Onion routing is a technique used in technology to enhance online privacy by anonymizing data transmissions. It involves encrypting messages in multiple layers, resembling the layers of an onion, and routing them through a series of network nodes called relays or routers. Each relay decrypts only one layer, revealing the next destination, thereby preventing any single node from accessing the entire message or tracing the sender. The Tor network is a prominent example of onion routing in practice, widely used for anonymous communication and bypassing censorship. Data transmitted through Tor is encrypted and routed via multiple volunteer-operated relays across the globe, ensuring that the source and content remain concealed. This method significantly reduces tracking and surveillance risks for users seeking privacy in their online activities.
Table of Comparison
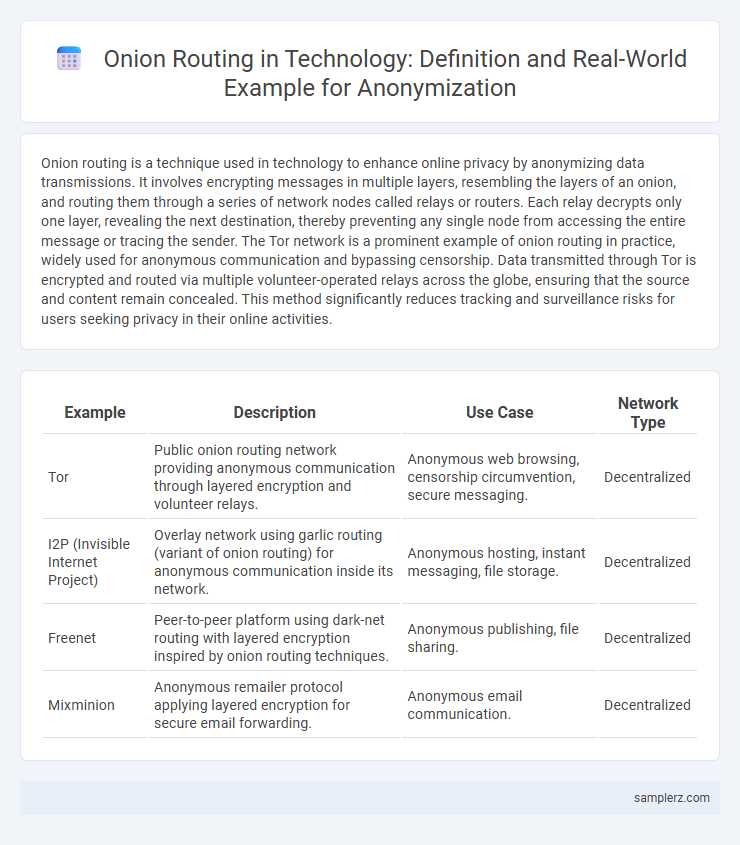
| Example | Description | Use Case | Network Type |
|---|---|---|---|
| Tor | Public onion routing network providing anonymous communication through layered encryption and volunteer relays. | Anonymous web browsing, censorship circumvention, secure messaging. | Decentralized |
| I2P (Invisible Internet Project) | Overlay network using garlic routing (variant of onion routing) for anonymous communication inside its network. | Anonymous hosting, instant messaging, file storage. | Decentralized |
| Freenet | Peer-to-peer platform using dark-net routing with layered encryption inspired by onion routing techniques. | Anonymous publishing, file sharing. | Decentralized |
| Mixminion | Anonymous remailer protocol applying layered encryption for secure email forwarding. | Anonymous email communication. | Decentralized |
Understanding Onion Routing in Anonymization
Onion routing anonymizes internet traffic by encrypting data in multiple layers, each decrypted by successive nodes, shielding the user's identity. This method ensures that no single point can trace the origin or destination of the communication, enhancing privacy. Applications like Tor exemplify onion routing by enabling anonymous browsing and circumventing censorship.
How Onion Routing Works: A Technical Overview
Onion routing anonymizes data by encapsulating messages in multiple layers of encryption, each peeled away by successive nodes in a network called relays or onion routers. When a user sends data, it is wrapped in encrypted layers corresponding to each node, ensuring that no single relay knows both the origin and destination of the message. This layered encryption method effectively conceals user identities and communication paths, providing strong privacy and resistance to traffic analysis in technologies like Tor.
Real-World Example: The Tor Network
The Tor network exemplifies onion routing by encrypting user data in multiple layers and routing it through a series of volunteer-operated nodes, making it difficult to trace the original source. This decentralized structure enhances online privacy and protects against traffic analysis and network surveillance. Tor's widespread adoption in privacy-focused applications highlights its effectiveness in maintaining user anonymity on the internet.
Onion Routing vs. Traditional Proxies
Onion Routing encrypts data multiple times and routes it through a series of volunteer-operated nodes, ensuring each node only knows the previous and next hop, which significantly enhances user anonymity compared to traditional proxies. Traditional proxies typically reroute traffic through a single server, exposing user data to that server and making them more vulnerable to surveillance and logging. The layered encryption and decentralized structure of Onion Routing provide stronger resistance to traffic analysis and tracking.
Case Study: Secure Messaging with Onion Routing
Onion routing enhances secure messaging by encrypting data in multiple layers, ensuring each relay node only decrypts its respective layer to prevent exposure of the sender or recipient. The Signal Protocol exemplifies this approach with its use of onion-encrypted message packets, providing end-to-end anonymity and resistance to traffic analysis. Case studies demonstrate that onion routing significantly mitigates metadata leakage in real-time communication platforms like Signal and Ricochet IM, maintaining user privacy in hostile network environments.
Layered Encryption: The Core of Onion Routing
Layered encryption in onion routing ensures that each message is wrapped in multiple layers of cryptographic protection, corresponding to each node in the network path. Every relay node decrypts its specific layer, revealing only the next destination, which maintains sender anonymity and message confidentiality. This process prevents any single point from accessing both sender identity and message content, enhancing secure and private communication online.
Impact of Onion Routing on Internet Privacy
Onion routing significantly enhances internet privacy by encrypting data in layered protocols that obscure users' IP addresses and browsing activities from surveillance and tracking. The Tor network, a prime example of onion routing, enables anonymous communication by routing traffic through multiple global relays, preventing data correlation and protecting user identity. This technology mitigates risks of censorship, data profiling, and unauthorized data collection, making it a critical tool for privacy advocates and journalists operating under oppressive regimes.
Limitations and Vulnerabilities of Onion Routing
Onion routing, widely used in anonymization protocols like Tor, faces limitations such as latency issues and susceptibility to traffic correlation attacks that can deanonymize users by analyzing timing patterns. Exit nodes in onion routing networks pose vulnerabilities since they decrypt the final layer, potentially exposing unencrypted traffic to malicious operators. Moreover, sophisticated adversaries with global network monitoring capabilities can exploit routing characteristics to compromise anonymity and trace communication paths despite encryption layers.
Innovations Inspired by Onion Routing
Innovations inspired by onion routing have led to advanced anonymization techniques such as mix networks and decentralized VPNs, enhancing privacy by layering encryption to obscure user data paths. These technologies leverage multi-layered encryption and routing protocols to prevent traffic analysis and safeguard user identities across networks. The evolution of onion routing principles continues to influence secure communication systems, fostering developments in blockchain privacy solutions and secure messaging applications.
Future Trends in Onion Routing and Anonymization
Future trends in onion routing emphasize integration with quantum-resistant cryptography to enhance security against emerging quantum computing threats. Advancements in decentralized network architectures aim to improve scalability and reduce latency in anonymization services. Research into AI-driven adaptive routing algorithms promises more efficient and dynamic anonymity protections for users.
example of onionrouting in anonymization Infographic
 samplerz.com
samplerz.com