A rootkit is a type of malware designed to gain unauthorized root or administrative access to a computer system while concealing its presence. One well-known example of a rootkit is the Sony BMG rootkit discovered in 2005, which was embedded in music CDs to prevent copying. This rootkit hid itself deeply within the operating system, making it difficult for users to detect and remove. Another prominent example is the Stuxnet rootkit, used in cyber warfare to target industrial control systems. Stuxnet employed a rootkit to mask its malicious activities from security software and system administrators. The complexity of Stuxnet highlighted the potential of rootkits to facilitate sophisticated, state-sponsored cyberattacks by maintaining stealth and persistence within targeted networks.
Table of Comparison
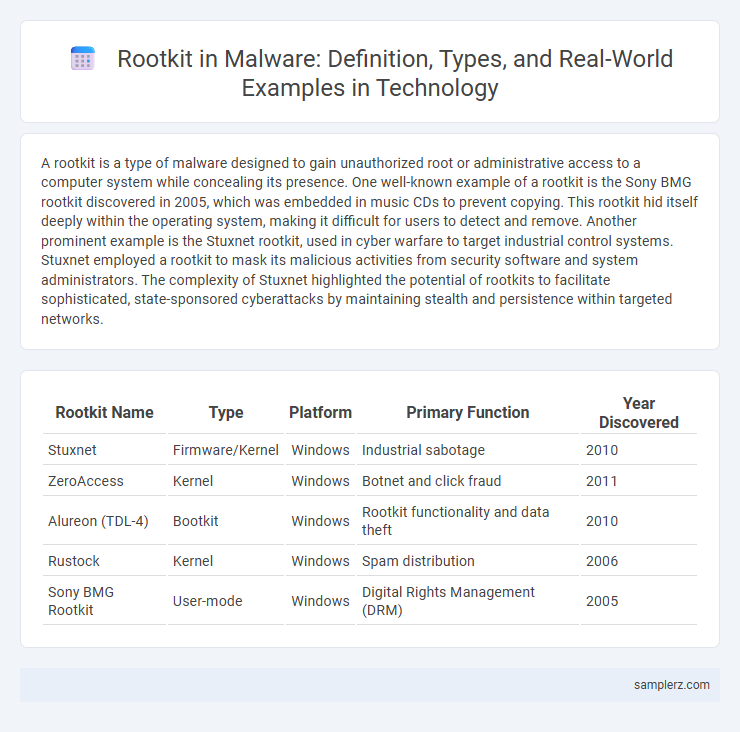
| Rootkit Name | Type | Platform | Primary Function | Year Discovered |
|---|---|---|---|---|
| Stuxnet | Firmware/Kernel | Windows | Industrial sabotage | 2010 |
| ZeroAccess | Kernel | Windows | Botnet and click fraud | 2011 |
| Alureon (TDL-4) | Bootkit | Windows | Rootkit functionality and data theft | 2010 |
| Rustock | Kernel | Windows | Spam distribution | 2006 |
| Sony BMG Rootkit | User-mode | Windows | Digital Rights Management (DRM) | 2005 |
Introduction to Rootkits in Malware
Rootkits are stealthy types of malware designed to gain unauthorized root-level access to a computer system while remaining hidden from detection. Examples include the Sony BMG rootkit, which secretly installed itself to enforce digital rights management, and the Stuxnet worm, which used rootkit techniques to conceal its sabotage of Iranian nuclear facilities. Rootkits manipulate system processes and kernel modules, making them extremely difficult for traditional antivirus software to detect or remove.
Notorious Rootkit Examples in History
Notorious rootkits like Sony BMG's XCP and the Rustock botnet have shaped cybersecurity challenges by enabling stealthy malware infections that evade detection. The Sony BMG XCP rootkit, embedded in music CDs in 2005, covertly installed software that compromised user control and sparked widespread backlash. Rustock, active from 2006 to 2011, powered massive spam campaigns while hiding deep within infected Windows systems, showcasing the destructive potential of persistent rootkits in malware history.
Sony BMG Rootkit Scandal
The Sony BMG Rootkit scandal exposed a controversial DRM rootkit embedded in millions of music CDs in 2005, designed to prevent illegal copying but secretly installed hidden software on users' computers. This rootkit created significant security vulnerabilities by masking malicious processes, making infected systems susceptible to further exploitation. The incident sparked widespread criticism, legal action, and increased awareness of rootkits as dangerous malware components in digital rights management technologies.
Stuxnet: Rootkit Techniques in Cyberwarfare
Stuxnet exemplifies advanced rootkit techniques by stealthily manipulating industrial control systems to sabotage Iran's nuclear program. Its rootkit components concealed malicious code within legitimate processes, evading detection by traditional antivirus software and security measures. This malware's sophistication demonstrated the strategic use of rootkits in cyberwarfare, altering the cybersecurity landscape significantly.
ZeroAccess Rootkit: Threat Analysis
ZeroAccess Rootkit is a sophisticated malware known for its stealth and persistence, primarily targeting Windows operating systems. It employs advanced techniques such as kernel-mode rootkit capabilities to hide its presence and execute fraudulent activities like click fraud and Bitcoin mining. Security experts classify ZeroAccess as a significant threat due to its ability to evade detection by traditional antivirus software and its widespread impact on infected systems.
Necurs Rootkit: Spambot Infrastructure
Necurs Rootkit is a notorious example of rootkit malware, primarily utilized as a spambot infrastructure to distribute massive volumes of spam emails and facilitate various cybercriminal activities. It employs advanced stealth techniques to evade detection by antivirus software, maintaining persistent control over infected systems. This rootkit's modular design allows it to deliver additional payloads, making it a versatile tool in large-scale botnet operations.
TDSS/Alureon Rootkit Case Study
The TDSS/Alureon rootkit exemplifies advanced malware designed to evade detection by manipulating kernel-level operations in Windows OS. This rootkit enables persistent backdoor access, intercepts system calls, and facilitates unauthorized data exfiltration while bypassing traditional antivirus software. Understanding the TDSS/Alureon case is critical for developing robust cybersecurity defenses against stealthy kernel-mode threats.
Rustock Rootkit: Spam Botnet Operations
Rustock Rootkit is a notorious example of malware employing rootkit techniques to maintain stealth and control over infected systems. Primarily used to operate a massive spam botnet, Rustock injected itself into the Windows kernel, evading detection by antivirus software and facilitating the distribution of billions of spam emails globally. Its sophisticated stealth capabilities and persistence mechanisms highlight significant challenges in cybersecurity defense against rootkit-based malware.
Examples of Rootkit Detection Evasion
Rootkits like Sony BMG's XCP and Stuxnet exemplify advanced evasion techniques by hiding processes and files from traditional antivirus tools. These rootkits manipulate kernel-level operations to intercept system calls, effectively masking their presence from security software. Sophisticated detection evasion includes using encrypted payloads and hooking system APIs to prevent logging or alerting during malicious activities.
Modern Rootkit Mitigation Strategies
Modern rootkit mitigation strategies prioritize behavior-based detection to identify stealthy malware that manipulates low-level system processes, leveraging kernel-mode and hypervisor-level monitoring to prevent unauthorized access. Techniques such as Secure Boot and Trusted Platform Module (TPM) integration ensure system integrity by verifying the authenticity of bootloaders and kernel drivers. Endpoint detection and response (EDR) solutions combined with machine learning algorithms enhance real-time identification of rootkit signatures and anomalous activities, minimizing the risk of persistent threats like rootkits embedded in advanced malware.
example of rootkit in malware Infographic
 samplerz.com
samplerz.com