A wormhole attack in a wireless sensor network occurs when an attacker records packets at one location and tunnels them to another location, creating a shortcut in the network. This manipulation disrupts routing protocols, causing nodes to accept false route information and degrade network performance. The impact includes increased latency, packet loss, and potential data interception. For example, in a military surveillance system using wireless sensor nodes, adversaries can exploit a wormhole attack to mislead nodes about the shortest communication path. By establishing a low-latency link between two distant points, attackers create a wormhole that captures critical data streams, leading to compromised situational awareness. This attack highlights vulnerabilities in routing protocols like AODV or DSR under wormhole conditions.
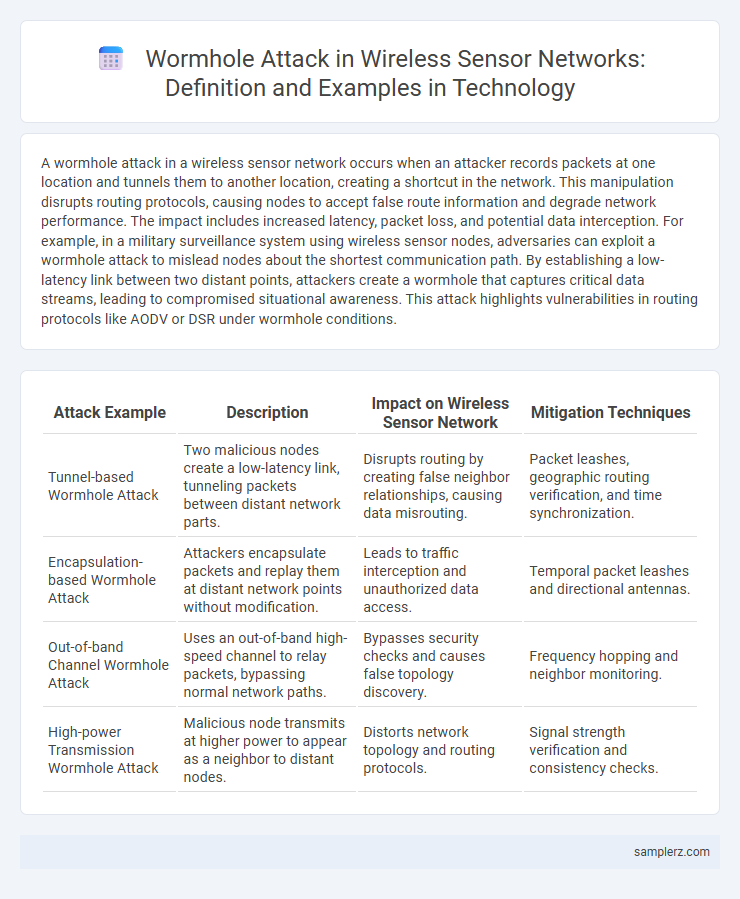
Table of Comparison
| Attack Example | Description | Impact on Wireless Sensor Network | Mitigation Techniques |
|---|---|---|---|
| Tunnel-based Wormhole Attack | Two malicious nodes create a low-latency link, tunneling packets between distant network parts. | Disrupts routing by creating false neighbor relationships, causing data misrouting. | Packet leashes, geographic routing verification, and time synchronization. |
| Encapsulation-based Wormhole Attack | Attackers encapsulate packets and replay them at distant network points without modification. | Leads to traffic interception and unauthorized data access. | Temporal packet leashes and directional antennas. |
| Out-of-band Channel Wormhole Attack | Uses an out-of-band high-speed channel to relay packets, bypassing normal network paths. | Bypasses security checks and causes false topology discovery. | Frequency hopping and neighbor monitoring. |
| High-power Transmission Wormhole Attack | Malicious node transmits at higher power to appear as a neighbor to distant nodes. | Distorts network topology and routing protocols. | Signal strength verification and consistency checks. |
Understanding Wormhole Attacks in Wireless Sensor Networks
Wormhole attacks in wireless sensor networks occur when an attacker records packets at one network location and tunnels them to another, creating a false network topology that disrupts routing. This attack can lead to serious consequences like data interception, packet drop, or network partitioning by misleading nodes about the shortest path. Detecting wormhole attacks involves using methods such as packet leash, time synchronization, and location-based techniques to ensure network integrity and security.
Key Features of Wormhole Attacks
Wormhole attacks in wireless sensor networks create a low-latency link, or wormhole tunnel, between two distant malicious nodes, enabling them to intercept and replay packets. This attack disrupts network topology by misleading nodes about the shortest path, causing routing distortions and increased latency. Key features include packet encapsulation, out-of-band communication channels, and a significant impact on network routing and data integrity.
Real-World Case Studies of Wormhole Attacks
Wormhole attacks in wireless sensor networks have been demonstrated in real-world case studies such as the deployment in military surveillance systems where attackers create low-latency links between distant nodes to disrupt routing protocols. In smart grid networks, adversaries utilized wormholes to manipulate data transmission paths, causing false readings and network partitioning. These incidents highlight vulnerabilities in geographic routing protocols and emphasize the need for robust hop-count and time-of-flight based detection mechanisms.
Classic Example: Packet Tunneling in Sensor Networks
In wireless sensor networks, a classic example of a wormhole attack involves packet tunneling, where an attacker records packets at one location and tunnels them to another location through a low-latency link. This creates a false impression of shorter distance between nodes, disrupting routing protocols and causing data to be misrouted or lost. Such attacks significantly degrade network performance and compromise data integrity by exploiting the network's vulnerability to out-of-band link creation.
Effects of Wormhole Attacks on Network Routing
Wormhole attacks in wireless sensor networks create a direct tunneling link between two distant nodes, disrupting the normal routing protocol by presenting a false shortest path. This manipulation causes legitimate data packets to be rerouted through the attacker-controlled tunnel, leading to increased latency, loss of packet integrity, and potential network partitioning. As a result, network routing efficiency is severely compromised, affecting overall sensor communication and data reliability.
Scenario: Disrupted Data Transmission via Wormhole Attack
In a wireless sensor network, a wormhole attack occurs when an attacker records packets at one location and tunnels them to another, creating a shortcut that disrupts normal routing paths. This manipulation causes disrupted data transmission, leading to packet loss, increased latency, and compromised network integrity. Sensor nodes end up communicating through the malicious tunnel instead of legitimate multi-hop routes, severely degrading network performance and reliability.
Simulation-Based Example in a Smart City Network
A simulation-based example of a wormhole attack in a wireless sensor network within a smart city involves malicious nodes creating a low-latency link to tunnel packets between distant locations, disrupting routing protocols and data integrity. In simulated smart city environments, this attack causes severe packet loss and increased latency in traffic management and environmental monitoring sensors. Network simulators like NS-3 demonstrate how wormhole tunnels compromise sensor data, highlighting vulnerabilities in smart city infrastructure reliant on wireless communication.
Practical Impacts: Energy Drain from Wormhole Exploits
Wormhole attacks in wireless sensor networks cause severe energy drain by repeatedly relaying packets between nodes, forcing sensors to expend excessive power on unnecessary communication. This continuous packet forwarding depletes battery life rapidly, shortening the operational lifespan of the network and leading to frequent node failures. Energy exhaustion from wormhole exploits significantly degrades network performance and reliability in critical applications like environmental monitoring and military surveillance.
Attack Demonstration: Colluding Nodes in Sensor Node Cluster
In a wireless sensor network, a wormhole attack can be demonstrated by two colluding nodes within a sensor node cluster that create a low-latency link to relay packets between distant parts of the network. These malicious nodes capture, tunnel, and replay messages, disrupting routing protocols by making nodes believe they are neighbors. This attack leads to network topology distortion, packet loss, and degradation of data integrity in sensor communications.
Lessons Learned from Wormhole Attack Incidents
Wormhole attacks in wireless sensor networks reveal critical vulnerabilities in routing protocols, where attackers create a low-latency link between distant nodes to disrupt network topology. Lessons learned emphasize the necessity of implementing robust localization techniques and secure neighbor discovery methods to detect and prevent such tunneling threats. Enhancing authentication and time synchronization mechanisms significantly reduces the risk of tunnel-based exploits in sensor network communications.
example of wormhole attack in wireless sensor network Infographic
 samplerz.com
samplerz.com