Deepfake technology poses significant threats to identity verification systems by creating highly realistic fake images or videos of individuals. For example, cybercriminals can use deepfake videos to impersonate authorized personnel during biometric verification processes, bypassing facial recognition security measures. These manipulated media files can deceive security algorithms, leading to unauthorized access to sensitive accounts and systems. Financial institutions and government agencies increasingly face challenges in detecting deepfake-based identity fraud. Advanced deepfake detection tools analyze subtle inconsistencies in eye movement, skin texture, and audio patterns to differentiate between genuine and synthetic identities. Incorporating multi-factor authentication alongside deepfake detection enhances the robustness of identity verification frameworks against evolving threats.
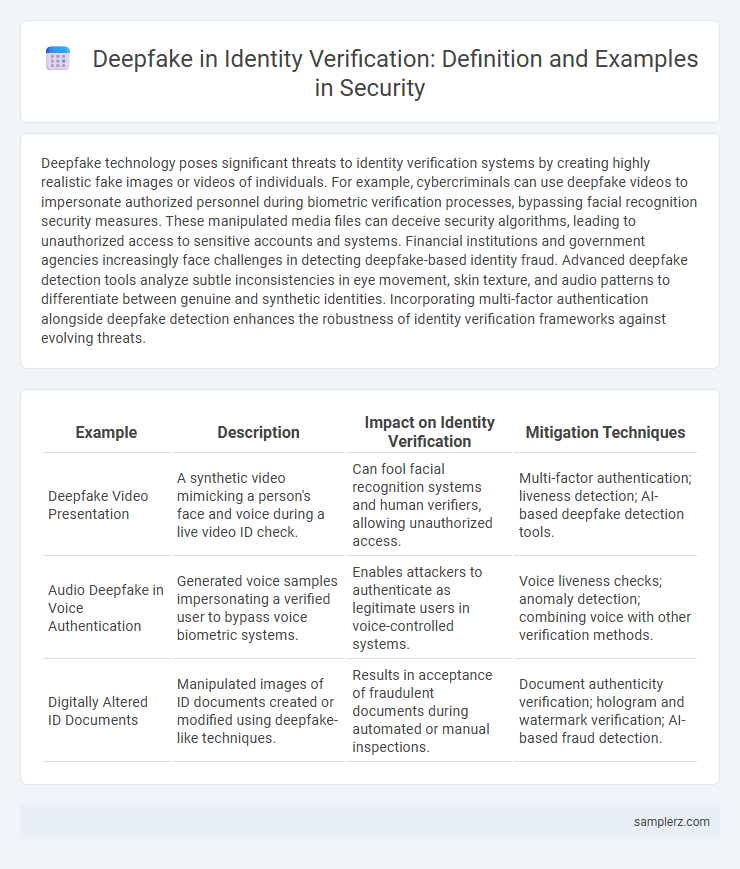
Table of Comparison
| Example | Description | Impact on Identity Verification | Mitigation Techniques |
|---|---|---|---|
| Deepfake Video Presentation | A synthetic video mimicking a person's face and voice during a live video ID check. | Can fool facial recognition systems and human verifiers, allowing unauthorized access. | Multi-factor authentication; liveness detection; AI-based deepfake detection tools. |
| Audio Deepfake in Voice Authentication | Generated voice samples impersonating a verified user to bypass voice biometric systems. | Enables attackers to authenticate as legitimate users in voice-controlled systems. | Voice liveness checks; anomaly detection; combining voice with other verification methods. |
| Digitally Altered ID Documents | Manipulated images of ID documents created or modified using deepfake-like techniques. | Results in acceptance of fraudulent documents during automated or manual inspections. | Document authenticity verification; hologram and watermark verification; AI-based fraud detection. |
Understanding Deepfakes in Identity Verification
Deepfakes pose a significant threat to identity verification by using AI-generated synthetic media to mimic legitimate users' facial features or voices, making biometric authentication systems vulnerable. Advanced neural networks create hyper-realistic video or audio of individuals, challenging conventional security protocols in areas like banking and border control. Recognizing the potential of deepfakes requires implementing multimodal verification techniques and AI-driven anomaly detection to enhance identity verification resilience.
Notable Deepfake Incidents in Financial Institutions
Notable deepfake incidents in financial institutions include the case where criminals used AI-generated voices to impersonate CEOs and request fraudulent wire transfers, resulting in millions of dollars lost. Another significant example involved deepfake videos simulating senior executives to manipulate employees into disclosing sensitive information or authorizing unauthorized transactions. These attacks highlight the vulnerabilities in identity verification systems that rely solely on voice or video authentication without multi-factor verification methods.
Deepfake Attacks on Remote Onboarding Processes
Deepfake attacks on remote onboarding processes exploit AI-generated synthetic media to impersonate legitimate users, compromising identity verification systems. These attacks manipulate facial recognition and voice authentication tools, enabling fraudsters to bypass security protocols and gain unauthorized access. Enhancing biometric liveness detection and multi-factor authentication is critical to mitigate the risks posed by deepfake-enabled identity fraud.
Real-World Cases: Deepfake Use in Banking Fraud
Deepfake technology has been exploited in banking fraud cases where attackers create realistic video or audio impersonations of legitimate customers to bypass identity verification systems. In 2020, a UK-based energy firm's CEO was impersonated via deepfake audio to authorize a fraudulent transfer of EUR220,000, highlighting the vulnerability of voice-based authentication. Financial institutions face increasing risks as deepfake attacks compromise biometric security measures, necessitating enhanced multi-factor verification protocols.
Deepfakes and Compromised Biometric Authentication
Deepfakes increasingly threaten identity verification by creating hyper-realistic synthetic videos that can bypass biometric authentication systems such as facial recognition and voice ID. These manipulated media exploit vulnerabilities in biometric algorithms, allowing attackers to impersonate legitimate users and gain unauthorized access to secure systems. Continuous advancements in AI-driven detection methods remain critical to countering this growing risk in security frameworks.
Social Engineering: Deepfakes in Customer Support Scams
Deepfake technology enables attackers to impersonate customers or employees convincingly during identity verification in customer support interactions, leading to unauthorized account access or data breaches. By syncing realistic facial movements and voice patterns, scammers manipulate support agents into disclosing sensitive information or processing fraudulent requests. This sophisticated form of social engineering exploits trust in visual and auditory cues, making traditional security measures like knowledge-based verification highly vulnerable.
Deepfake Manipulation of ID Documents and Videos
Deepfake manipulation in identity verification involves the creation of highly realistic forged ID documents and videos that can deceive biometric systems and human inspectors alike. These manipulated assets often use AI-generated facial reenactments to mimic authorized individuals, enabling unauthorized access or fraudulent transactions. Advances in deepfake technology necessitate robust multi-factor authentication and AI-driven detection tools to identify synthetic alterations in identity verification processes.
Legal Consequences of Deepfake Identity Fraud
Deepfake identity fraud in security systems can lead to severe legal consequences including criminal charges such as identity theft and fraud, resulting in fines and imprisonment. Regulatory bodies are increasingly enacting stringent laws to deter the malicious use of deepfake technology in identity verification processes. Victims of deepfake fraud may pursue civil lawsuits for damages, emphasizing the need for robust authentication protocols and advanced detection mechanisms in cybersecurity frameworks.
How Deepfakes Bypass Traditional Verification Tools
Deepfakes manipulate facial features and voice patterns with advanced AI, rendering traditional biometric systems like facial recognition and voice authentication increasingly vulnerable to fraud. These synthetic media exploit weaknesses in algorithms, bypassing security protocols by mimicking idiosyncratic behaviors and appearance cues that verification tools rely on. As deepfake technology evolves, it necessitates enhanced multi-factor authentication and real-time liveness detection to effectively counteract identity spoofing threats in security frameworks.
Lessons Learned: Preventing Deepfake Exploits in Identity Systems
Deepfake technology has exposed critical vulnerabilities in identity verification systems, highlighting the necessity for multi-factor authentication incorporating biometric liveness detection and behavioral analytics to prevent spoofing. Organizations must invest in AI-driven anomaly detection tools capable of identifying synthetic media artifacts that often evade traditional security measures. Continuous monitoring and regular updates to verification protocols are essential to adapt to evolving deepfake techniques and safeguard identity systems effectively.
example of deepfake in identity verification Infographic
 samplerz.com
samplerz.com