An air gap in security refers to a network security measure that physically isolates a computer or network from unsecured networks, such as the internet or external networks. This separation ensures that sensitive systems, like those used in military, financial, or critical infrastructure environments, remain protected from cyber threats and unauthorized access. For example, a classified government computer handling top-secret data may be air-gapped to prevent any potential hacking attempts. Air-gapped systems rely on data transfer methods like USB drives or dedicated data diodes to move information securely between isolated and connected environments. These setups limit exposure to malware or ransomware attacks commonly targeting connected devices. In industrial control systems, an air gap protects operational technology by separating it from corporate networks, minimizing risks of cyber-physical attacks that could disrupt essential services.
Table of Comparison
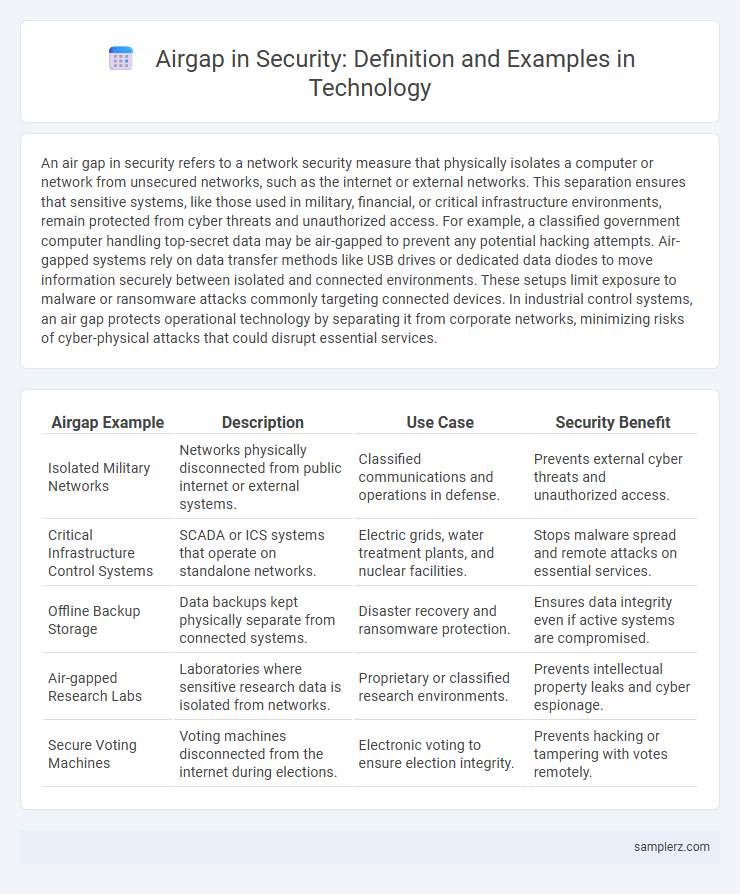
| Airgap Example | Description | Use Case | Security Benefit |
|---|---|---|---|
| Isolated Military Networks | Networks physically disconnected from public internet or external systems. | Classified communications and operations in defense. | Prevents external cyber threats and unauthorized access. |
| Critical Infrastructure Control Systems | SCADA or ICS systems that operate on standalone networks. | Electric grids, water treatment plants, and nuclear facilities. | Stops malware spread and remote attacks on essential services. |
| Offline Backup Storage | Data backups kept physically separate from connected systems. | Disaster recovery and ransomware protection. | Ensures data integrity even if active systems are compromised. |
| Air-gapped Research Labs | Laboratories where sensitive research data is isolated from networks. | Proprietary or classified research environments. | Prevents intellectual property leaks and cyber espionage. |
| Secure Voting Machines | Voting machines disconnected from the internet during elections. | Electronic voting to ensure election integrity. | Prevents hacking or tampering with votes remotely. |
Understanding Airgap: Definition and Core Concept
An air gap in security refers to a physical and electronic isolation between a secure computer or network and unsecured networks, ensuring no direct or indirect data communication occurs. This method is widely used in high-security environments such as military systems, critical infrastructure control systems, and sensitive data storage to prevent cyberattacks and unauthorized access. By maintaining a gap, data transfer relies solely on manual methods like removable media, substantially reducing the risk of malware infiltration and data breaches.
Common Scenarios Where Airgap is Applied
Airgap security is commonly applied in critical infrastructure such as power plants and military defense systems to isolate sensitive networks from external threats. Financial institutions also implement airgapped environments to protect transaction data and prevent cyber attacks targeting customer information. In industrial control systems, airgaps secure operational technology by physically separating control networks from the internet and corporate LANs.
Real-World Examples of Airgap in Critical Infrastructure
Airgaps in critical infrastructure protect national security by isolating control systems from external networks, as seen in the Stuxnet attack on Iran's nuclear facilities where airgapped centrifuge systems were targeted. Power grids often employ airgapped networks to separate supervisory control and data acquisition (SCADA) systems from the internet, preventing cyber intrusions that could cause blackouts. In military environments, classified communication networks remain airgapped to ensure sensitive operational data is shielded from cyber espionage attempts.
Airgap in Financial Institutions: A Security Perspective
Airgap security in financial institutions involves isolating critical systems from unsecured networks to prevent cyberattacks, ensuring sensitive data and transactions remain protected from remote threats. This physical and logical separation dramatically reduces the risk of malware infiltration, unauthorized access, and data breaches in banking networks. Financial organizations often deploy airgapped systems for core banking operations, transaction processing, and data storage to maintain regulatory compliance and safeguard customer assets.
Military Airgap Solutions for Data Protection
Military airgap solutions isolate critical systems by physically disconnecting them from unsecured networks, preventing unauthorized access and cyber intrusions. These solutions use separate hardware, such as standalone servers and dedicated communication devices, ensuring sensitive data remains within a secure, controlled environment. Implementing advanced enclave architectures and controlled data transfer protocols enhances data protection against cyber espionage in defense operations.
Airgap Deployment in Industrial Control Systems (ICS)
Airgap deployment in Industrial Control Systems (ICS) isolates critical infrastructure networks from unsecured external connections, significantly reducing the risk of cyberattacks and malware infiltration. By physically separating the ICS network from corporate IT and the internet, organizations ensure operational technology (OT) environments remain secure and resilient against ransomware and advanced persistent threats (APTs). This strategy is essential for protecting SCADA systems, programmable logic controllers (PLCs), and other vital components in sectors such as energy, manufacturing, and water treatment.
Airgap Strategies in Healthcare Data Security
Airgap strategies in healthcare data security involve isolating critical systems from unsecured networks to prevent cyber threats and unauthorized access. Implementing physical separation between electronic medical records (EMR) systems and the internet ensures robust protection against ransomware attacks. These measures safeguard patient data integrity and comply with HIPAA regulations by minimizing digital exposure.
Physical vs. Virtual Airgap: Key Differences
Physical airgap refers to the complete physical isolation of a network or system, ensuring no direct or indirect communication channels exist, such as disconnected hardware or standalone devices. Virtual airgap employs software-based controls like network segmentation, stringent firewalls, and access policies to mimic isolation within connected systems, enhancing flexibility without full disconnection. Key differences lie in the level of isolation, with physical airgaps providing absolute security through hardware separation, whereas virtual airgaps balance security and connectivity using virtualization and software-defined network controls.
Challenges of Maintaining Airgap Security
Maintaining airgap security presents significant challenges such as ensuring physical isolation to prevent unauthorized data transfer and managing the risk of insider threats exploiting removable media or compromised devices. Strict protocols are required to monitor and control any data exchange, often leading to operational inefficiencies and increased costs. Furthermore, the complexity of sustaining hardware integrity and software updates without network connectivity amplifies vulnerability to sophisticated cyberattacks.
Future Trends: Evolving Airgap Technologies
Emerging airgap technologies integrate AI-driven monitoring and quantum encryption to enhance cyber-physical isolation, preventing unauthorized data transmissions in critical infrastructure. Future airgaps utilize blockchain for immutable audit trails, ensuring data integrity in isolated networks. Innovations in micro-segmentation and zero-trust architectures further strengthen airgapped environments against sophisticated cyber threats.
example of airgap in security Infographic
 samplerz.com
samplerz.com