource Hijacked | Description | Impact | Detection Method |
|---|---|---|---|---|
| Browser-Based Cryptojacking | CPU & Memory (Browser) | Malicious script runs in browser to mine cryptocurrency without user consent. | Increased CPU usage, battery drain, slow browsing experience. | Monitoring browser performance and network activity for unusual spikes. |
| Cryptojacking Malware | CPU & GPU (Device) | Malware installed on device mines cryptocurrency stealthily in the background. | Reduced device performance and overheating. | Using antivirus and endpoint detection solutions. |
| Compromised Cloud Infrastructure | Cloud Compute Resources | Unauthorized use of cloud servers to mine cryptocurrency. | Unexpected resource costs and degraded cloud services. | Cloud usage monitoring and anomaly detection tools. |
| Cryptojacking via IoT Devices | IoT Device CPU & Network | Infected IoT devices used to mine cryptocurrency leveraging limited resources. | Reduced device functionality and increased network traffic. | IoT security monitoring and firmware updates. |
Understanding Cryptojacking: A Form of Resource Hijacking
Cryptojacking is a malicious activity where cybercriminals covertly use a victim's computing resources to mine cryptocurrency, significantly degrading system performance and increasing energy consumption. This form of resource hijacking exploits vulnerabilities in software or websites, often through malicious scripts or infected applications, without the user's consent or knowledge. Understanding cryptojacking is essential for implementing effective cybersecurity measures to detect and prevent unauthorized mining operations that compromise device security and operational efficiency.
How Cryptojackers Compromise Systems for Mining
Cryptojackers compromise systems for mining by exploiting vulnerabilities such as outdated software, weak passwords, or unsecured remote desktop protocols to gain unauthorized access. They often deploy malicious scripts or malware that stealthily run cryptocurrency mining processes, consuming significant CPU or GPU resources without user consent. This unauthorized resource hijacking leads to degraded system performance, increased energy consumption, and potential hardware damage.
Notorious Real-World Cryptojacking Incidents
The 2018 Coinhive cryptojacking campaign exploited thousands of websites, injecting malicious scripts that covertly mined Monero without user consent, causing significant CPU resource drain worldwide. Another high-profile case involved the Tesla cloud infrastructure breach in 2018, where attackers deployed cryptojacking malware through misconfigured Kubernetes consoles to mine cryptocurrency on company servers. These incidents highlight the critical security risks of cryptojacking, including unauthorized resource consumption and compromised organizational networks.
Cryptojacking Exploits in Cloud Infrastructure
Cryptojacking exploits in cloud infrastructure involve unauthorized use of cloud-based resources to mine cryptocurrencies, significantly increasing operational costs and degrading system performance. Attackers often leverage vulnerabilities in poorly secured cloud environments, deploying malicious scripts or containers that consume CPU and GPU resources without detection. Continuous monitoring and implementing strict access controls are essential to mitigate cryptojacking risks within cloud infrastructures.
Case Study: Cryptojacking via Malicious Browser Extensions
Cryptojacking through malicious browser extensions exploits users' devices by secretly mining cryptocurrency using their computing resources without consent. A notable case involved extensions distributed on popular web stores that injected cryptojacking scripts into browsers, significantly degrading system performance and increasing electricity usage. This method leverages the widespread use of browser extensions to bypass traditional software security measures, highlighting the importance of vigilant extension vetting and continuous monitoring for unusual CPU usage.
Server Resource Hijacking: Examples from the Enterprise Sector
Cryptojacking in server resource hijacking often targets enterprise sectors by exploiting vulnerabilities in cloud infrastructure and virtualization platforms to mine cryptocurrency illicitly. Enterprises such as financial institutions and healthcare providers face risks where attackers deploy hidden scripts on servers, leading to degraded performance and increased energy costs. Security measures must include real-time monitoring, patch management, and anomaly detection to mitigate unauthorized cryptojacking activities effectively.
IoT Devices: Unseen Victims of Cryptojacking Attacks
Cryptojacking exploits IoT devices by covertly installing malicious software that hijacks processing power to mine cryptocurrencies, often unnoticed due to limited device security. Vulnerable IoT devices such as smart cameras, thermostats, and routers are frequently targeted, causing system slowdowns and increased energy consumption. The distributed nature of IoT networks amplifies the impact, making cryptojacking a significant threat to both individual users and enterprises reliant on interconnected devices.
Cryptojacking in Content Management Systems: Notable Breaches
Cryptojacking in Content Management Systems (CMS) often exploits vulnerabilities in platforms like WordPress, Joomla, and Drupal to embed unauthorized cryptocurrency miners. Notable breaches include the 2018 Coinhive attack on WordPress sites, where hackers injected malicious JavaScript mining Monero, significantly degrading site performance. These incidents highlight the critical need for regular CMS updates, strong plugin management, and comprehensive security audits to prevent resource hijacking through cryptojacking.
Mobile Device Resource Hijacking through Cryptojacking
Mobile device resource hijacking through cryptojacking exploits the processing power of smartphones and tablets without user consent, often causing significant battery drain and overheating. Cybercriminals embed malicious scripts in mobile apps or websites that silently mine cryptocurrencies like Monero using the device's CPU and GPU resources. This unauthorized use depletes device performance, increases energy consumption, and poses serious security risks to mobile users.
Lessons Learned from High-Profile Cryptojacking Cases
High-profile cryptojacking cases reveal critical lessons about resource hijacking, emphasizing the importance of robust endpoint security and continuous network monitoring to detect unauthorized mining activities. Attackers exploit vulnerabilities in software and hardware, leading to significant performance degradation and increased energy costs, underscoring the need for timely patch management. Organizations learn to implement strong access controls and user training to mitigate the risk of cryptojacking threats effectively.
example of cryptojacking in resource hijacking Infographic
 samplerz.com
samplerz.com