Secure Access Service Edge (SASE) integrates network security services with wide area network (WAN) capabilities to support dynamic, secure connections. A common example of SASE in network architecture involves combining firewall-as-a-service (FWaaS), secure web gateways (SWG), and zero trust network access (ZTNA) into a unified cloud platform. This architecture allows enterprises to enforce consistent security policies regardless of user location or device type. Cisco's SASE solution exemplifies this approach by delivering secure connectivity through its cloud-native security platform, integrating SD-WAN for optimized network performance. The architecture uses real-time data analytics to monitor threats and adapt policies based on user behavior and application context. Organizations benefit from reduced latency, simplified management, and enhanced protection against cyber threats with this comprehensive SASE implementation.
Table of Comparison
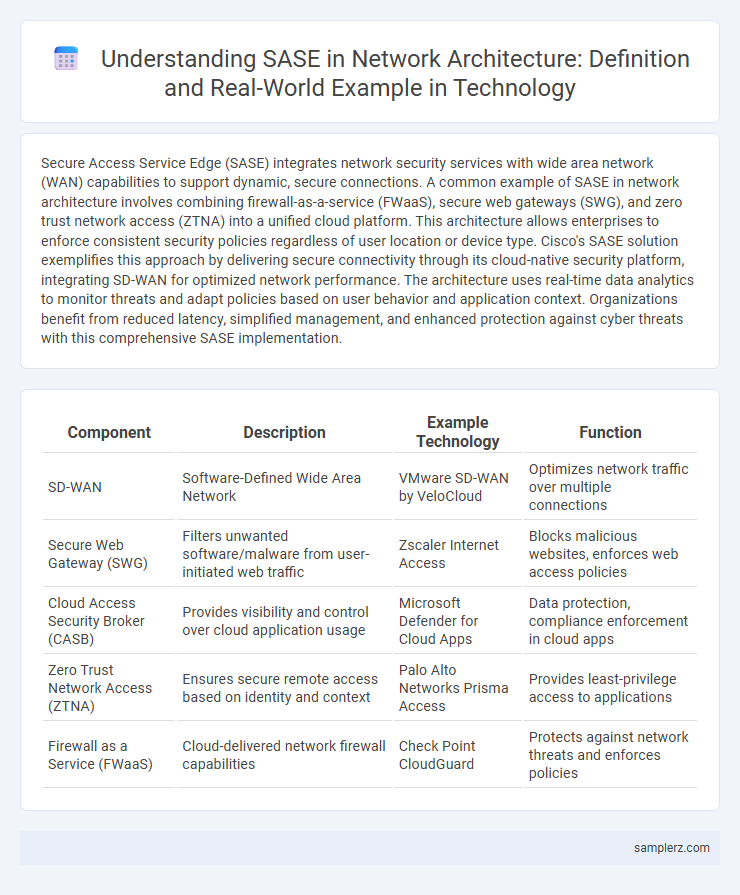
| Component | Description | Example Technology | Function |
|---|---|---|---|
| SD-WAN | Software-Defined Wide Area Network | VMware SD-WAN by VeloCloud | Optimizes network traffic over multiple connections |
| Secure Web Gateway (SWG) | Filters unwanted software/malware from user-initiated web traffic | Zscaler Internet Access | Blocks malicious websites, enforces web access policies |
| Cloud Access Security Broker (CASB) | Provides visibility and control over cloud application usage | Microsoft Defender for Cloud Apps | Data protection, compliance enforcement in cloud apps |
| Zero Trust Network Access (ZTNA) | Ensures secure remote access based on identity and context | Palo Alto Networks Prisma Access | Provides least-privilege access to applications |
| Firewall as a Service (FWaaS) | Cloud-delivered network firewall capabilities | Check Point CloudGuard | Protects against network threats and enforces policies |
Understanding SASE: Key Concepts and Components
Secure Access Service Edge (SASE) integrates network security functions such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Firewall as a Service (FWaaS), and Zero Trust Network Access (ZTNA) into a unified cloud-native service. This architecture simplifies the management of network security by delivering consistent policies and secure access regardless of user location or device. SASE enhances network performance and security through edge computing, providing real-time threat protection and seamless connectivity across distributed environments.
Real-World Use Cases of SASE in Network Environments
SASE (Secure Access Service Edge) is widely implemented in enterprises requiring secure, low-latency access for remote workers and branch offices, exemplified by multinational corporations integrating SASE to unify WAN and cybersecurity via cloud-native platforms. Financial institutions leverage SASE to enforce consistent security policies across distributed networks, enabling real-time threat prevention without compromising application performance. Telecommunications providers adopt SASE to streamline network management and optimize bandwidth usage while maintaining compliance with evolving regulatory standards.
SASE Implementation in Multi-Cloud Architectures
SASE implementation in multi-cloud architectures integrates secure access service edge capabilities to streamline network security across distributed cloud environments. By deploying SASE, organizations achieve unified policy enforcement, secure connectivity, and reduced latency between multiple cloud platforms such as AWS, Azure, and Google Cloud. This approach enhances threat protection, simplifies management, and optimizes performance in complex multi-cloud network infrastructures.
Enhancing Remote Workforce Security with SASE Solutions
SASE solutions integrate secure access service edge technology to protect remote workforces by combining SD-WAN capabilities with cloud-native security functions such as zero-trust network access (ZTNA), secure web gateways (SWG), and cloud access security brokers (CASB). Companies like Cisco and Palo Alto Networks deploy SASE frameworks that reduce threat exposure by enforcing consistent security policies across distributed endpoints and cloud environments. This architecture optimizes performance and security for remote users by dynamically routing traffic through encrypted tunnels while applying real-time threat intelligence.
SASE vs Traditional Network Security: Comparative Analysis
SASE (Secure Access Service Edge) integrates network security functions like SD-WAN, firewall as a service (FWaaS), and zero-trust network access (ZTNA) into a unified cloud-native platform, enhancing scalability and reducing latency compared to traditional network security architectures. Traditional security relies on on-premises hardware and perimeter-based defenses, leading to challenges in managing remote workforces and cloud applications effectively. Enterprises adopting SASE benefit from improved threat protection, simplified management, and optimized performance by converging connectivity and security in a single solution.
Integrating Zero Trust Principles within SASE Frameworks
SASE (Secure Access Service Edge) integrates Zero Trust principles by enforcing strict identity verification and least-privilege access across distributed networks. This approach combines network security functions such as SDP (Software-Defined Perimeter), CASB (Cloud Access Security Broker), and FWaaS (Firewall as a Service) within a unified platform to ensure continuous authentication and real-time threat intelligence. By leveraging granular access controls and dynamic policy enforcement, SASE frameworks effectively minimize attack surfaces and improve visibility in hybrid and cloud environments.
SASE Case Study: Global Enterprise Network Transformation
A global enterprise transformed its network architecture by implementing Secure Access Service Edge (SASE) to unify security and connectivity across 150 international branch offices. The deployment of cloud-delivered firewall, Zero Trust Network Access (ZTNA), and secure web gateways enhanced performance, reduced latency by 30%, and strengthened compliance with data protection regulations. This SASE case study demonstrates significant improvements in network agility, centralized policy management, and scalable security for the enterprise's hybrid cloud environment.
Streamlining Branch Connectivity Using SASE Architecture
SASE architecture streamlines branch connectivity by integrating SD-WAN capabilities with cloud-delivered security services such as CASB and FWaaS, reducing latency and improving network performance. Enterprises benefit from simplified management and enhanced security through centralized policy enforcement across distributed branches. This approach optimizes bandwidth usage while ensuring consistent access controls and threat protection for remote and branch offices.
SASE for Secure Access and Identity Management
Secure Access Service Edge (SASE) integrates identity management with network security by enforcing zero-trust policies through cloud-delivered security functions like Secure Web Gateways (SWG) and Cloud Access Security Brokers (CASB). SASE enables dynamic, context-aware access controls that verify user identity and device posture before granting network access, reducing attack surfaces. This architecture supports secure, seamless connectivity for remote and mobile users by converging identity-centric security with SD-WAN and threat prevention services.
Best Practices for Deploying SASE in Modern Networks
Implementing SASE (Secure Access Service Edge) in modern networks requires integrating edge security components like SD-WAN, CASB, and ZTNA to ensure seamless connectivity and robust protection. Best practices include continuous policy enforcement through cloud-native platforms, minimizing latency by distributing security functions at the network edge, and leveraging automation for dynamic threat response. Prioritizing user-centric access control combined with scalable cloud services enhances performance and security across distributed environments.
example of SASE in network architecture Infographic
 samplerz.com
samplerz.com