A backdoor in firmware is a hidden method that allows unauthorized access to a device's hardware or software at a fundamental level. One common example is the Intel Management Engine (ME), which operates within Intel chipsets and has been found to contain backdoor-like features that enable remote control and monitoring of the hardware without user knowledge. This low-level access poses significant security risks as it can bypass traditional operating system protections and firmware integrity checks. Another notable instance is the Juniper Networks ScreenOS firmware incident discovered in 2015, where attackers implanted a backdoor that granted unauthorized VPN access. This backdoor manipulated cryptographic keys within the firmware, allowing attackers to decrypt network traffic and control Juniper devices covertly. Such firmware backdoors highlight the importance of rigorous security audits and firmware validation in network infrastructure devices.
Table of Comparison
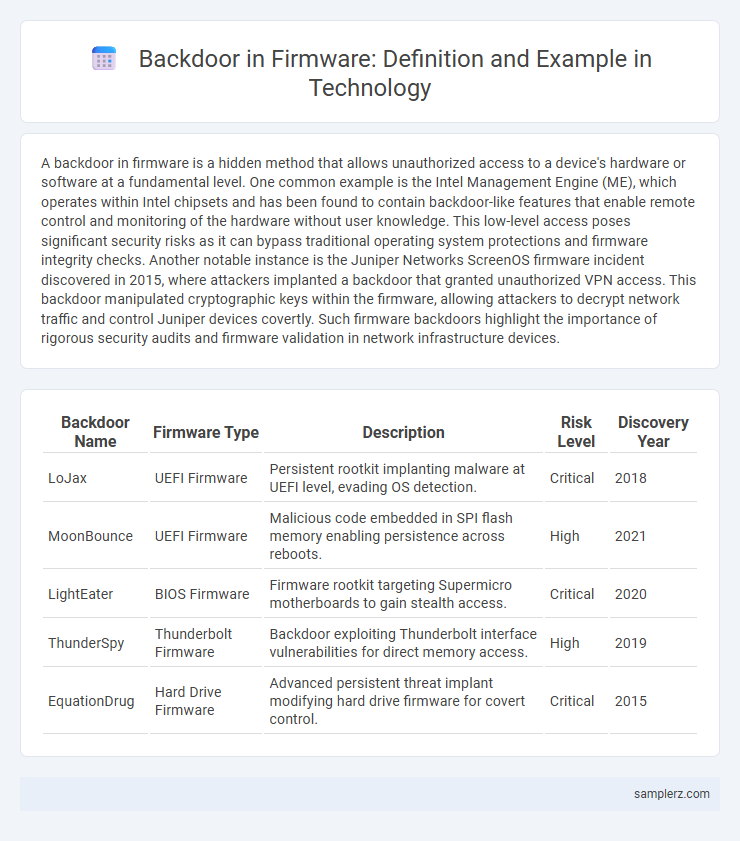
| Backdoor Name | Firmware Type | Description | Risk Level | Discovery Year |
|---|---|---|---|---|
| LoJax | UEFI Firmware | Persistent rootkit implanting malware at UEFI level, evading OS detection. | Critical | 2018 |
| MoonBounce | UEFI Firmware | Malicious code embedded in SPI flash memory enabling persistence across reboots. | High | 2021 |
| LightEater | BIOS Firmware | Firmware rootkit targeting Supermicro motherboards to gain stealth access. | Critical | 2020 |
| ThunderSpy | Thunderbolt Firmware | Backdoor exploiting Thunderbolt interface vulnerabilities for direct memory access. | High | 2019 |
| EquationDrug | Hard Drive Firmware | Advanced persistent threat implant modifying hard drive firmware for covert control. | Critical | 2015 |
Introduction to Firmware Backdoors
Firmware backdoors are hidden malicious code embedded within the low-level software controlling hardware devices, allowing unauthorized access or manipulation without user detection. An infamous example is the Lenovo Superfish incident, where pre-installed firmware included ad-serving backdoors compromising security. Such vulnerabilities in firmware can bypass traditional security measures, making detection and remediation critically challenging in technology environments.
Historical Cases of Firmware Backdoors
The 2017 case of the Supermicro firmware backdoor revealed attackers embedding malicious code deep within server motherboards, compromising hardware at a foundational level. Another notable instance occurred in 2015 when security researchers uncovered backdoors in Huawei routers, enabling unauthorized access through hidden firmware vulnerabilities. These historical firmware backdoor cases underscore persistent risks in supply chain security and the critical need for rigorous firmware auditing.
Notable Firmware Backdoor Incidents
One notable firmware backdoor incident involved the Supermicro motherboards discovered in 2018, where hidden malicious code enabled unauthorized remote access, compromising global supply chains. Another critical case occurred with Lenovo laptops in 2017, where a pre-installed firmware backdoor allowed attackers to execute privileged commands without user consent. These incidents highlight persistent vulnerabilities in firmware security that threaten hardware integrity and data protection across industries.
Techniques Used to Implant Backdoors in Firmware
Techniques used to implant backdoors in firmware include code injection during the manufacturing process, exploiting vulnerabilities in firmware update mechanisms, and embedding malicious code within firmware bootloaders. Attackers often manipulate firmware binaries to gain persistent low-level access, bypassing traditional security controls. Hardware-based rootkits and modified firmware images are common methods to stealthily compromise devices at the firmware layer.
Real-World Example: Stuxnet and Firmware Manipulation
Stuxnet exemplifies a sophisticated backdoor in firmware by targeting Siemens PLCs used in Iran's nuclear facilities, manipulating the firmware to subtly alter centrifuge speeds and sabotage operations without detection. This malware infiltrated firmware to maintain persistence and evade conventional antivirus tools, demonstrating how firmware-level backdoors can compromise critical industrial control systems. The Stuxnet case underscores the importance of securing firmware against unauthorized code modifications to prevent covert attacks on essential infrastructure.
Case Study: Juniper Networks ScreenOS Backdoor
The Juniper Networks ScreenOS backdoor exposed a critical vulnerability in firewall firmware, allowing unauthorized remote access through a hardcoded password. Discovered in 2015, this backdoor exploited the Dual_EC_DRBG cryptographic algorithm to decrypt VPN traffic, compromising the confidentiality and integrity of network communications. This case highlighted significant risks in embedded firmware security and the importance of rigorous code auditing in network hardware.
Analysis of Lenovo Laptop Firmware Backdoor
The analysis of Lenovo laptop firmware backdoor revealed a hidden root-level access mechanism embedded within the BIOS, allowing unauthorized remote control and data extraction. Researchers discovered specifically crafted code segments that bypassed standard authentication protocols, exposing critical vulnerabilities in system integrity and user privacy. This firmware backdoor highlights significant security risks inherent in pre-installed software, emphasizing the need for rigorous firmware auditing and secure update practices.
Vulnerabilities in IoT Device Firmware
Backdoor vulnerabilities in IoT device firmware often arise from hardcoded credentials or unsecured debug interfaces, granting unauthorized remote access to attackers. Exploits targeting these backdoors can lead to device hijacking, data breaches, and the creation of botnets like Mirai. Securing firmware through code audits, encryption, and regular updates is essential to mitigate these risks in connected devices.
Methods for Detecting Firmware Backdoors
Firmware backdoors can be detected using methods such as firmware integrity verification through cryptographic hashes and digital signatures, which ensure the code has not been tampered with. Behavioral analysis techniques examine firmware activity for unusual patterns or unauthorized access attempts. Advanced approaches also include the use of hardware-assisted debugging and side-channel analysis to uncover hidden backdoors embedded within firmware components.
Preventive Measures Against Firmware Backdoors
Implementing secure boot processes and cryptographic firmware signing effectively prevents unauthorized firmware modifications and backdoor insertions. Regular firmware integrity checks using hardware-based Root of Trust mechanisms identify and mitigate potential backdoors during device initialization. Employing multi-factor authentication and strict access controls further reduces the risk of exploitation in embedded system firmware.
example of backdoor in firmware Infographic
 samplerz.com
samplerz.com