Polymorphism in code obfuscation involves modifying the code's structure while preserving its original functionality to evade detection by reverse engineering tools. For example, a polymorphic virus might change its encryption key and decryptor algorithm upon each infection, making signature-based detection ineffective. This technique constantly generates different code variants that achieve the same operational result, increasing the difficulty of static analysis. In programming, polymorphism allows creating multiple forms of a function or method, which can be leveraged for obfuscation by embedding diverse implementations under a unified interface. Different methods with identical signatures can alter control flow and data handling patterns without changing the output. As a result, reverse engineers face challenges discerning the actual program logic due to the dynamic and varied nature of the code's execution paths.
Table of Comparison
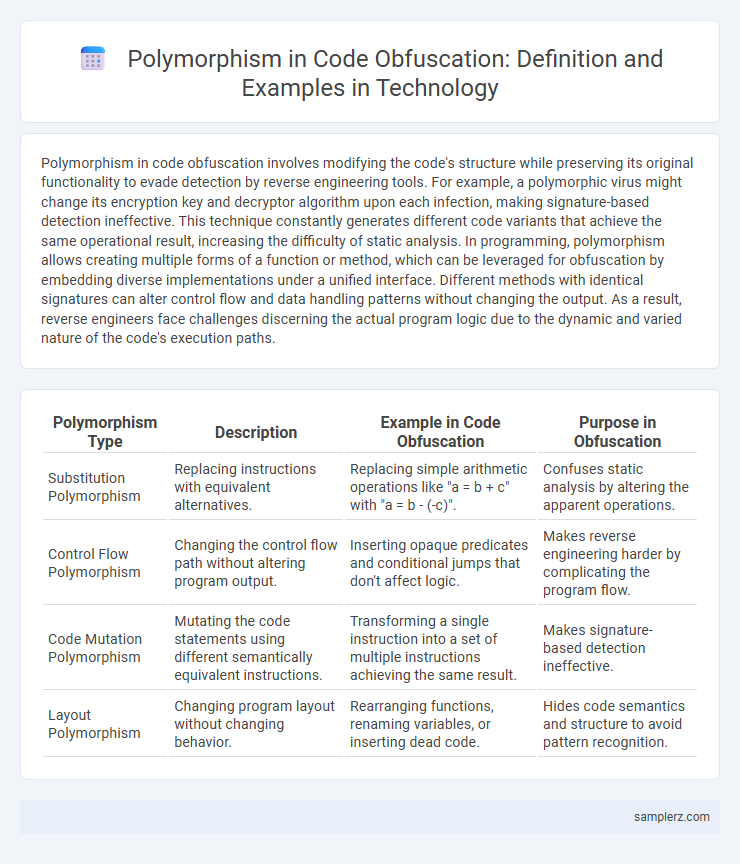
| Polymorphism Type | Description | Example in Code Obfuscation | Purpose in Obfuscation |
|---|---|---|---|
| Substitution Polymorphism | Replacing instructions with equivalent alternatives. | Replacing simple arithmetic operations like "a = b + c" with "a = b - (-c)". | Confuses static analysis by altering the apparent operations. |
| Control Flow Polymorphism | Changing the control flow path without altering program output. | Inserting opaque predicates and conditional jumps that don't affect logic. | Makes reverse engineering harder by complicating the program flow. |
| Code Mutation Polymorphism | Mutating the code statements using different semantically equivalent instructions. | Transforming a single instruction into a set of multiple instructions achieving the same result. | Makes signature-based detection ineffective. |
| Layout Polymorphism | Changing program layout without changing behavior. | Rearranging functions, renaming variables, or inserting dead code. | Hides code semantics and structure to avoid pattern recognition. |
Introduction to Polymorphism in Code Obfuscation
Polymorphism in code obfuscation refers to the technique where malware or software continuously changes its code structure while retaining its original functionality to evade detection by security tools. This method relies on generating varied but semantically equivalent code snippets using different instructions, control flows, or register usage, making static analysis ineffective. By implementing polymorphic engines, attackers ensure that each iteration of the obfuscated code appears unique, enhancing stealth against signature-based antivirus systems.
How Polymorphism Enhances Software Security
Polymorphism in code obfuscation transforms program instructions dynamically, making static analysis and reverse engineering extremely difficult for attackers. By generating multiple functionally equivalent but syntactically different code variants, polymorphism hinders pattern recognition and signature-based detection in malware analysis. This technique significantly enhances software security by increasing resistance against decompilation, tampering, and automated vulnerability scanning tools.
Common Polymorphic Techniques Used in Code Obfuscation
Common polymorphic techniques used in code obfuscation include instruction substitution, where equivalent instructions replace original code to evade detection. Control flow flattening modifies the program's structure by breaking and rearranging basic blocks, complicating static analysis. Additionally, register renaming and dynamic code generation alter code appearance each execution, enhancing resistance to signature-based malware scanners.
Real-World Examples of Polymorphic Obfuscation
Real-world examples of polymorphic obfuscation include malware like the Zeus Trojan, which dynamically changes its code structure to evade detection by antivirus software. Polymorphic viruses use algorithms to encrypt their payload with different keys each time they propagate, making static signature analysis ineffective. Techniques such as instruction substitution, register reassignment, and control flow alteration exemplify polymorphic obfuscation in practice, significantly enhancing the stealth and resilience of malicious programs.
Implementing Polymorphism with Encryption Algorithms
Implementing polymorphism in code obfuscation leverages multiple encryption algorithms dynamically to conceal program logic from reverse engineering tools. By abstracting encryption methods such as AES, RSA, and Blowfish behind a unified interface, obfuscators can switch algorithms at runtime, increasing complexity and resilience against static analysis. This polymorphic approach ensures encrypted payloads transform continuously, thwarting pattern recognition and enhancing software security.
Polymorphic Code in Malware and Antivirus Evasion
Polymorphic code in malware continuously alters its underlying code structure while maintaining original functionality, making signature-based antivirus detection ineffective. This technique uses polymorphism by encrypting the payload with a changing key and incorporating a decryptor that mutates in each iteration, significantly complicating pattern recognition. Antivirus solutions respond with heuristic and behavior-based analysis, but polymorphic malware remains a persistent challenge in cybersecurity defense.
Case Study: Polymorphic Obfuscation in JavaScript
Polymorphic obfuscation in JavaScript leverages dynamic code transformation techniques to evade static analysis by modifying the code structure while preserving functionality, such as altering variable names and control flows during runtime. This technique exemplifies polymorphism by generating unique code variants each time the script executes, complicating detection by anti-malware tools. Case studies demonstrate how polymorphic JavaScript obfuscators employ self-modifying code and encryption to enhance security and resist reverse engineering.
Benefits and Drawbacks of Using Polymorphism for Obfuscation
Polymorphism in code obfuscation helps to disguise program logic by dynamically altering method implementations, making reverse engineering significantly harder and enhancing software protection. This technique increases code complexity and resilience against automated deobfuscation tools, but it can also introduce performance overhead and complicate debugging and maintenance. Balancing the security benefits against potential system slowdowns is essential when implementing polymorphic obfuscation in critical applications.
Tools and Frameworks for Polymorphic Code Generation
Tools like Metasploit and Veil-Evasion excel in polymorphic code generation by automatically modifying payloads to evade signature-based detection. Frameworks such as Invoke-Obfuscation empower developers to generate obfuscated PowerShell scripts that leverage polymorphism techniques for dynamic code mutation. These platforms integrate advanced algorithms to vary instruction sequences and encryption keys, enhancing stealth in cyber attack scenarios.
Future Trends in Polymorphic Code Obfuscation
Future trends in polymorphic code obfuscation emphasize advanced machine learning algorithms to dynamically generate ever-changing code patterns, making reverse engineering increasingly difficult. Techniques leveraging artificial intelligence enable automated mutation engines that adapt obfuscation strategies in real-time based on threat detection. Emerging quantum-resistant polymorphic obfuscation methods also promise enhanced security against next-generation decryption capabilities.
example of polymorphism in code obfuscation Infographic
 samplerz.com
samplerz.com