Cold boot in memory forensics refers to the process of analyzing volatile data retrieved from a computer's RAM immediately after a system reboot or power cycle. This technique involves capturing residual data left in memory chips, which can reveal crucial information such as encryption keys, running processes, and system states. Cold boot attacks exploit the remanence effect in DRAM, allowing forensic experts to recover sensitive data that would otherwise be lost during normal shutdown. In practical terms, cold boot analysis requires rapidly cooling the memory modules to slow down data degradation, followed by transferring the modules to a forensic rig for imaging and examination. Tools used in cold boot forensics include memory dump utilities and hex editors designed to extract and analyze residual data. This method has become a valuable asset in cybersecurity investigations, particularly for uncovering evidence in cases involving data breaches and unauthorized access.
Table of Comparison
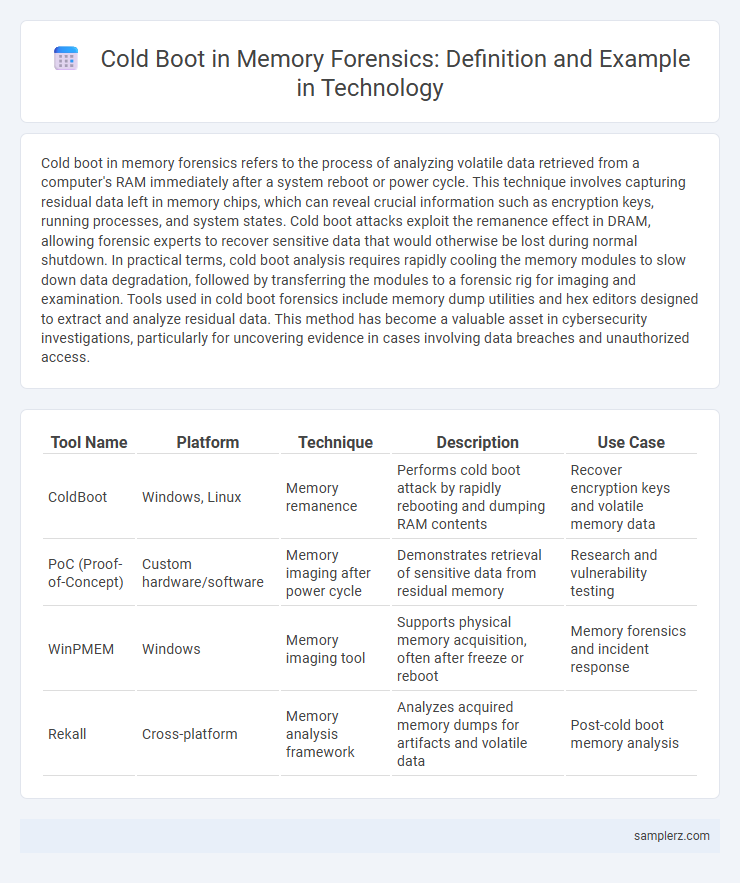
| Tool Name | Platform | Technique | Description | Use Case |
|---|---|---|---|---|
| ColdBoot | Windows, Linux | Memory remanence | Performs cold boot attack by rapidly rebooting and dumping RAM contents | Recover encryption keys and volatile memory data |
| PoC (Proof-of-Concept) | Custom hardware/software | Memory imaging after power cycle | Demonstrates retrieval of sensitive data from residual memory | Research and vulnerability testing |
| WinPMEM | Windows | Memory imaging tool | Supports physical memory acquisition, often after freeze or reboot | Memory forensics and incident response |
| Rekall | Cross-platform | Memory analysis framework | Analyzes acquired memory dumps for artifacts and volatile data | Post-cold boot memory analysis |
Understanding Cold Boot Attacks in Memory Forensics
Cold boot attacks exploit the remanence effect in DRAM, where data remains intact for seconds to minutes after power loss, enabling recovery of encryption keys and sensitive information during memory acquisition. In memory forensics, cold boot techniques involve rapidly rebooting a system or transferring RAM modules to another device to capture volatile memory contents before they fade. Understanding cold boot attacks is critical for developing defensive strategies and enhancing forensic tools to preserve and analyze volatile memory evidence securely.
Key Cold Boot Incident Case Studies
Key cold boot incident case studies in memory forensics highlight the vulnerability of encryption keys stored in RAM after a sudden power loss. Notable examples include the 2008 demonstration by Halderman et al., where encryption keys were successfully extracted from DDR memory modules seconds after shutdown. These cases underscore the importance of securing volatile memory and implementing countermeasures like full memory encryption and rapid key destruction to prevent unauthorized retrieval during cold boot attacks.
Step-by-Step Example: Performing a Cold Boot Attack
Performing a cold boot attack involves forcibly rebooting a target computer to capture residual data in RAM before it fully powers down, exploiting data remanence. First, the attacker cools the memory modules to extend data retention time, then immediately transfers the modules to a prepared device for memory dumping. Extracted memory images are analyzed using forensic tools to recover sensitive information such as encryption keys or passwords.
Tools Commonly Used for Cold Boot Forensics
Tools commonly used for cold boot forensics include Volatility, which analyzes memory dumps for volatile data recovery, and Firewire for direct memory access to capture RAM content during system boot. Rekall is another prominent tool offering features to extract remnants of encryption keys and other transient artifacts from cold boot memory images. These tools enable digital investigators to recover critical information lost in standard shutdown processes by exploiting physical memory snapshots.
Analyzing Recovered Data from Cold Boot Attacks
Cold boot attacks exploit residual data in a computer's RAM by rapidly rebooting the system to capture volatile memory contents before they dissipate. Analyzing recovered data involves extracting encryption keys, plaintext passwords, and other sensitive information stored in memory, which forensic tools reconstruct for further investigation. Memory forensic techniques leverage patterns and signatures within the recovered data to identify artifacts critical for proving unauthorized access or malware activity.
Visualization of Memory Data Post-Cold Boot
Cold boot attacks exploit residual data in RAM after power loss, enabling extraction of sensitive information for forensic analysis. Visualization tools like Volatility and Rekall transform raw memory dumps into structured formats, revealing process states, network connections, and hidden malware. Effective visualization enhances understanding of system behavior post-attack, facilitating accurate incident response and threat mitigation.
Challenges in Cold Boot Evidence Collection
Cold boot evidence collection in memory forensics faces significant challenges due to rapid data decay and volatility after system shutdown, making timely acquisition critical. Physical access restrictions and encryption mechanisms further complicate the extraction of coherent memory dumps. Effective strategies require advanced hardware interfaces and specialized tools to preserve memory integrity and counteract data obfuscation.
Notable Vulnerabilities Exploited by Cold Boot Attacks
Cold boot attacks exploit the residual data left in DRAM modules immediately after power loss, allowing attackers to recover encryption keys and sensitive information from memory. This vulnerability is notable in full-disk encryption systems such as BitLocker and FileVault, where key material remains accessible in memory for seconds to minutes post-shutdown. Memory forensics tools leverage these cold boot vulnerabilities to extract volatile data, highlighting the critical need for hardware-level encryption and memory scrambling technologies to mitigate risk.
Mitigation Techniques Against Cold Boot Forensics
Mitigation techniques against cold boot forensics include full disk encryption (FDE) to protect data even when memory is physically accessed, and disabling or encrypting RAM contents to prevent residual data recovery during a cold boot attack. Implementing Trusted Platform Module (TPM) hardware ensures secure key storage, reducing the risk of key extraction from memory. Employing memory scrambling and rapid memory overwriting during shutdown further limits the viable data remnants accessible through cold boot analysis.
Future Trends in Cold Boot Memory Analysis
Future trends in cold boot memory analysis emphasize advancements in volatile memory acquisition techniques, enabling more reliable data retrieval from encryption keys and ephemeral secrets. Enhanced machine learning algorithms assist in automating pattern recognition within memory dumps, improving accuracy in identifying malicious artifacts. Integration with cloud-based forensics platforms accelerates analysis speed while maintaining the integrity of volatile data during incident response.
example of coldboot in memory forensics Infographic
 samplerz.com
samplerz.com