Skimming in payment systems is a form of fraud where criminals illegally capture card information using a small device called a skimmer. This device is often installed on ATMs, gas station pumps, or point-of-sale terminals, secretly recording data from the magnetic stripe of credit or debit cards. The stolen data can then be cloned onto counterfeit cards or used for unauthorized online transactions. Financial institutions and businesses implement various anti-skimming technologies such as encrypted card readers, jamming devices, and real-time transaction monitoring to protect customers. Consumer awareness plays a critical role, encouraging individuals to inspect payment terminals for suspicious attachments or unusual behavior. Advances in chip-based card technology also reduce the risk of skimming by creating dynamic transaction codes that are difficult to duplicate.
Table of Comparison
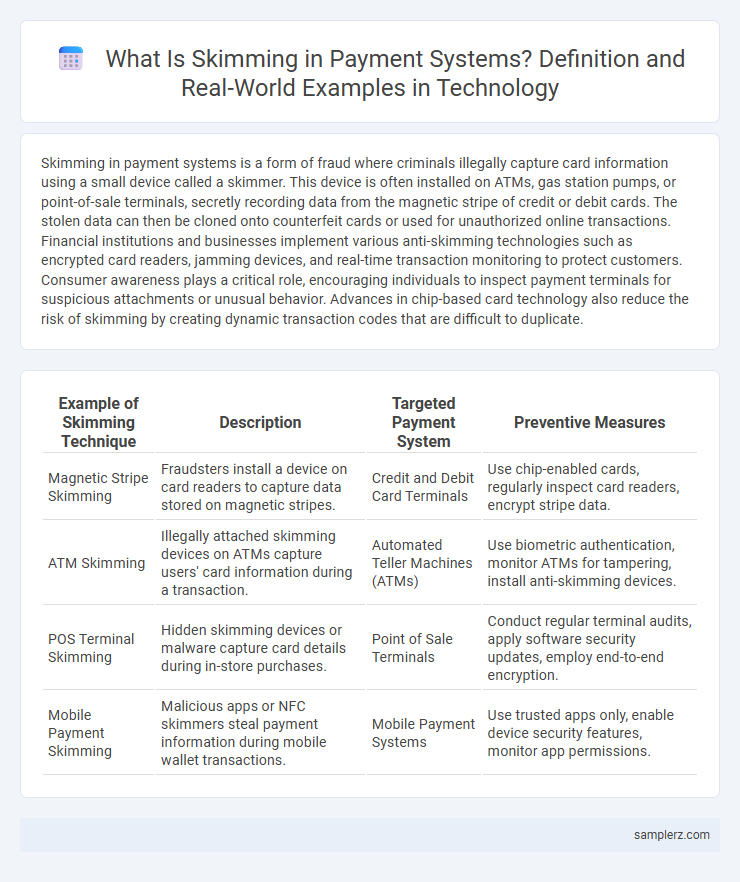
| Example of Skimming Technique | Description | Targeted Payment System | Preventive Measures |
|---|---|---|---|
| Magnetic Stripe Skimming | Fraudsters install a device on card readers to capture data stored on magnetic stripes. | Credit and Debit Card Terminals | Use chip-enabled cards, regularly inspect card readers, encrypt stripe data. |
| ATM Skimming | Illegally attached skimming devices on ATMs capture users' card information during a transaction. | Automated Teller Machines (ATMs) | Use biometric authentication, monitor ATMs for tampering, install anti-skimming devices. |
| POS Terminal Skimming | Hidden skimming devices or malware capture card details during in-store purchases. | Point of Sale Terminals | Conduct regular terminal audits, apply software security updates, employ end-to-end encryption. |
| Mobile Payment Skimming | Malicious apps or NFC skimmers steal payment information during mobile wallet transactions. | Mobile Payment Systems | Use trusted apps only, enable device security features, monitor app permissions. |
What is Skimming in Payment Systems?
Skimming in payment systems refers to the illegal practice of capturing and copying credit or debit card information using a small electronic device called a skimmer, often placed on ATMs or point-of-sale terminals. This stolen data is then used to create counterfeit cards or execute unauthorized transactions, leading to significant financial losses and compromised consumer security. Advanced skimming techniques now also include wireless data transmission, making detection by victims and institutions more challenging and emphasizing the need for enhanced payment security measures.
Common Methods Used for Payment Skimming
Common methods used for payment skimming include the installation of small, concealed devices on ATMs, gas station pumps, and point-of-sale terminals to capture card data during transactions. Criminals often use handheld skimmers and shimmers, the latter targeting chip card technology by inserting thin devices into card readers. Magnetic stripe data and PIN numbers collected through these methods enable unauthorized transactions and financial fraud.
Real-World Cases of Skimming in Payment Systems
Real-world cases of skimming in payment systems often involve criminals installing hidden card readers on ATMs and point-of-sale terminals to capture magnetic stripe data. Notable incidents include the 2013 Target breach, where millions of payment card details were skimmed via compromised payment terminals, leading to widespread fraud. Financial institutions continuously upgrade security measures like EMV chip technology and encryption to combat these sophisticated skimming attacks.
Skimming at ATMs: How It Happens
Skimming at ATMs occurs when criminals attach a small device over the card slot to capture card data during legitimate transactions. These devices often include a hidden camera or keypad overlay to record PIN entries, enabling unauthorized access to accounts. Such fraudulent technology exploits vulnerabilities in ATM hardware, emphasizing the need for enhanced security measures like EMV chip authentication and surveillance integration.
POS Terminal Skimming: Techniques and Risks
POS terminal skimming involves installing discreet devices on payment terminals to illegally capture card data during transactions. Cybercriminals often use tiny card readers and pinhole cameras to record magnetic stripe information and PIN entries, posing significant risks to cardholders and merchants. Understanding these techniques helps businesses implement advanced security measures like EMV chips and anti-skimming technology to prevent data theft.
Credit Card Skimming: Examples and Warnings
Credit card skimming involves fraudsters installing small devices on legitimate card readers, such as ATMs or gas station pumps, to illegally capture card data during transactions. Examples include hidden skimmers on point-of-sale terminals that record magnetic stripe information covertly. Customers should regularly monitor bank statements and use chip-enabled cards to reduce the risk of unauthorized credit card data theft.
Contactless Payment Skimming Scenarios
Contactless payment skimming occurs when criminals use RFID readers to steal card information during tap transactions without physical contact. Attackers can intercept data from unsuspecting users in crowded places by hovering devices near wallets or smartphones. This form of skimming exploits the wireless communication in NFC-enabled credit cards and mobile payment apps, posing significant security risks to users.
Skimming Devices: Types and Identification
Skimming devices in payment systems include overlay skimmers, which are placed over card readers to capture magnetic stripe data, and shimming devices that infiltrate EMV chip readers to extract chip information. Identification of these devices involves inspecting card readers for loose or bulky components, unusual wires, or mismatched LED lights, alongside using specialized tools like anti-skimming detectors. Security protocols and regular hardware audits are critical for detecting and preventing skimming attacks.
Impact of Skimming on Consumers and Businesses
Skimming in payment systems involves illegally capturing card data through compromised point-of-sale terminals or ATM devices, leading to significant financial losses for consumers and businesses. Consumers face unauthorized transactions, depleted accounts, and potential credit score damage, while businesses experience chargeback fees, reputational harm, and increased costs for implementing enhanced security measures. The widespread impact of skimming accelerates the adoption of EMV chip technology and tokenization to protect sensitive payment information.
Preventive Measures Against Skimming in Payment Systems
Preventive measures against skimming in payment systems include deploying EMV chip technology, which encrypts transaction data to prevent unauthorized copying of card information. Installing anti-skimming devices on ATMs and point-of-sale terminals helps detect and block fraudulent card readers. Educating users to regularly monitor account statements and use contactless payment methods further reduces the risk of skimming attacks.
example of skimming in payment system Infographic
 samplerz.com
samplerz.com