Fuzzing is a software testing technique used to identify vulnerabilities by inputting random or malformed data into a program. This method targets security flaws such as buffer overflows and memory leaks by generating unexpected inputs that the software may not handle correctly. Popular fuzzing tools include AFL (American Fuzzy Lop) and LibFuzzer, which automate the process and improve code robustness. Fuzzing tests focus on analyzing the software's behavior under abnormal conditions to uncover hidden bugs that traditional testing might miss. The technique is widely applied in testing operating systems, web browsers, and network protocols, making it valuable for cybersecurity. Companies often integrate fuzzing into continuous integration pipelines to enhance software security proactively.
Table of Comparison
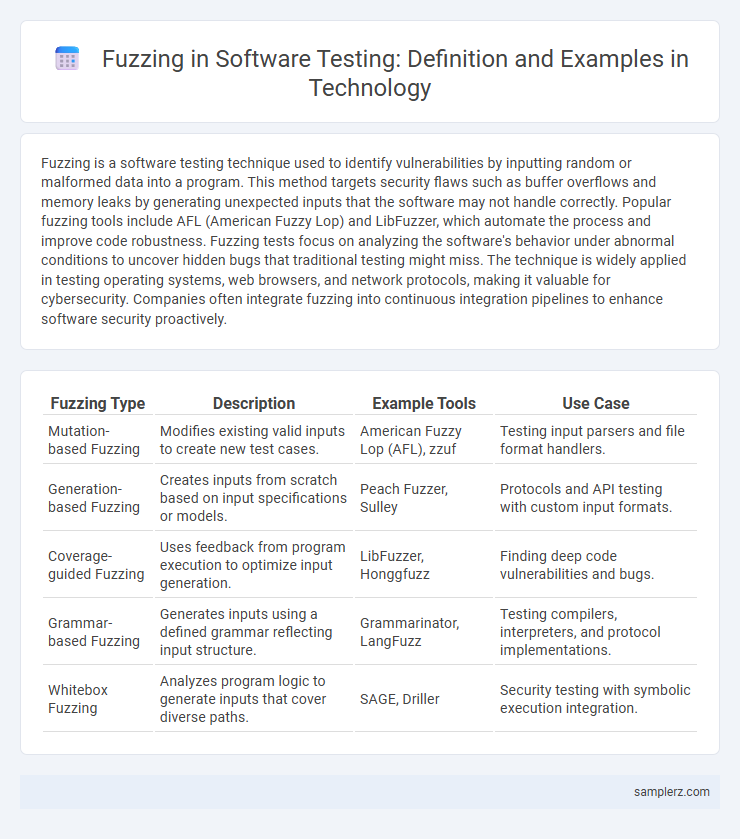
| Fuzzing Type | Description | Example Tools | Use Case |
|---|---|---|---|
| Mutation-based Fuzzing | Modifies existing valid inputs to create new test cases. | American Fuzzy Lop (AFL), zzuf | Testing input parsers and file format handlers. |
| Generation-based Fuzzing | Creates inputs from scratch based on input specifications or models. | Peach Fuzzer, Sulley | Protocols and API testing with custom input formats. |
| Coverage-guided Fuzzing | Uses feedback from program execution to optimize input generation. | LibFuzzer, Honggfuzz | Finding deep code vulnerabilities and bugs. |
| Grammar-based Fuzzing | Generates inputs using a defined grammar reflecting input structure. | Grammarinator, LangFuzz | Testing compilers, interpreters, and protocol implementations. |
| Whitebox Fuzzing | Analyzes program logic to generate inputs that cover diverse paths. | SAGE, Driller | Security testing with symbolic execution integration. |
Introduction to Fuzzing in Software Testing
Fuzzing in software testing involves automatically generating and inputting large volumes of random, unexpected, or malformed data into software to identify security vulnerabilities and bugs. This technique helps detect memory leaks, crashes, and assertion failures that traditional testing methods might overlook. Tools like AFL (American Fuzzy Lop) and libFuzzer enable efficient fuzz testing by evolving inputs based on program feedback to maximize code coverage.
Key Concepts of Fuzzing Techniques
Fuzzing techniques involve automatically generating and inputting malformed or unexpected data into software to identify vulnerabilities and bugs. Key concepts include mutation-based fuzzing, which alters existing valid inputs, and generation-based fuzzing, which creates inputs from scratch based on protocol specifications. Coverage-guided fuzzing enhances effectiveness by using runtime feedback to focus on unexplored code paths and increase bug discovery rates.
Benefits of Fuzzing in Modern Software Development
Fuzzing in software testing enhances security by automatically detecting vulnerabilities and unexpected bugs through random input generation, reducing the risk of exploitation. It accelerates the debugging process by exposing edge cases that traditional testing methods often miss, improving overall software reliability. Integration of fuzzing tools enables continuous testing in CI/CD pipelines, ensuring consistent quality and safety in modern software development.
Popular Fuzzing Tools and Frameworks
Popular fuzzing tools and frameworks such as American Fuzzy Lop (AFL), libFuzzer, and OSS-Fuzz are widely used to identify security vulnerabilities and software bugs by generating random inputs for testing. AFL employs genetic algorithms to optimize test cases, enhancing bug detection efficiency in diverse software environments. Google's OSS-Fuzz provides continuous fuzzing integration with extensive open-source projects, significantly improving code reliability and security.
Real-World Case Studies: Fuzzing in Action
Google's OSS-Fuzz project exemplifies fuzzing in software testing by continuously identifying vulnerabilities in widely used open-source software like Chromium and OpenSSL. Microsoft incorporated fuzz testing into its DevOps pipeline, uncovering critical bugs in Windows components before release. Real-world case studies demonstrate that fuzzing effectively enhances software security by discovering obscure defects that traditional testing methods often miss.
Step-by-Step Example: Fuzzing a Web Application
Fuzzing a web application begins by identifying input vectors such as forms, URL parameters, and API endpoints where unexpected data can be injected. A fuzzing tool like OWASP ZAP or Burp Suite systematically generates and sends malformed or random input to these entry points, monitoring the application for crashes, memory leaks, or unexpected behavior. The collected results help developers pinpoint vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows, improving the security and robustness of the web application.
Fuzzing in Open Source Projects: Practical Applications
Fuzzing in open source projects involves automated input generation to uncover vulnerabilities and bugs by feeding unexpected or random data into software. Projects like LLVM's LibFuzzer and Google's OSS-Fuzz leverage continuous fuzz testing to improve code security and stability across multiple open source codebases. These practical applications enable early detection of critical bugs, reduce manual testing efforts, and enhance overall software robustness.
Detecting Vulnerabilities through Fuzz Testing
Fuzz testing detects vulnerabilities by inputting numerous random or malformed data into software to trigger unexpected behaviors or crashes. This technique uncovers security flaws such as buffer overflows, memory leaks, and input validation errors, which traditional testing might miss. Tools like American Fuzzy Lop (AFL) and LibFuzzer automate fuzzing, enhancing the identification of critical software weaknesses.
Challenges and Limitations of Fuzzing
Fuzzing in software testing often faces challenges such as generating meaningful test inputs that effectively explore complex code paths and uncover deep security vulnerabilities. Limitations include high resource consumption due to extensive execution time and difficulty in analyzing crashes caused by non-deterministic or environment-dependent faults. These factors hinder fuzzing's ability to guarantee complete software coverage and detection of subtle bugs in large-scale, real-world applications.
Future Trends in Fuzzing Technology
Future trends in fuzzing technology emphasize the integration of machine learning algorithms to enhance automatic input generation and vulnerability detection. Advances in cloud-based distributed fuzzing platforms enable scalable testing of complex software systems, significantly reducing time-to-discovery for security flaws. Emerging approaches combine fuzzing with symbolic execution and runtime analysis, improving precision and coverage in identifying hard-to-detect bugs.
example of fuzzing in software testing Infographic
 samplerz.com
samplerz.com