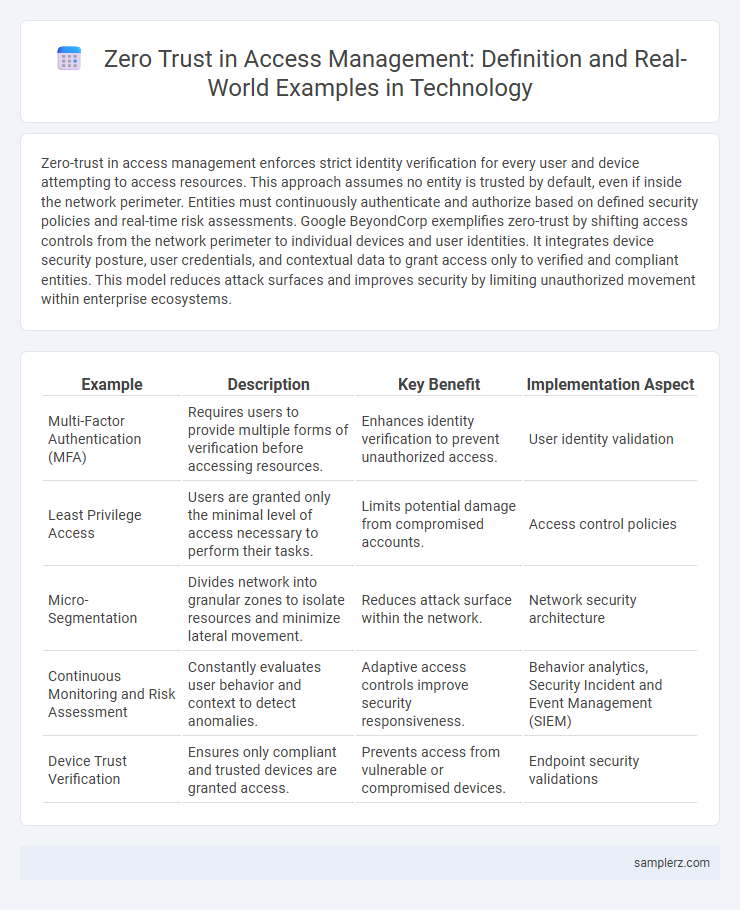
Zero-trust in access management enforces strict identity verification for every user and device attempting to access resources. This approach assumes no entity is trusted by default, even if inside the network perimeter. Entities must continuously authenticate and authorize based on defined security policies and real-time risk assessments. Google BeyondCorp exemplifies zero-trust by shifting access controls from the network perimeter to individual devices and user identities. It integrates device security posture, user credentials, and contextual data to grant access only to verified and compliant entities. This model reduces attack surfaces and improves security by limiting unauthorized movement within enterprise ecosystems.
Table of Comparison
| Example | Description | Key Benefit | Implementation Aspect |
|---|---|---|---|
| Multi-Factor Authentication (MFA) | Requires users to provide multiple forms of verification before accessing resources. | Enhances identity verification to prevent unauthorized access. | User identity validation |
| Least Privilege Access | Users are granted only the minimal level of access necessary to perform their tasks. | Limits potential damage from compromised accounts. | Access control policies |
| Micro-Segmentation | Divides network into granular zones to isolate resources and minimize lateral movement. | Reduces attack surface within the network. | Network security architecture |
| Continuous Monitoring and Risk Assessment | Constantly evaluates user behavior and context to detect anomalies. | Adaptive access controls improve security responsiveness. | Behavior analytics, Security Incident and Event Management (SIEM) |
| Device Trust Verification | Ensures only compliant and trusted devices are granted access. | Prevents access from vulnerable or compromised devices. | Endpoint security validations |
Understanding Zero-Trust in Access Management
Zero-trust in access management enforces strict verification for every user and device attempting to access network resources, regardless of their location. This approach requires continuous authentication, authorization, and validation based on least-privilege principles to mitigate potential security breaches. Implementations often include multi-factor authentication (MFA), micro-segmentation, and real-time monitoring to ensure that only legitimate entities gain access at any time.
Key Principles of Zero-Trust Security
Zero-trust security in access management eliminates implicit trust by enforcing strict identity verification for every user and device attempting to access resources. Key principles include continuous authentication, least privilege access, and micro-segmentation to minimize the attack surface and contain potential breaches. Implementation relies on multi-factor authentication (MFA), dynamic policy enforcement, and real-time monitoring to ensure secure, context-aware access control.
Multi-Factor Authentication as a Zero-Trust Example
Multi-Factor Authentication (MFA) exemplifies zero-trust in access management by requiring users to verify their identity through multiple independent credentials, such as passwords, biometrics, and one-time codes. This layered security approach minimizes the risk of unauthorized access even if one authentication factor is compromised. Major technology firms like Microsoft and Google integrate MFA within their zero-trust frameworks to enhance protection against phishing and credential theft.
Role-Based Access Control in Zero-Trust Models
Role-Based Access Control (RBAC) is a pivotal technology in zero-trust access management, enforcing strict user permissions based on defined roles to minimize unauthorized access. In zero-trust models, RBAC ensures that each user is granted the least privilege necessary, dynamically adjusting access rights as tasks or roles evolve. Integrating RBAC with continuous authentication and real-time monitoring enhances security by validating identity and access context at every interaction point.
Conditional Access Policies Implementation
Conditional Access Policies implementation in zero-trust access management enforces strict identity verification and device compliance before granting resource access, reducing risk from unauthorized users. Microsoft Azure AD utilizes conditional access to evaluate user location, device health, and user risk level, ensuring adaptive access controls dynamically respond to threats. This granular policy approach limits lateral movement and data exposure across cloud and on-premises environments, strengthening overall security posture.
Least Privilege Access in Zero-Trust Frameworks
Least Privilege Access in zero-trust frameworks enforces strict access controls by granting users only the minimal permissions necessary to perform their tasks, reducing the risk of lateral movement in case of a breach. Technologies like micro-segmentation and continuous authentication ensure that access is dynamically verified and limited, bolstering the security posture. This approach is widely implemented in enterprises using identity and access management (IAM) solutions integrated with multi-factor authentication (MFA) and adaptive policies.
Micro-Segmentation for Network Security
Micro-segmentation enhances zero-trust access management by dividing a network into granular zones, ensuring that users and devices access only the specific segments necessary for their roles. This approach minimizes lateral movement of threats within the network, enforcing strict access controls based on identity, device posture, and context. Leading implementations in data centers and cloud environments leverage micro-segmentation to protect critical assets and maintain continuous verification aligned with zero-trust principles.
Continuous User Verification Techniques
Continuous user verification techniques in zero-trust access management employ behavioral biometrics, adaptive risk scoring, and real-time context analysis to ensure persistent authentication throughout a session. These methods analyze typing patterns, geolocation, device posture, and network anomalies to detect and prevent unauthorized access dynamically. Integrating machine learning algorithms enhances the accuracy of identifying legitimate users, reducing reliance on static credentials and mitigating insider threats.
Real-Time Monitoring and Automated Threat Response
Real-time monitoring in zero-trust access management continuously analyzes user behavior and network activity to detect anomalies, ensuring immediate identification of potential security threats. Automated threat response systems instantly isolate compromised accounts and revoke access privileges without human intervention, minimizing the attack surface. This approach integrates AI-driven analytics and machine learning to enhance threat detection accuracy and accelerate remediation efforts in dynamic IT environments.
Zero-Trust Architecture Success Stories in Organizations
Microsoft implemented Zero-Trust Architecture by enforcing strict identity verification, least-privilege access, and continuous monitoring, resulting in a 50% reduction in security breaches within one year. Google's BeyondCorp framework eliminated traditional VPNs, enabling secure remote access and improving operational efficiency across its global workforce. The healthcare provider Mayo Clinic adopted Zero-Trust principles to protect sensitive patient data, achieving compliance with HIPAA while reducing insider threat incidents by 40%.
example of zero-trust in access management Infographic
 samplerz.com
samplerz.com