Polymorphism in antivirus technology refers to the ability of malware to change its code or structure while maintaining its original functionality. This technique makes detection difficult for traditional signature-based antivirus software because each variant appears unique. Antivirus programs must rely on heuristic analysis and behavior-based detection to identify these evolving threats effectively. An example of polymorphism in antivirus detection is malware that encrypts its payload with a different key each time it replicates. The antivirus software scans for suspicious behaviors and patterns rather than fixed code signatures. This approach enhances detection rates and helps prevent polymorphic malware from evading security measures.
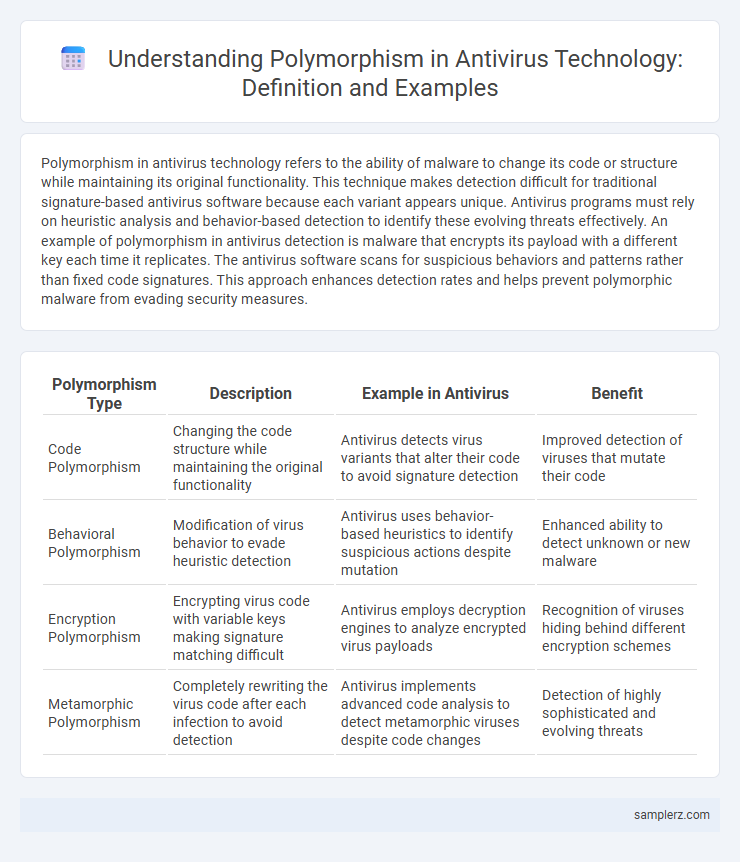
Table of Comparison
| Polymorphism Type | Description | Example in Antivirus | Benefit |
|---|---|---|---|
| Code Polymorphism | Changing the code structure while maintaining the original functionality | Antivirus detects virus variants that alter their code to avoid signature detection | Improved detection of viruses that mutate their code |
| Behavioral Polymorphism | Modification of virus behavior to evade heuristic detection | Antivirus uses behavior-based heuristics to identify suspicious actions despite mutation | Enhanced ability to detect unknown or new malware |
| Encryption Polymorphism | Encrypting virus code with variable keys making signature matching difficult | Antivirus employs decryption engines to analyze encrypted virus payloads | Recognition of viruses hiding behind different encryption schemes |
| Metamorphic Polymorphism | Completely rewriting the virus code after each infection to avoid detection | Antivirus implements advanced code analysis to detect metamorphic viruses despite code changes | Detection of highly sophisticated and evolving threats |
Understanding Polymorphism in Antivirus Technology
Polymorphism in antivirus technology involves the ability of malware to change its code structure while retaining its original functionality, making detection by traditional signature-based methods challenging. Antivirus software uses heuristic and behavior-based analysis to identify polymorphic viruses by examining their actions rather than relying solely on static code signatures. This dynamic approach enhances malware detection rates and improves protection against rapidly evolving threats.
Real-World Examples of Polymorphic Malware
Polymorphic malware like the Storm Worm constantly alters its code to evade detection by traditional antivirus programs using signature-based scanning. The infamous Zeus Trojan employs polymorphism by encrypting its payload with varying keys, enabling it to persist undetected across multiple systems. These real-world examples demonstrate how polymorphic techniques complicate malware analysis and demand advanced heuristic and behavior-based antivirus solutions.
How Antivirus Software Detects Polymorphic Threats
Antivirus software detects polymorphic threats by analyzing code behavior and employing heuristic algorithms that identify suspicious patterns despite constant code mutations. Machine learning models enhance detection by recognizing anomalies in executable instructions and runtime behavior, even as the malware continuously alters its code signature. Signature-less detection methods focus on scanning for encrypted payloads, unpacking routines, and abnormal API calls, enabling identification of polymorphic viruses that evade traditional signature-based filters.
The Evolution of Polymorphic Techniques in Cybersecurity
Polymorphic antivirus techniques continuously evolve to counteract increasingly sophisticated malware by altering their code signatures while maintaining core functionalities, complicating detection efforts. Modern polymorphic engines employ advanced encryption algorithms and dynamic code mutation strategies, enabling malware to evade static signature-based scanning. This evolutionary approach in cybersecurity demands adaptive machine learning-based detection systems that analyze behavioral patterns rather than relying solely on fixed virus signatures.
Signature-Based vs. Behavioral Detection for Polymorphic Viruses
Signature-based detection in antivirus software relies on identifying known code patterns specific to polymorphic viruses, enabling rapid recognition of previously cataloged threats. Behavioral detection monitors the actions and system changes induced by polymorphic viruses, effectively identifying new or altered variants that evade signature matching. Combining both methods enhances security by addressing the limitations of signature-based systems in detecting evolving polymorphic malware.
Famous Polymorphic Viruses and Their Impact on Antivirus Solutions
Famous polymorphic viruses like the Whale virus and the Marburg virus employ encryption and mutation techniques to evade traditional antivirus detection by constantly changing their code structure. These viruses significantly impacted antivirus solutions by forcing the development of heuristic analysis and behavior-based detection methods to identify malicious patterns beyond signature recognition. Consequently, antivirus software evolved to incorporate advanced machine learning algorithms and real-time monitoring to counteract the dynamic nature of polymorphic threats effectively.
Advanced Heuristics in Combating Polymorphic Malware
Advanced heuristics in antivirus software analyze code behavior and structural patterns rather than relying solely on signature matching, enabling detection of polymorphic malware that dynamically alters its code to evade traditional scans. By monitoring runtime anomalies and employing machine learning algorithms, these heuristics identify suspicious instructions and mutations indicative of polymorphic threats. This approach enhances malware detection accuracy, effectively countering evasive polymorphic viruses through behavioral analysis and adaptive pattern recognition.
Anti-Polymorphic Strategies Used by Modern Antivirus Programs
Modern antivirus programs employ anti-polymorphic strategies such as behavior-based detection, which analyzes suspicious code execution patterns instead of relying solely on signatures. Machine learning algorithms enhance detection accuracy by identifying polymorphic malware variants through feature extraction and anomaly detection. Memory scanning techniques are also utilized to inspect runtime code and bypass obfuscation methods commonly used by polymorphic viruses.
Machine Learning and Polymorphism in Antivirus Solutions
Polymorphism in antivirus leverages Machine Learning algorithms to detect and adapt to evolving malware variants by analyzing behavior patterns rather than relying solely on static signatures. This approach enables the identification of polymorphic malware that continuously modifies its code to evade traditional detection methods. Machine Learning models enhance real-time threat detection accuracy, improving the ability of antivirus solutions to respond to unknown or zero-day attacks effectively.
Future Trends: Polymorphism and Next-Gen Antivirus Technologies
Future trends in antivirus technology emphasize polymorphism to enhance malware detection by enabling software to adapt and evolve its code signatures dynamically, thwarting traditional signature-based attacks. Next-generation antivirus tools integrate machine learning algorithms with polymorphic capabilities to identify and neutralize emerging threats in real-time, improving overall cybersecurity resilience. The continuous development of polymorphic techniques in threat detection promises more robust defense mechanisms against sophisticated malware and zero-day exploits.
example of polymorphism in antivirus Infographic
 samplerz.com
samplerz.com