A hash in blockchain is a unique digital fingerprint generated by a cryptographic algorithm that transforms input data into a fixed-size string of characters. Each block in a blockchain contains a hash of the previous block, creating a secure and immutable chain of data records. The SHA-256 algorithm is commonly used in blockchain technology to produce these hashes, ensuring data integrity and protection against tampering. Data within a blockchain is organized into blocks, each containing transactional details hashed into a concise format that links blocks in chronological order. The process of hashing helps verify transactions without revealing the actual data, enhancing privacy and security in decentralized systems. Hashes are fundamental to consensus mechanisms, such as Proof of Work, where miners compete to find a hash that meets specific criteria, validating new blocks and maintaining the blockchain network.
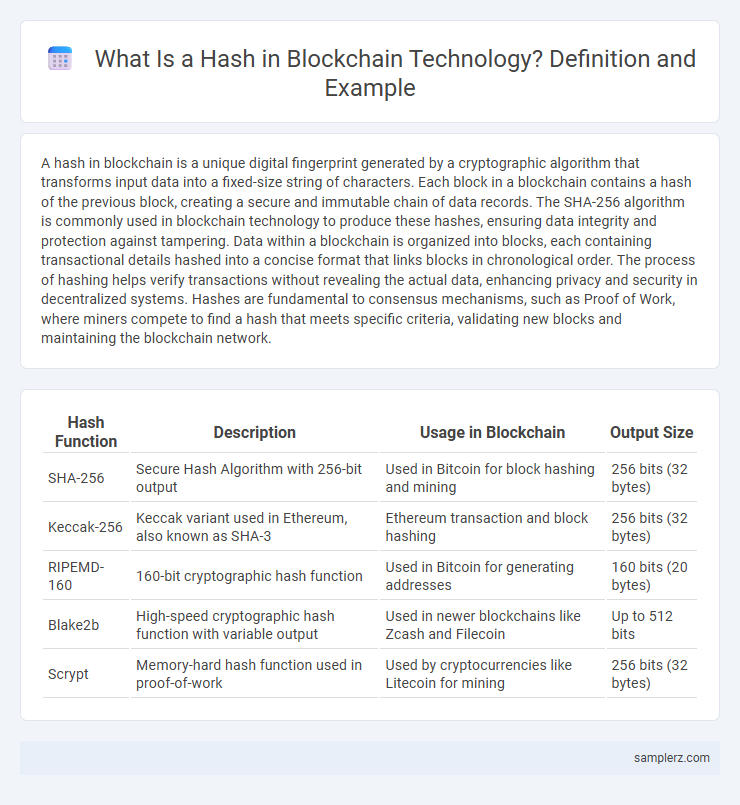
Table of Comparison
| Hash Function | Description | Usage in Blockchain | Output Size |
|---|---|---|---|
| SHA-256 | Secure Hash Algorithm with 256-bit output | Used in Bitcoin for block hashing and mining | 256 bits (32 bytes) |
| Keccak-256 | Keccak variant used in Ethereum, also known as SHA-3 | Ethereum transaction and block hashing | 256 bits (32 bytes) |
| RIPEMD-160 | 160-bit cryptographic hash function | Used in Bitcoin for generating addresses | 160 bits (20 bytes) |
| Blake2b | High-speed cryptographic hash function with variable output | Used in newer blockchains like Zcash and Filecoin | Up to 512 bits |
| Scrypt | Memory-hard hash function used in proof-of-work | Used by cryptocurrencies like Litecoin for mining | 256 bits (32 bytes) |
Understanding Hash Functions in Blockchain Technology
Hash functions in blockchain technology create a fixed-size string of characters from input data, ensuring data integrity and security. Each block contains a hash of the previous block, linking blocks in a secure chain that prevents tampering. This cryptographic process underpins consensus algorithms and enables trustless transactions in decentralized networks.
Role of Hashes in Ensuring Blockchain Security
Hashes in blockchain act as unique digital fingerprints for each block, ensuring data integrity by making any alteration easily detectable. They link blocks together through cryptographic algorithms like SHA-256, creating an immutable chain that prevents tampering. This cryptographic security underpins consensus mechanisms, safeguarding transaction authenticity and network trustworthiness.
Real-World Example: SHA-256 Hashing in Bitcoin
SHA-256 hashing algorithm serves as the fundamental cryptographic function in Bitcoin, transforming transaction data into a fixed 256-bit hash value that ensures data integrity and security. This hash not only links each block to its predecessor, creating an immutable blockchain, but also underpins Bitcoin's proof-of-work consensus mechanism by requiring miners to find a hash below a specific target. The robustness and collision resistance of SHA-256 solidify it as a critical component enabling trust and decentralization in Bitcoin's digital ledger.
Step-by-Step: How a Transaction Hash is Created
A transaction hash in blockchain is created by first compiling the transaction data, including sender, receiver, amount, and timestamp, into a structured format. This data is then input into a cryptographic hash function like SHA-256, which processes the information and produces a fixed-length, unique alphanumeric string. The resulting transaction hash serves as a digital fingerprint, ensuring data integrity and enabling easy verification within the blockchain network.
Hashes and Digital Signatures in Blockchain Validation
Hashes like SHA-256 serve as the backbone of blockchain validation by securely converting transaction data into fixed-length strings, ensuring data integrity and preventing tampering. Digital signatures use asymmetric cryptography to authenticate the transaction sender, linking the public key to the hashed transaction for verification. Together, hashes and digital signatures maintain the trustworthiness and immutability of blockchain records through cryptographic validation mechanisms.
Blockchain Integrity: Merkle Trees and Hashing
Merkle trees utilize cryptographic hashing to link transaction hashes into a single root hash, preserving blockchain integrity by enabling efficient and tamper-proof verification of data. Each leaf node represents a transaction hash, while parent nodes combine child hashes, creating a secure hierarchical structure resistant to data alteration. This method ensures that any change in transaction data results in a different root hash, making unauthorized modifications easily detectable in blockchain networks.
Example of Using Hashes for Data Immutability
In blockchain technology, SHA-256 hash functions are commonly used to ensure data immutability by generating unique fixed-length outputs for transaction data, making any alteration easily detectable. For example, if even a single bit in a block's content changes, the resulting hash will differ dramatically, signaling tampering. This cryptographic hashing mechanism secures the integrity of blocks, maintaining a transparent and tamper-proof ledger.
Hash Functions in Smart Contract Execution
Hash functions like SHA-256 play a critical role in smart contract execution by ensuring data integrity and enabling secure transaction verification on the blockchain. These cryptographic algorithms convert input data into fixed-size hash values, facilitating deterministic state changes and preventing tampering during contract processing. Efficient hashing mechanisms allow smart contracts to authenticate sender identities, validate inputs, and maintain trustless, decentralized operations within blockchain platforms such as Ethereum.
Practical Demonstration: Hashing a Block Header
Hashing a block header in blockchain involves taking the block's metadata--including the previous block hash, timestamp, nonce, and Merkle root--and applying a cryptographic hash function like SHA-256 to produce a unique fixed-length output. This hash acts as a digital fingerprint, ensuring the integrity and immutability of the block by linking it securely to the previous one. Miners iteratively modify the nonce value to find a hash that meets the network's difficulty target, demonstrating proof of work through this computational process.
Cryptographic Hashing Algorithms in Leading Blockchains
SHA-256 is the cryptographic hashing algorithm most famously utilized by Bitcoin, ensuring data integrity and security through its deterministic and collision-resistant properties. Ethereum employs the Keccak-256 hash function, a variant of SHA-3, to secure transaction data and smart contract operations. Leading blockchains rely on these robust hashing algorithms to maintain consensus, validate transactions, and protect against tampering in decentralized networks.
example of hash in blockchain Infographic
 samplerz.com
samplerz.com