Fuzzing is a software testing technique used to identify security vulnerabilities and bugs by inputting large volumes of random or semi-random data, called fuzz, into a program. This method helps detect issues such as memory leaks, crashes, and assertion failures by observing how the software behaves under unexpected or malformed inputs. Tools like American Fuzzy Lop (AFL) and libFuzzer automate the fuzzing process, providing extensive coverage with minimal manual intervention. Fuzzing targets core components of software systems, including APIs, file parsers, and network protocols, revealing weaknesses before attackers can exploit them. It generates diverse data patterns to simulate real-world attacks, assisting developers in strengthening the robustness of their applications. Data collected from fuzzing campaigns includes crash logs, code coverage details, and execution traces, which guide debugging and vulnerability remediation efforts.
Table of Comparison
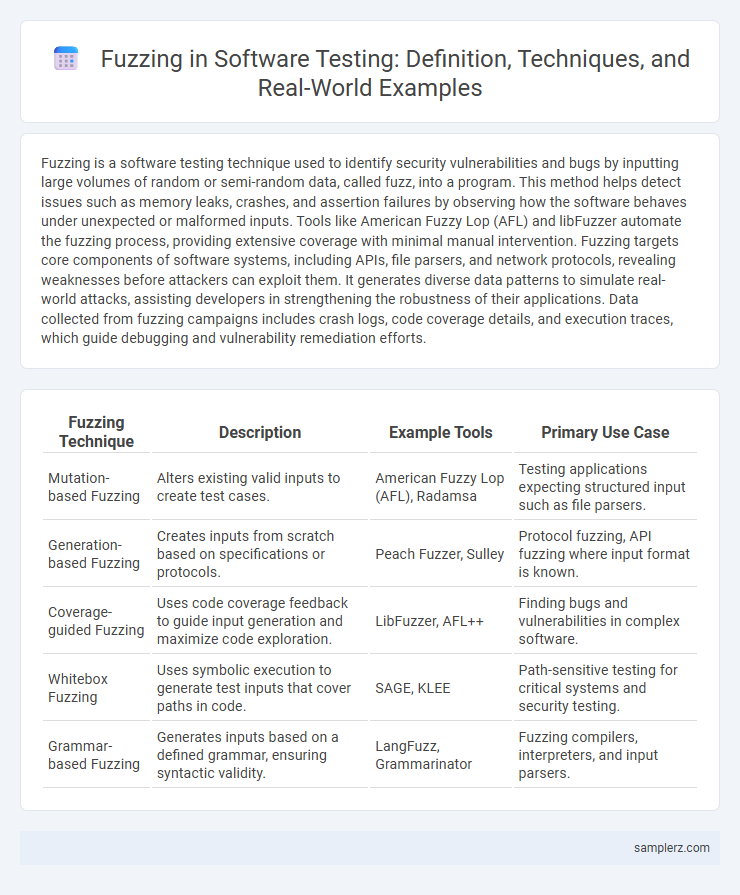
| Fuzzing Technique | Description | Example Tools | Primary Use Case |
|---|---|---|---|
| Mutation-based Fuzzing | Alters existing valid inputs to create test cases. | American Fuzzy Lop (AFL), Radamsa | Testing applications expecting structured input such as file parsers. |
| Generation-based Fuzzing | Creates inputs from scratch based on specifications or protocols. | Peach Fuzzer, Sulley | Protocol fuzzing, API fuzzing where input format is known. |
| Coverage-guided Fuzzing | Uses code coverage feedback to guide input generation and maximize code exploration. | LibFuzzer, AFL++ | Finding bugs and vulnerabilities in complex software. |
| Whitebox Fuzzing | Uses symbolic execution to generate test inputs that cover paths in code. | SAGE, KLEE | Path-sensitive testing for critical systems and security testing. |
| Grammar-based Fuzzing | Generates inputs based on a defined grammar, ensuring syntactic validity. | LangFuzz, Grammarinator | Fuzzing compilers, interpreters, and input parsers. |
Introduction to Fuzzing in Software Testing
Fuzzing in software testing is an automated technique that involves inputting invalid, unexpected, or random data into a program to discover security vulnerabilities and software bugs. By continuously generating diverse test cases, fuzzing helps identify memory leaks, crashes, and logic errors that traditional testing methods might overlook. Popular fuzzing tools like AFL (American Fuzzy Lop) and libFuzzer enhance software robustness by simulating real-world attack scenarios during the development lifecycle.
Key Types of Fuzzing Techniques
Key types of fuzzing techniques include mutation-based fuzzing, which involves modifying existing inputs to generate test cases, and generation-based fuzzing, which creates inputs from scratch based on specifications or formats. Coverage-guided fuzzing leverages code coverage data to prioritize inputs that explore new execution paths, enhancing detection of vulnerabilities. Other methods, such as grammar-based fuzzing, utilize formal grammars to produce syntactically valid inputs, improving the effectiveness of testing complex protocols or file formats.
Real-World Examples of Fuzzing Tools
AFL (American Fuzzy Lop) is a widely used fuzzing tool that identifies vulnerabilities by generating random inputs for software testing, effectively uncovering buffer overflows and memory corruption bugs. Google's OSS-Fuzz integrates AFL and other fuzzers to provide continuous fuzz testing for open-source projects, significantly improving security for widely used libraries such as Chromium and OpenSSL. Microsoft's Security Risk Detection uses fuzzing technology to analyze Windows components and third-party software, helping to detect critical security flaws before they reach end-users.
Case Study: Fuzzing in Web Application Testing
Fuzzing in web application testing involves automatically injecting malformed or unexpected inputs to identify security vulnerabilities and bugs. A notable case study includes testing the Open Web Application Security Project's (OWASP) Juice Shop, where fuzzing revealed multiple injection flaws and cross-site scripting (XSS) vulnerabilities. This method enhances the detection of hidden security issues by simulating real-world attack patterns against input fields, APIs, and session management components.
Fuzzing Example in Network Protocol Testing
Fuzzing in network protocol testing involves sending malformed or random data packets to target systems to identify vulnerabilities and crashes. Tools like AFL (American Fuzzy Lop) and Peach Fuzzer automate this process by generating diverse test cases for protocols such as TCP/IP, HTTP, and DNS. This method helps uncover buffer overflows, memory leaks, and improper input validation in network devices and software.
Fuzzing for Security Vulnerability Detection
Fuzzing for security vulnerability detection involves automatically generating and inputting random or malformed data into software to uncover unexpected crashes, memory leaks, or security flaws. Tools like AFL (American Fuzzy Lop) and libFuzzer systematically probe program interfaces, discovering buffer overflows, use-after-free errors, and SQL injection vulnerabilities. This technique enhances software robustness by identifying critical security weaknesses before attackers can exploit them.
Automation of Fuzz Testing: Practical Examples
Automation of fuzz testing enhances software security by systematically generating random inputs to identify vulnerabilities and crashes. Tools like AFL (American Fuzzy Lop) and libFuzzer automate this process by integrating with continuous integration pipelines, enabling extensive coverage with minimal manual intervention. Real-world applications include automated fuzzing of web browsers, network protocols, and file parsers, accelerating the discovery of critical security flaws.
Fuzzing in Open Source Projects: Success Stories
Fuzzing in open source projects like LLVM and Mozilla Firefox has uncovered critical vulnerabilities, enhancing software security through automated, random input testing. These success stories demonstrate how fuzzing tools such as AFL (American Fuzzy Lop) and libFuzzer identify memory corruption and logic errors effectively. Open source fuzzing frameworks foster community collaboration, accelerating the detection and resolution of security flaws.
Challenges Encountered During Fuzzing
Fuzzing in software testing often encounters challenges such as generating meaningful inputs that effectively trigger rare edge cases and detecting subtle bugs buried deep within complex code paths. Handling highly stateful applications or protocols complicates the fuzzing process due to the need for maintaining context across multiple inputs. Performance limitations and false positives further hinder the accuracy and efficiency of fuzzing tools in identifying genuine security vulnerabilities.
Best Practices for Implementing Fuzz Testing
Fuzz testing involves automatically generating unexpected or random inputs to identify vulnerabilities and software bugs, particularly in security-critical applications. Best practices for implementing fuzz testing include selecting diverse input formats, integrating coverage-guided fuzzers like AFL or libFuzzer, and continuously monitoring test results for anomalies to improve defect detection. Incorporating automated triage and prioritization helps efficiently manage vulnerability reports, maximizing the effectiveness of fuzz testing in continuous integration pipelines.
example of fuzzing in testing Infographic
 samplerz.com
samplerz.com