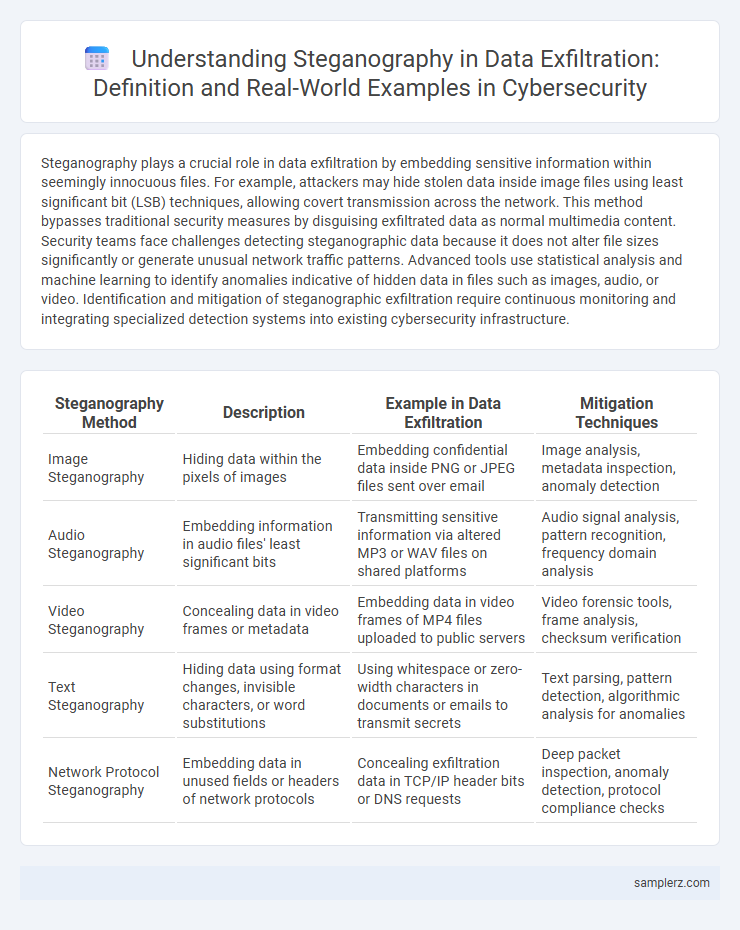
Steganography plays a crucial role in data exfiltration by embedding sensitive information within seemingly innocuous files. For example, attackers may hide stolen data inside image files using least significant bit (LSB) techniques, allowing covert transmission across the network. This method bypasses traditional security measures by disguising exfiltrated data as normal multimedia content. Security teams face challenges detecting steganographic data because it does not alter file sizes significantly or generate unusual network traffic patterns. Advanced tools use statistical analysis and machine learning to identify anomalies indicative of hidden data in files such as images, audio, or video. Identification and mitigation of steganographic exfiltration require continuous monitoring and integrating specialized detection systems into existing cybersecurity infrastructure.
Table of Comparison
| Steganography Method | Description | Example in Data Exfiltration | Mitigation Techniques |
|---|---|---|---|
| Image Steganography | Hiding data within the pixels of images | Embedding confidential data inside PNG or JPEG files sent over email | Image analysis, metadata inspection, anomaly detection |
| Audio Steganography | Embedding information in audio files' least significant bits | Transmitting sensitive information via altered MP3 or WAV files on shared platforms | Audio signal analysis, pattern recognition, frequency domain analysis |
| Video Steganography | Concealing data in video frames or metadata | Embedding data in video frames of MP4 files uploaded to public servers | Video forensic tools, frame analysis, checksum verification |
| Text Steganography | Hiding data using format changes, invisible characters, or word substitutions | Using whitespace or zero-width characters in documents or emails to transmit secrets | Text parsing, pattern detection, algorithmic analysis for anomalies |
| Network Protocol Steganography | Embedding data in unused fields or headers of network protocols | Concealing exfiltration data in TCP/IP header bits or DNS requests | Deep packet inspection, anomaly detection, protocol compliance checks |
Introduction to Steganography in Data Exfiltration
Steganography in data exfiltration involves hiding sensitive information within benign files such as images, audio, or video to evade detection by security systems. Attackers embed confidential data into seemingly innocuous media, enabling covert transfer across networks or external storage without raising suspicion. This technique exploits file format redundancies and compression artifacts to conceal data, making it a sophisticated method of bypassing traditional data loss prevention tools.
Image-Based Steganography in Cyber Espionage
Image-based steganography in cyber espionage involves embedding sensitive data within seemingly innocuous digital images to evade detection during data exfiltration. Attackers utilize techniques such as least significant bit (LSB) manipulation to conceal confidential information without altering the image's appearance, enabling covert communication channels. This method is prevalent in advanced persistent threats (APTs) where stealthy extraction of intellectual property or classified information is critical.
Audio File Steganography for Covert Data Theft
Audio file steganography hides sensitive data within sound files by embedding information into inaudible frequencies or subtle audio modifications, making detection difficult. Attackers use this technique to stealthily exfiltrate confidential data over network channels, bypassing traditional security measures such as firewalls and intrusion detection systems. This method exploits the high capacity and widespread use of audio formats like MP3 or WAV for covert communication in cyber espionage.
Video Steganography: Hiding Secrets in Plain Sight
Video steganography leverages the vast data capacity of video files to embed sensitive information within individual frames, making detection by traditional security tools challenging. Techniques such as modifying color values or slight pixel variations remain imperceptible to human eyes, allowing unauthorized data exfiltration without raising suspicion. Cyber attackers increasingly exploit video steganography to bypass firewalls and intrusion detection systems by hiding secrets in plain sight within high-volume multimedia traffic.
Network Protocol Steganography in Data Breaches
Network Protocol Steganography exploits unused or less monitored fields in legitimate network protocols like TCP/IP, HTTP, or DNS to covertly transmit sensitive data during breaches. Attackers embed confidential information within packet headers or payloads, evading traditional security tools and intrusion detection systems. This technique complicates detection efforts by blending exfiltrated data into normal network traffic patterns, increasing the risk and impact of data breaches.
Malicious Document Steganography Techniques
Malicious document steganography techniques embed hidden data within seemingly benign files such as Word, PDF, or Excel documents to facilitate covert data exfiltration. Attackers exploit metadata fields, embedded images, or macros to conceal sensitive information, enabling stealthy communication with external servers. Detection requires advanced forensic tools capable of analyzing document structure anomalies and extracting hidden payloads from these commonly trusted file formats.
Steganography via Social Media and Messaging Platforms
Steganography via social media and messaging platforms leverages image, audio, or video files to covertly embed sensitive data within seemingly innocuous messages, bypassing traditional security measures. Attackers exploit the widespread use and large file-sharing capacities of platforms like WhatsApp, Facebook, and Instagram to conceal exfiltrated data without arousing suspicion. Techniques such as embedding payloads in image pixels or audio spectrums facilitate stealthy data leakage, complicating detection by standard network monitoring tools.
Steganography in Malware for Data Exfiltration
Steganography in malware enables covert data exfiltration by embedding sensitive information within seemingly benign files, such as images or audio, evading traditional security detection methods. Advanced threats use this technique to discreetly transmit stolen credentials or confidential documents through encrypted channels, complicating incident response efforts. Detection relies on anomaly-based analysis and digital forensic tools designed to uncover hidden payloads within container files.
Case Studies: Real-World Steganographic Attacks
Real-world steganographic attacks have demonstrated how hackers embed malicious data within innocuous file formats like images, audio, or video to evade detection during data exfiltration. Notable case studies include the Operation Shady RAT campaign, where attackers concealed command-and-control instructions inside JPEG images, enabling prolonged espionage activities. These examples highlight the need for advanced anomaly detection systems capable of identifying hidden payloads in seemingly benign multimedia content.
Detecting and Preventing Steganographic Data Exfiltration
Detecting steganographic data exfiltration requires analyzing network traffic for anomalous patterns in file sizes, unusual payload entropy, and unexpected file format changes that may indicate hidden data. Preventing steganographic threats involves implementing advanced intrusion detection systems (IDS) equipped with machine learning algorithms designed to recognize covert communication channels and enforcing strict file monitoring policies. Employing data loss prevention (DLP) tools with steganalysis capabilities significantly reduces the risk of sensitive data leakage via image, audio, and video files used as covert carriers.
example of steganography in data exfiltration Infographic
 samplerz.com
samplerz.com