A canarytoken is a digital tripwire used in intrusion detection systems to identify unauthorized access within a network. It acts as a decoy, such as a fake URL, file, or database credential, which triggers an alert when an attacker interacts with it. This technology leverages entity-specific data patterns to detect and respond to malicious activity before substantial damage occurs. In practical use, canarytokens can be embedded within sensitive files or system configurations, mimicking critical assets to mislead intruders. When the canarytoken is accessed or altered, it generates detailed logs capturing attacker behavior and access points. These logs provide valuable entity data for cybersecurity teams to analyze intrusion methods and reinforce defense mechanisms.
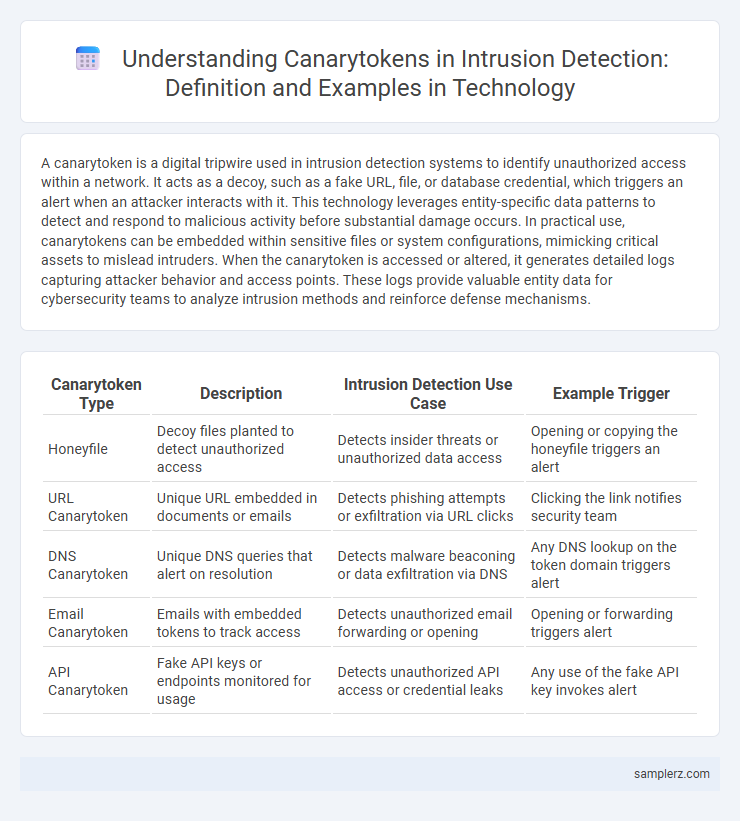
Table of Comparison
| Canarytoken Type | Description | Intrusion Detection Use Case | Example Trigger |
|---|---|---|---|
| Honeyfile | Decoy files planted to detect unauthorized access | Detects insider threats or unauthorized data access | Opening or copying the honeyfile triggers an alert |
| URL Canarytoken | Unique URL embedded in documents or emails | Detects phishing attempts or exfiltration via URL clicks | Clicking the link notifies security team |
| DNS Canarytoken | Unique DNS queries that alert on resolution | Detects malware beaconing or data exfiltration via DNS | Any DNS lookup on the token domain triggers alert |
| Email Canarytoken | Emails with embedded tokens to track access | Detects unauthorized email forwarding or opening | Opening or forwarding triggers alert |
| API Canarytoken | Fake API keys or endpoints monitored for usage | Detects unauthorized API access or credential leaks | Any use of the fake API key invokes alert |
Introduction to Canarytokens in Intrusion Detection
Canarytokens are stealthy digital tripwires embedded in systems to detect unauthorized access or breaches by alerting administrators when triggered. These tokens can take various forms such as fake URLs, documents, or API keys that, when interacted with by an intruder, send real-time notifications to security teams. Integrating canarytokens into intrusion detection strategies enhances early threat detection and minimizes the window of attacker persistence within networks.
How Canarytokens Enhance Security Monitoring
Canarytokens enhance security monitoring by acting as deceptive digital tripwires embedded within critical systems or files, triggering immediate alerts when accessed by unauthorized users. These tokens provide real-time, actionable intelligence on intrusion attempts, enabling rapid incident response and minimizing potential damage. Integrating canarytokens into cybersecurity frameworks significantly improves threat detection accuracy and reduces false positives in security operations.
Common Types of Canarytokens for Intrusion Detection
Common types of canarytokens used in intrusion detection include honey files, which trigger alerts when accessed or copied, and fake database credentials embedded in applications that notify administrators upon unauthorized use. Email canarytokens monitor unauthorized email openings or link clicks, while web beacon tokens detect malicious web scraping or automated scanning activities. Network-based canarytokens like unused IP addresses or honey DNS records serve to identify suspicious network reconnaissance or lateral movement attempts within a system.
Real-World Examples of Canarytoken Deployment
Organizations deploy canarytokens embedded in sensitive files and URLs within corporate networks to trigger alerts when accessed by unauthorized users. Financial institutions often use canarytoken-laden documents disguised as audit reports to detect insider threats and data exfiltration attempts. Cloud service providers integrate canarytokens into API keys and serverless functions, enabling rapid identification of compromised credentials and malicious activity.
Step-by-Step Guide to Creating a Canarytoken
Creating a canarytoken for intrusion detection involves generating a unique, trackable bait such as a fake document or URL designed to alert administrators when accessed. Begin by selecting a canarytoken provider, then customize the token with specific triggers like email, DNS, or HTTP requests that will notify you upon interaction. Deploy the token strategically within your network or sensitive files to monitor unauthorized access and gain actionable intelligence on potential intrusions.
Detecting Lateral Movement with Canarytokens
Canarytokens can detect lateral movement by embedding unique, trackable tokens in files, endpoints, or network shares that alert administrators upon unauthorized access. These tokens provide real-time signals when an intruder attempts to move laterally across a network, triggering immediate investigation. Implementing canarytokens enhances intrusion detection capabilities by identifying attackers before significant damage occurs.
Integrating Canarytokens into Existing Security Systems
Integrating Canarytokens into existing security systems enhances intrusion detection by providing customizable, low-cost sensors that trigger alerts upon unauthorized access. These tokens can be embedded in files, URLs, or network protocols to create deceptive bait, enabling security teams to detect lateral movement and privilege escalation attempts in real-time. Combining Canarytokens with SIEM and SOAR platforms offers automated incident response and enriched threat intelligence for comprehensive cybersecurity defense.
Case Study: Successful Intrusion Detection with Canarytokens
A financial institution detected a sophisticated cyberattack by deploying canarytokens embedded in confidential documents, which triggered instant alerts upon unauthorized access. The early warning enabled the security team to isolate compromised systems, preventing data exfiltration and minimizing operational disruption. This case study demonstrates the effectiveness of canarytokens as proactive intrusion detection tools in real-world security environments.
Limitations and Best Practices for Canarytoken Usage
Canarytokens provide early intrusion detection by embedding decoy artifacts that alert administrators when accessed, though they often generate false positives if not properly contextualized within network behavior. Effective deployment demands strategic placement in sensitive directories and regular token rotation to minimize attacker awareness and false alarms. Continuous monitoring and integration with broader security information and event management (SIEM) systems enhance response capabilities and reduce operational overhead.
Future Trends of Canarytokens in Cybersecurity
Future trends of canarytokens in cybersecurity highlight their integration with AI-driven anomaly detection systems, enhancing real-time threat identification and response. Advanced canarytokens will leverage machine learning to adaptively generate decoys tailored to evolving attack vectors, increasing the precision of intrusion detection. The convergence of canarytokens with automated incident response platforms promises to streamline threat mitigation and reduce dwell time in complex network environments.
example of canarytoken in intrusion detection Infographic
 samplerz.com
samplerz.com