Bluejacking is a Bluetooth-based technique that enables users to send unsolicited messages to nearby devices without pairing. This practice involves creating a contact entry with a custom message and broadcasting it to discoverable Bluetooth-enabled devices within a range of approximately 10 meters. Typically used for prank messaging or marketing purposes, bluejacking exploits the object push profile (OPP) in Bluetooth technology. In technology contexts, bluejacking highlights both the potential for innovative communication and the security vulnerabilities in wireless protocols. Devices such as smartphones, laptops, and tablets that have Bluetooth enabled in discoverable mode are susceptible to receiving bluejacked messages. Data involved in bluejacking primarily consists of small text strings sent via contact cards, illustrating how simple exploits can leverage standard Bluetooth functionalities.
Table of Comparison
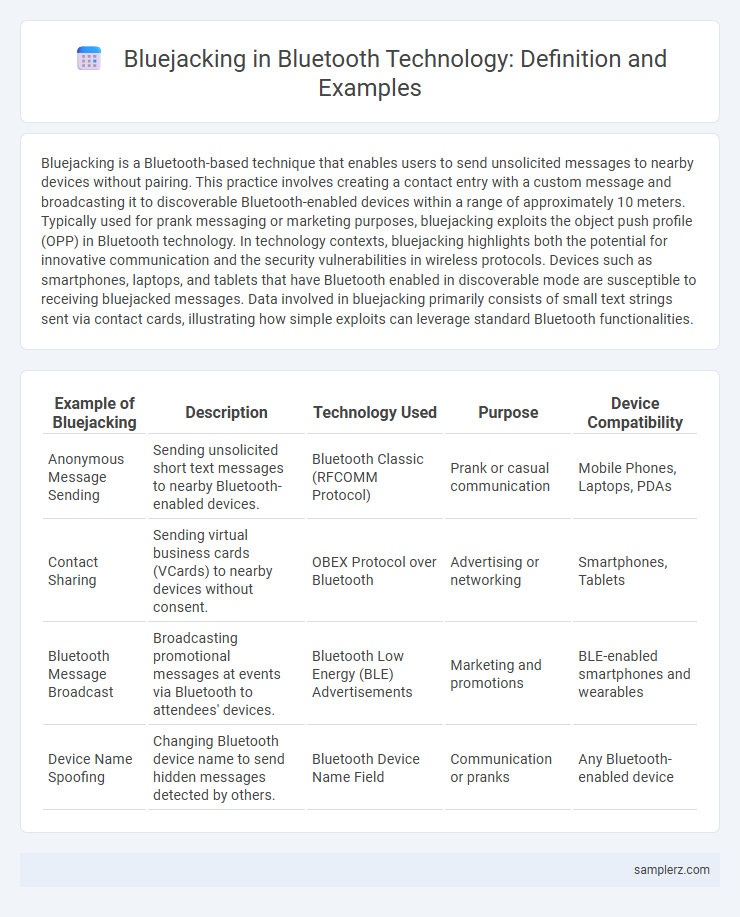
| Example of Bluejacking | Description | Technology Used | Purpose | Device Compatibility |
|---|---|---|---|---|
| Anonymous Message Sending | Sending unsolicited short text messages to nearby Bluetooth-enabled devices. | Bluetooth Classic (RFCOMM Protocol) | Prank or casual communication | Mobile Phones, Laptops, PDAs |
| Contact Sharing | Sending virtual business cards (VCards) to nearby devices without consent. | OBEX Protocol over Bluetooth | Advertising or networking | Smartphones, Tablets |
| Bluetooth Message Broadcast | Broadcasting promotional messages at events via Bluetooth to attendees' devices. | Bluetooth Low Energy (BLE) Advertisements | Marketing and promotions | BLE-enabled smartphones and wearables |
| Device Name Spoofing | Changing Bluetooth device name to send hidden messages detected by others. | Bluetooth Device Name Field | Communication or pranks | Any Bluetooth-enabled device |
Introduction to Bluejacking in Bluetooth Technology
Bluejacking in Bluetooth technology involves sending unsolicited messages to nearby Bluetooth-enabled devices without permission. This technique exploits the Bluetooth protocol's ability to exchange contact information, commonly using the device name field to transmit short text messages. Bluejacking highlights both the versatility and potential security concerns in wireless device communication within short-range Bluetooth networks.
How Bluejacking Works: A Brief Overview
Bluejacking works by sending unsolicited messages to nearby Bluetooth-enabled devices, exploiting the device's ability to receive contact information or text messages via Bluetooth. The sender creates a vCard or a message that is transmitted to discoverable devices within Bluetooth range, typically up to 10 meters. This method does not require pairing or hacking into the device, making it a simple yet unexpected form of communication.
Real-World Instances of Bluejacking
Bluejacking has been documented in crowded places like airports and shopping malls, where users send anonymous messages to nearby Bluetooth-enabled devices. In 2004, a university student used bluejacking to display humorous notes on peers' phones during lectures, sparking awareness of Bluetooth security issues. Retailers have also experimented with bluejacking to engage customers by sending promotional messages to Bluetooth devices within proximity.
Common Devices Targeted by Bluejacking
Common devices targeted by bluejacking include smartphones, tablets, and laptops equipped with Bluetooth capabilities. These devices often receive unsolicited messages or contact requests due to their discoverable Bluetooth settings, making them vulnerable to bluejacking attacks. Wearable technology such as smartwatches is also frequently targeted because of their constant Bluetooth connectivity.
Notable Bluejacking Scenarios in Public Spaces
Notable bluejacking scenarios in public spaces include sending anonymous messages to strangers' Bluetooth-enabled devices on public transportation, airports, and coffee shops, creating unexpected social interactions or sharing promotional content. Retailers leverage bluejacking to deliver targeted advertisements or coupons directly to potential customers' smartphones within store proximity. Security experts warn that while bluejacking is generally harmless, it highlights vulnerabilities in Bluetooth protocols that could be exploited for phishing or spreading malware in crowded public environments.
Bluejacking in the Workplace: Case Studies
Bluejacking in the workplace involves sending unsolicited Bluetooth messages to employees' devices, often resulting in security concerns and workplace distractions. Case studies highlight incidents where bluejacking disrupted meetings or spread prank messages in office environments. These examples emphasize the need for strict Bluetooth usage policies and device security measures to prevent unauthorized access and maintain productivity.
Bluejacking at Events: Demonstrations and Examples
Bluejacking at events often involves sending unsolicited messages or contact cards to nearby Bluetooth-enabled devices in crowded spaces like conferences or concerts. Demonstrations typically showcase how easily attendees can receive unexpected texts or images, highlighting potential privacy concerns in public settings. Examples include prank messages during tech expos or promotional content sent during marketing events to raise awareness about Bluetooth security.
Digital Advertising through Bluejacking
Bluejacking in Bluetooth allows marketers to send unsolicited promotional messages to nearby devices, leveraging proximity-based digital advertising without requiring internet connectivity. This method targets potential customers in crowded environments such as malls or events by delivering branded content, coupons, or alerts directly to their smartphones. Bluejacking enhances engagement by creating personalized, interactive ad experiences while maintaining a low-cost, location-specific marketing strategy.
Social Interactions Sparked by Bluejacking
Bluejacking enables spontaneous social interactions by allowing users to send anonymous messages or business cards to nearby Bluetooth-enabled devices, often sparking curiosity and conversations among strangers. This technique leverages Bluetooth's limited range to facilitate playful or unexpected communication in public spaces like cafes, conferences, or public transportation. As a result, bluejacking has become a unique tool for initiating social connections and enhancing network engagement through creative digital interaction.
Preventing Unauthorized Bluejacking: Tips and Tools
Preventing unauthorized bluejacking involves disabling Bluetooth visibility and setting devices to non-discoverable mode, which limits exposure to unsolicited messages. Utilizing trusted device lists and employing Bluetooth security apps can enhance protection by filtering unknown connection attempts. Regular software updates are crucial to patch security vulnerabilities and maintain robust defense against bluejacking exploits.
example of bluejacking in Bluetooth Infographic
 samplerz.com
samplerz.com