A sandbox in malware analysis is a secure, isolated environment designed to execute and observe potentially malicious software without risking damage to the host system. Cybersecurity professionals use sandboxes to monitor the behavior of malware, capturing data such as file modifications, network activity, and system calls. This data helps in identifying the threat's objectives, techniques, and potential vulnerabilities. Sandbox technology often employs virtualization or containerization to replicate various operating systems and environments, enabling comprehensive testing of different malware strains. Tools like Cuckoo Sandbox and FireEye provide automated analysis, generating detailed reports on the malware's actions and indicators of compromise (IOCs). These entities offer critical insights that assist in developing detection signatures and enhancing overall security posture.
Table of Comparison
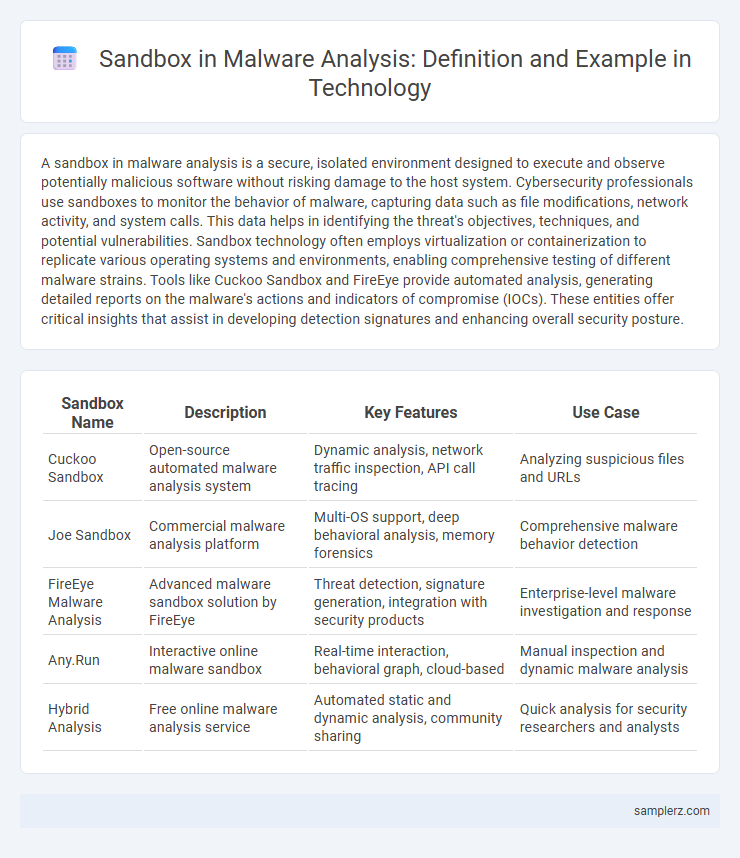
| Sandbox Name | Description | Key Features | Use Case |
|---|---|---|---|
| Cuckoo Sandbox | Open-source automated malware analysis system | Dynamic analysis, network traffic inspection, API call tracing | Analyzing suspicious files and URLs |
| Joe Sandbox | Commercial malware analysis platform | Multi-OS support, deep behavioral analysis, memory forensics | Comprehensive malware behavior detection |
| FireEye Malware Analysis | Advanced malware sandbox solution by FireEye | Threat detection, signature generation, integration with security products | Enterprise-level malware investigation and response |
| Any.Run | Interactive online malware sandbox | Real-time interaction, behavioral graph, cloud-based | Manual inspection and dynamic malware analysis |
| Hybrid Analysis | Free online malware analysis service | Automated static and dynamic analysis, community sharing | Quick analysis for security researchers and analysts |
Introduction to Sandboxes in Malware Analysis
A sandbox in malware analysis is a controlled, isolated environment designed to safely execute and observe suspicious software without risking damage to the host system. These virtual environments capture detailed behavioral data, such as file modifications, network activity, and system calls, helping analysts identify malicious intent. Popular sandbox solutions include Cuckoo Sandbox, FireEye, and Any.Run, which automate malware detection and facilitate rapid threat assessment.
Key Features of Malware Analysis Sandboxes
Malware analysis sandboxes isolate suspicious files in a controlled environment to monitor behaviors such as file modifications, network traffic, and system calls without risking host contamination. These sandboxes provide automated static and dynamic analysis, capturing detailed reports on malware payload execution and obfuscation techniques. Integration with threat intelligence databases and real-time alerting enhances the detection of zero-day exploits and polymorphic malware variants.
Popular Sandbox Tools for Malware Research
Popular sandbox tools for malware research include Cuckoo Sandbox, an open-source automated malware analysis system that provides detailed reports on malicious behavior. Sandboxie offers isolated environments for running suspicious applications safely, preventing malware from affecting the host system. Other widely-used tools such as Joe Sandbox and Any.Run provide advanced dynamic analysis and real-time interaction capabilities for in-depth malware examination.
Automated vs. Manual Sandboxing Techniques
Automated sandboxing techniques in malware analysis enable rapid execution and behavior monitoring of suspicious files within isolated virtual environments, providing scalable detection of threats without human intervention. Manual sandboxing involves security analysts interactively investigating malware samples by controlling execution steps to observe intricate behaviors and extract detailed intelligence often missed by automation. Combining both approaches enhances malware detection accuracy, leveraging automation for efficiency and manual analysis for in-depth contextual understanding of complex cyber threats.
Real-World Sandbox Deployment Scenarios
Real-world sandbox deployment scenarios in malware analysis include corporate cybersecurity environments where isolated virtual machines execute suspicious files to detect threats without risking network integrity. Cloud-based sandboxes such as those offered by services like FireEye or Palo Alto Networks provide scalable, real-time threat intelligence by analyzing malware behavior in controlled, ephemeral environments. These deployments enable rapid identification of zero-day exploits and advanced persistent threats by capturing detailed runtime data and network activity.
Step-by-Step Malware Analysis Using a Sandbox
Step-by-step malware analysis using a sandbox involves isolating suspicious files in a controlled virtual environment to observe their behavior without risking system compromise. Key steps include executing the malware sample within the sandbox, monitoring network traffic and system changes, and capturing detailed logs to identify malicious activities. Tools like Cuckoo Sandbox enable automated analysis by providing comprehensive reports on file execution, registry modifications, and network communications for precise threat assessment.
Benefits of Sandbox Environments for Cybersecurity
Sandbox environments in malware analysis isolate suspicious files in a controlled setting to observe malicious behavior without risking system integrity. These environments provide detailed insights into malware functions, enabling faster threat detection and response. Enhanced security through sandboxing reduces false positives and strengthens overall cybersecurity posture.
Case Studies: Sandbox Applications in Threat Detection
Sandbox environments like Cuckoo Sandbox enable deep inspection of malware behavior by isolating suspicious files in virtual machines, providing analysts with detailed execution logs and network activity. Case studies demonstrate its effectiveness in detecting zero-day exploits by capturing real-time system modifications and command-and-control communications. Deployments in enterprise settings reveal significant reductions in false positives and enhanced threat intelligence integration for proactive defense.
Limitations and Challenges of Sandbox Analysis
Sandbox analysis in malware detection faces limitations such as evasion techniques where sophisticated malware can detect virtual environments and alter behavior to avoid detection. Performance overhead is another challenge, as executing malware in a sandbox requires substantial computational resources and time, hindering real-time analysis. Furthermore, maintaining up-to-date sandbox environments is crucial, as outdated signatures and configurations can result in false negatives and reduce overall detection accuracy.
Future Trends in Sandbox Technology for Malware Analysis
Emerging sandbox technologies in malware analysis increasingly incorporate machine learning algorithms to enhance behavior detection and reduce false positives. Cloud-based sandbox environments enable scalable, real-time analysis of sophisticated threats and support collaborative threat intelligence sharing. Advances in virtualization and containerization improve sandbox fidelity, allowing more accurate emulation of diverse operating systems and hardware configurations.
example of sandbox in malware analysis Infographic
 samplerz.com
samplerz.com