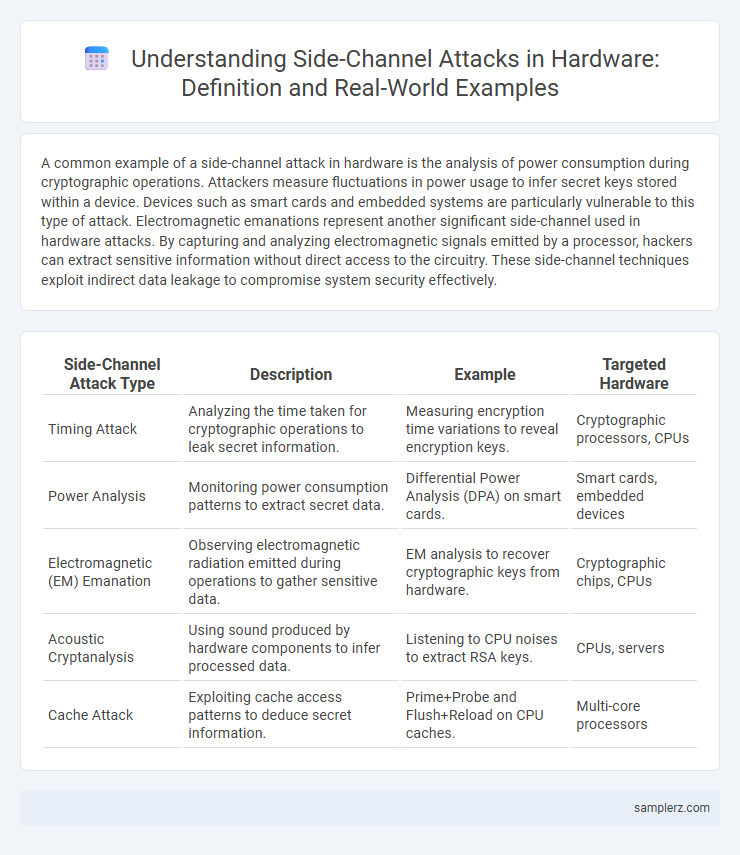
A common example of a side-channel attack in hardware is the analysis of power consumption during cryptographic operations. Attackers measure fluctuations in power usage to infer secret keys stored within a device. Devices such as smart cards and embedded systems are particularly vulnerable to this type of attack. Electromagnetic emanations represent another significant side-channel used in hardware attacks. By capturing and analyzing electromagnetic signals emitted by a processor, hackers can extract sensitive information without direct access to the circuitry. These side-channel techniques exploit indirect data leakage to compromise system security effectively.
Table of Comparison
| Side-Channel Attack Type | Description | Example | Targeted Hardware |
|---|---|---|---|
| Timing Attack | Analyzing the time taken for cryptographic operations to leak secret information. | Measuring encryption time variations to reveal encryption keys. | Cryptographic processors, CPUs |
| Power Analysis | Monitoring power consumption patterns to extract secret data. | Differential Power Analysis (DPA) on smart cards. | Smart cards, embedded devices |
| Electromagnetic (EM) Emanation | Observing electromagnetic radiation emitted during operations to gather sensitive data. | EM analysis to recover cryptographic keys from hardware. | Cryptographic chips, CPUs |
| Acoustic Cryptanalysis | Using sound produced by hardware components to infer processed data. | Listening to CPU noises to extract RSA keys. | CPUs, servers |
| Cache Attack | Exploiting cache access patterns to deduce secret information. | Prime+Probe and Flush+Reload on CPU caches. | Multi-core processors |
Understanding Side-Channel Attacks in Hardware
Side-channel attacks in hardware exploit indirect information leakage such as power consumption, electromagnetic emissions, or timing variations to extract sensitive data from devices. An example includes Differential Power Analysis (DPA), where attackers analyze variations in power usage during cryptographic operations to recover secret keys. Understanding these side-channel vulnerabilities is critical for designing robust hardware security countermeasures like masking and noise introduction.
Power Analysis: Revealing Secrets Through Consumption
Power analysis is a prevalent side-channel attack in hardware security that exploits variations in a device's power consumption to extract cryptographic keys and sensitive data. Differential Power Analysis (DPA) measures subtle power fluctuations during encryption operations, revealing secret keys by statistically analyzing multiple power traces. This technique targets microcontrollers and smart cards, posing significant risks to embedded systems and secure hardware modules.
Electromagnetic Emanations as Attack Vectors
Electromagnetic emanations from hardware components serve as critical side-channel attack vectors, leaking sensitive information such as cryptographic keys and data processed within secure environments. Attackers use specialized equipment to capture and analyze these emissions, exploiting unintentional electromagnetic signals generated by processors, memory modules, or communication interfaces. Mitigation techniques include shielding, signal filtering, and algorithmic noise injection to obscure or minimize exploitable electromagnetic side-channel data in embedded systems and secure hardware.
Timing Attacks: Exploiting Execution Delays
Timing attacks exploit variations in the time taken by hardware to execute cryptographic algorithms, revealing sensitive information like encryption keys. By precisely measuring execution delays during operations on CPUs or embedded devices, attackers can infer secret data without direct access to the system. This side-channel vulnerability is critical in microcontrollers and secure processors where timing differences correlate strongly with processed data values.
Cache-Based Side-Channel Techniques
Cache-based side-channel attacks exploit timing differences in CPU cache accesses to leak sensitive information such as cryptographic keys. Techniques like Prime+Probe and Flush+Reload monitor cache sets to infer victim processes' memory access patterns. These attacks are particularly effective against shared hardware environments like cloud servers where adversaries can co-locate with target virtual machines.
Acoustic Attacks: Listening to Hardware Operations
Acoustic attacks exploit the sound emitted by electronic components during operations to extract sensitive information like cryptographic keys. Microphones capture subtle vibrations or electromagnetic interference from CPUs or GPUs, allowing attackers to analyze and reconstruct processed data. Research demonstrates that these side-channel attacks can bypass traditional security measures, highlighting the need for enhanced hardware shielding and noise mitigation techniques.
Fault Injection: Manipulating Hardware Responses
Fault Injection is a side-channel attack technique that manipulates hardware responses by deliberately inducing faults to disrupt normal operation, often targeting microcontrollers and cryptographic modules. Techniques like voltage glitching, clock glitching, and laser fault injection force transient errors, revealing sensitive information such as encryption keys or firmware code. Successful fault injection exploits hardware vulnerabilities in embedded systems, emphasizing the importance of robust fault detection and error correction mechanisms in secure hardware design.
Laser and Optical Side-Channel Methods
Laser and optical side-channel methods in hardware attacks exploit light emissions and reflections from electronic components to extract sensitive information. Techniques such as laser fault injection precisely alter a device's behavior by injecting faults with focused laser beams, revealing secret keys or data. Optical power analysis captures light intensity variations during device operations, enabling attackers to infer cryptographic processes without physical tampering.
Temperature Variations and Information Leakage
Temperature variations in hardware during side-channel attacks can cause fluctuations in power consumption and electromagnetic emissions, enabling attackers to infer sensitive data such as cryptographic keys. Thermal imaging techniques detect minute heat differences in processors, revealing computation patterns linked to secret information. These temperature-induced side-channels pose a significant risk to hardware security in environments requiring high confidentiality.
Real-World Cases of Hardware Side-Channel Exploits
Real-world cases of hardware side-channel exploits include the Spectre and Meltdown vulnerabilities, which leverage speculative execution to access sensitive data across trust boundaries. Another notable example is the Rowhammer attack, which induces bit flips in DRAM to escalate privileges or extract cryptographic keys. These exploits demonstrate the critical impact of hardware-level side channels in compromising system security.
example of side-channel in hardware attack Infographic
 samplerz.com
samplerz.com