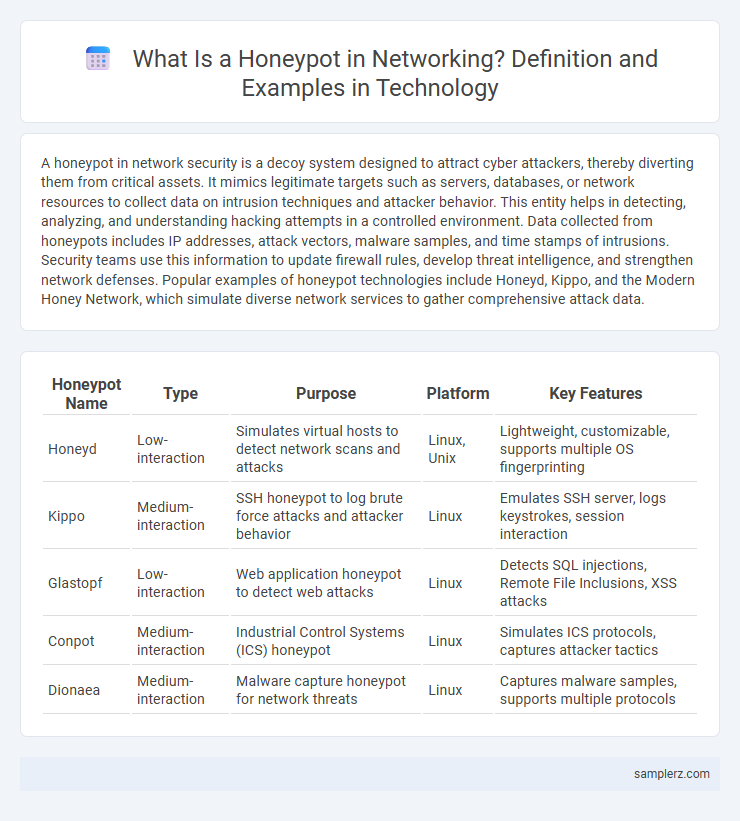
A honeypot in network security is a decoy system designed to attract cyber attackers, thereby diverting them from critical assets. It mimics legitimate targets such as servers, databases, or network resources to collect data on intrusion techniques and attacker behavior. This entity helps in detecting, analyzing, and understanding hacking attempts in a controlled environment. Data collected from honeypots includes IP addresses, attack vectors, malware samples, and time stamps of intrusions. Security teams use this information to update firewall rules, develop threat intelligence, and strengthen network defenses. Popular examples of honeypot technologies include Honeyd, Kippo, and the Modern Honey Network, which simulate diverse network services to gather comprehensive attack data.
Table of Comparison
| Honeypot Name | Type | Purpose | Platform | Key Features |
|---|---|---|---|---|
| Honeyd | Low-interaction | Simulates virtual hosts to detect network scans and attacks | Linux, Unix | Lightweight, customizable, supports multiple OS fingerprinting |
| Kippo | Medium-interaction | SSH honeypot to log brute force attacks and attacker behavior | Linux | Emulates SSH server, logs keystrokes, session interaction |
| Glastopf | Low-interaction | Web application honeypot to detect web attacks | Linux | Detects SQL injections, Remote File Inclusions, XSS attacks |
| Conpot | Medium-interaction | Industrial Control Systems (ICS) honeypot | Linux | Simulates ICS protocols, captures attacker tactics |
| Dionaea | Medium-interaction | Malware capture honeypot for network threats | Linux | Captures malware samples, supports multiple protocols |
Introduction to Honeypots in Network Security
Honeypots in network security serve as decoy systems designed to attract cyber attackers, enabling the collection of intelligence on attack methods and tactics. These isolated and monitored environments mimic real network resources, luring hackers away from critical infrastructure while providing valuable data for threat analysis. Deployment of honeypots enhances an organization's ability to detect, analyze, and respond to emerging cyber threats effectively.
Basic Example: Simulated Web Server Honeypot
A simulated web server honeypot mimics a real website environment to attract and analyze malicious traffic targeting web vulnerabilities. It collects data on attack methods such as SQL injection, cross-site scripting (XSS), and brute force login attempts, enabling security teams to study attacker behavior without risking production systems. This basic honeypot setup enhances threat intelligence by providing real-time insights into exploitation techniques and emerging web-based threats.
Database Honeypots: Luring SQL Attackers
Database honeypots simulate vulnerable SQL environments to attract and analyze attackers attempting SQL injection or other database exploits. By mimicking real database structures and behaviors, these honeypots capture attack vectors and techniques, providing valuable intelligence for enhancing security measures. Deploying database honeypots helps organizations identify emerging threats and reinforce defenses against malicious SQL activities.
SSH Honeypots for Credential Harvesting
SSH honeypots are specialized decoy systems designed to attract and capture unauthorized login attempts by mimicking vulnerable SSH servers, enabling cybersecurity experts to analyze credential harvesting techniques. These honeypots log attacker IP addresses, passwords, and behavior patterns, providing valuable intelligence to identify common brute-force strategies and compromised credentials used in cyberattacks. Deploying SSH honeypots enhances network defense by facilitating early detection of credential theft and improving threat response capabilities through real-world attack data collection.
Email Server Honeypot: Identifying Phishing Attempts
Email server honeypots simulate real mail systems to attract and analyze phishing attempts, capturing malicious payloads and sender information. By monitoring incoming emails, these honeypots detect phishing strategies involving spoofed addresses, malicious links, and zero-day exploits. Data collected enhances threat intelligence, improving spam filters and anti-phishing measures within network security frameworks.
IoT Device Honeypot in Modern Networks
IoT device honeypots simulate vulnerable smart devices like cameras, thermostats, and sensors to attract and analyze cyberattacks targeting the Internet of Things. These honeypots help identify emerging threats such as Mirai botnet infections and unauthorized access attempts in real time. By deploying IoT honeypots, network defenders gain actionable intelligence to enhance security policies and fortify IoT ecosystems against evolving attack vectors.
High-Interaction Honeypots for Advanced Threat Detection
High-interaction honeypots, such as the Honeynet Project's Sebek system, simulate entire operating systems to capture detailed attacker behaviors and advanced threat techniques. These honeypots provide deep insight into zero-day exploits, malware propagation, and lateral movement tactics by engaging adversaries in realistic environments. Organizations deploy high-interaction honeypots to enhance threat intelligence, improve intrusion detection systems, and strengthen overall cybersecurity defenses.
Low-Interaction Honeypots for Minimal Risk
Low-interaction honeypots simulate only a limited set of services and operating system behaviors to attract cyber attackers while minimizing security risks. Examples include Honeyd, which creates virtual hosts on a network to detect unauthorized access attempts without exposing real system vulnerabilities. This approach allows network administrators to gather data on attack methods and sources without risking critical infrastructure.
Industrial Control System (ICS) Honeypot Analysis
Industrial Control System (ICS) honeypots simulate critical infrastructure environments such as SCADA networks to detect and analyze cyber threats targeting operational technology. These honeypots capture attack patterns, including malware behavior and intrusion techniques specific to ICS protocols like Modbus and DNP3. By emulating real ICS components, they provide valuable data for enhancing threat intelligence and improving cybersecurity strategies in industrial sectors.
Real-World Case Studies: Successful Honeypot Deployments
The Honeynet Project exemplifies successful honeypot deployment by creating a global network of honeypots that capture real-time cyberattack data, enabling comprehensive threat analysis and improved defensive strategies. Another notable case is Google's use of high-interaction honeypots to detect and analyze sophisticated state-sponsored attacks, enhancing their cybersecurity posture. These real-world implementations demonstrate how honeypots effectively detect, analyze, and mitigate advanced persistent threats (APTs) in modern network environments.
example of honeypot in network Infographic
 samplerz.com
samplerz.com