Aircrack-ng is a powerful tool used in wireless penetration testing to assess the security of Wi-Fi networks. It focuses on capturing packets and cracking WEP and WPA-PSK keys by analyzing captured data frames. The effectiveness of Aircrack-ng lies in its ability to exploit vulnerabilities in wireless encryption protocols, making it a crucial asset for network security audits. This tool supports various attack modes such as replay attacks, deauthentication, and fake authentication to gather sufficient data for key recovery. Its suite includes utilities like Airodump-ng for packet capturing and Aireplay-ng for traffic injection, streamlining the penetration testing process. Aircrack-ng's compatibility with multiple wireless adapters enhances its flexibility in different testing environments.
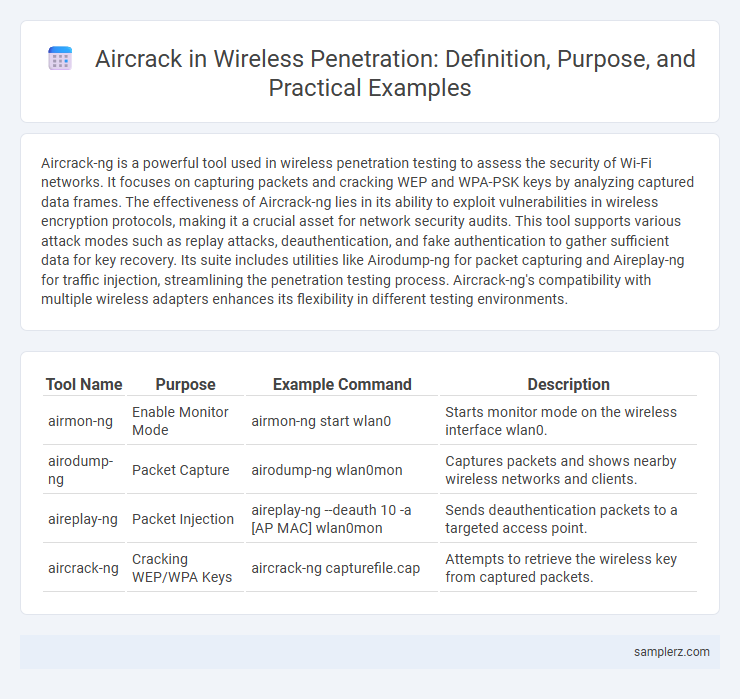
Table of Comparison
| Tool Name | Purpose | Example Command | Description |
|---|---|---|---|
| airmon-ng | Enable Monitor Mode | airmon-ng start wlan0 | Starts monitor mode on the wireless interface wlan0. |
| airodump-ng | Packet Capture | airodump-ng wlan0mon | Captures packets and shows nearby wireless networks and clients. |
| aireplay-ng | Packet Injection | aireplay-ng --deauth 10 -a [AP MAC] wlan0mon | Sends deauthentication packets to a targeted access point. |
| aircrack-ng | Cracking WEP/WPA Keys | aircrack-ng capturefile.cap | Attempts to retrieve the wireless key from captured packets. |
Introduction to Aircrack and Wireless Penetration Testing
Aircrack-ng is a powerful suite of tools used for assessing the security of wireless networks by capturing and analyzing packets to crack WEP and WPA-PSK keys. Wireless penetration testing utilizes Aircrack-ng to identify vulnerabilities in Wi-Fi encryption protocols, enabling security professionals to strengthen network defenses. This testing is essential for uncovering weaknesses in wireless infrastructures and ensuring robust protection against unauthorized access.
Understanding Wireless Security Protocols and Vulnerabilities
Aircrack-ng is a powerful tool used in wireless penetration testing to exploit vulnerabilities in WEP, WPA, and WPA2 security protocols by capturing and analyzing handshake packets. It effectively demonstrates weaknesses in encryption algorithms, enabling penetration testers to assess network security and identify susceptible access points. Understanding these protocols' flaws helps professionals strengthen wireless defenses against unauthorized access and cyber attacks.
Setting Up the Environment for Aircrack Testing
Setting up the environment for Aircrack testing involves configuring a compatible wireless adapter to operate in monitor mode, which allows packet capturing from nearby networks. Essential tools like Aircrack-ng suite and Wireshark must be installed on a Linux-based system for effective traffic analysis and decryption. Ensuring the wireless interface supports packet injection is critical for testing the security of WEP and WPA/WPA2 wireless networks accurately.
Capturing Wireless Packets with Aircrack Tools
Aircrack-ng captures wireless packets by placing the network interface into monitor mode, enabling the interception of raw 802.11 frames. This process allows the tool to gather initialization vectors (IVs) necessary for decrypting WEP and WPA-PSK keys. Utilizing specialized utilities like airmon-ng and airodump-ng, users can effectively monitor, capture, and analyze wireless traffic for penetration testing purposes.
Cracking WEP Encryption Using Aircrack-ng
Aircrack-ng is a powerful tool designed for cracking WEP encryption by analyzing captured wireless packets and performing statistical attacks on the encryption key. It utilizes techniques such as packet injection and initialization vector (IV) collection to accelerate the key recovery process, often requiring thousands of IVs to successfully crack WEP passwords. This tool is essential for wireless penetration testing, highlighting vulnerabilities in outdated WEP-secured networks and promoting improved security measures like WPA2.
Demonstrating WPA/WPA2 Handshake Capture
Aircrack-ng facilitates wireless penetration testing by capturing WPA/WPA2 handshakes, essential for assessing network security. The process involves placing the wireless interface into monitor mode, targeting the specific access point, and initiating deauthentication attacks to force clients to reconnect. Captured handshake files enable offline password cracking attempts, providing critical insights into the vulnerability of wireless encryption protocols.
Brute-Force and Dictionary Attacks on Wireless Networks
Aircrack-ng utilizes brute-force and dictionary attacks to compromise wireless network security by systematically attempting all possible keys or leveraging precompiled password lists to identify valid WPA/WPA2 passphrases. These methods exploit vulnerabilities in weak or common passwords, enabling unauthorized access to wireless networks by rapidly testing numerous combinations. Effective network security requires strong, complex passphrases and the implementation of advanced encryption protocols like WPA3 to counteract such automated intrusion techniques.
Interpreting Aircrack-ng Output and Results
Aircrack-ng analyzes captured wireless packets to crack WEP and WPA-PSK keys by running statistical attacks on the data. The tool outputs the key index, the recovered key, and the number of initialization vectors (IVs) used, highlighting the success of the decryption process. Interpreting Aircrack-ng results involves verifying key correctness against the handshake data and assessing signal quality indicators to ensure accurate penetration testing in wireless security auditing.
Common Challenges and Limitations in Wireless Penetration
Aircrack-ng, a popular wireless penetration testing tool, often faces challenges such as encrypted network protocols like WPA3, which significantly increase the difficulty of key cracking attempts. Limited range and the presence of multiple access points can cause packet loss and reduce the effectiveness of capturing handshake data. Hardware constraints, including low-quality network adapters and insufficient processing power, also hinder the speed and success of wireless penetration efforts.
Best Practices and Legal Considerations in Wireless Testing
Aircrack-ng is a powerful tool for evaluating wireless network security by capturing and analyzing packets to identify vulnerabilities in Wi-Fi encryption protocols such as WEP and WPA/WPA2. Best practices in wireless penetration testing with Aircrack-ng involve obtaining explicit written permission from network owners, using isolated test environments to prevent unintended disruptions, and adhering to industry guidelines like those from OWASP and the Wireless Security Alliance. Legal considerations require testers to comply with local laws and regulations, ensuring all activities are authorized to avoid violations of privacy and cybersecurity statutes.
example of aircrack in wireless penetration Infographic
 samplerz.com
samplerz.com