A backdoor in software refers to a hidden method that allows unauthorized access to a computer system or application. These secret access points bypass normal authentication mechanisms, enabling attackers to control the system without detection. Common examples include hardcoded credentials in code, undocumented debug modes, or hidden network ports left open for remote access. In cybersecurity, one notable example is the backdoor discovered in the Juniper Networks ScreenOS, which allowed attackers to decrypt VPN traffic. Another instance is the Sony BMG rootkit scandal, where a backdoor in the DRM software exposed user systems to exploitation. These examples highlight the importance of thorough code audits and continuous monitoring to detect and mitigate backdoors in software products.
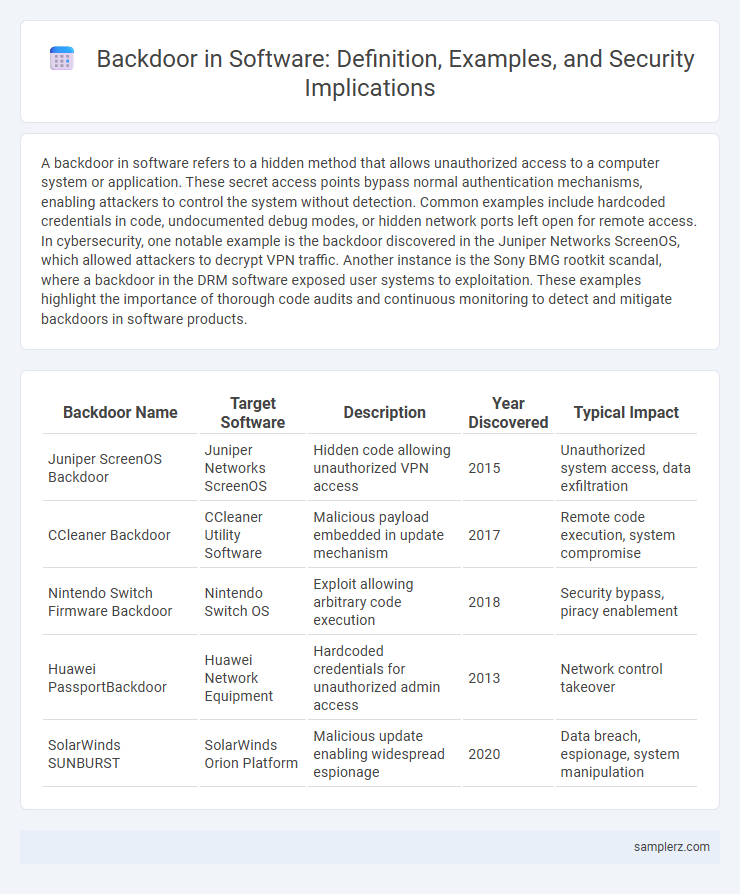
Table of Comparison
| Backdoor Name | Target Software | Description | Year Discovered | Typical Impact |
|---|---|---|---|---|
| Juniper ScreenOS Backdoor | Juniper Networks ScreenOS | Hidden code allowing unauthorized VPN access | 2015 | Unauthorized system access, data exfiltration |
| CCleaner Backdoor | CCleaner Utility Software | Malicious payload embedded in update mechanism | 2017 | Remote code execution, system compromise |
| Nintendo Switch Firmware Backdoor | Nintendo Switch OS | Exploit allowing arbitrary code execution | 2018 | Security bypass, piracy enablement |
| Huawei PassportBackdoor | Huawei Network Equipment | Hardcoded credentials for unauthorized admin access | 2013 | Network control takeover |
| SolarWinds SUNBURST | SolarWinds Orion Platform | Malicious update enabling widespread espionage | 2020 | Data breach, espionage, system manipulation |
Understanding Backdoors: Definition and Overview
Backdoors in software are covert methods that provide unauthorized access to systems, often embedded intentionally or through vulnerabilities. Common examples include hidden user accounts, undocumented administrative privileges, or malicious code like the infamous Sony BMG rootkit. Understanding these entry points is crucial for cybersecurity professionals to safeguard systems against exploitation and data breaches.
Historical Examples of Software Backdoors
The infamous 1993 Microsoft Windows backdoor, discovered by security analyst Mark Russinovich, allowed unauthorized system access through a hidden password within the Telnet service. Another historically significant backdoor was the Juniper Networks incident in 2015, where unauthorized code inserted into the ScreenOS operating system enabled attackers to decrypt VPN traffic. These cases highlight critical vulnerabilities embedded in widely-used software platforms, emphasizing the ongoing need for rigorous security audits and patch management.
Famous Backdoor Incidents in Commercial Software
The Sony BMG rootkit scandal of 2005 exposed a notorious backdoor embedded in commercial music CDs, which stealthily installed software compromising user security. In 2013, the Juniper Networks firewall backdoor incident revealed unauthorized code allowing attackers to decrypt VPN traffic, highlighting significant vulnerabilities in network security appliances. Microsoft's Windows XP and 2003 Server also contained the "NSA backdoor" known as the Dual_EC_DRBG cryptographic flaw, which undermined encryption protocols until patched.
Backdoors in Open Source Projects
Backdoors in open source projects, such as the infamous Linux Mint compromise in 2016, exploit the transparency of source code to inject malicious functionality unnoticed by the community. Attackers often embed hidden access points within legitimate code repositories or dependency libraries, leveraging trust and widespread adoption to maximize impact. Rigorous code audits and continuous monitoring of pull requests are essential techniques to detect and prevent backdoor vulnerabilities in open source ecosystems.
How Backdoors are Planted in Software
Backdoors in software are typically planted through deliberate code insertion by malicious insiders or by attackers exploiting vulnerabilities during development or deployment stages. Common methods include injecting hidden access points via compromised source code repositories, embedding secret credentials in updates, or manipulating third-party libraries and dependencies. Attackers often leverage weak code review processes and insufficient security auditing to introduce these covert entry mechanisms undetected.
Insider Threats: Developers Introducing Backdoors
Insider threats frequently manifest when developers intentionally insert backdoors into software, bypassing security protocols to maintain unauthorized access. These hidden access points exploit privileged code knowledge, often going undetected during standard audits and testing procedures. Organizations face significant risks as such backdoors undermine encryption, data integrity, and system trustworthiness, making comprehensive code reviews and behavioral monitoring essential.
Government-Mandated Backdoors: Case Studies
Government-mandated backdoors in software often arise from legislation requiring tech companies to provide law enforcement with access to encrypted data, exemplified by the FBI's demand for a backdoor in Apple's iPhone during the San Bernardino case. In 2016, the UK's Investigatory Powers Act compelled providers like Vodafone and BT to implement capabilities for government surveillance, effectively introducing backdoors. These cases highlight ongoing tensions between national security imperatives and user privacy in technology policy.
Real-World Exploitation of Software Backdoors
The 2013 revelations of the NSA's exploitation of software backdoors, such as those in Windows operating systems, demonstrated how intelligence agencies leveraged hidden access points for surveillance and cyber-espionage. The SolarWinds supply chain attack in 2020 showcased real-world exploitation where threat actors inserted malicious backdoors into software updates, compromising thousands of organizations globally. These incidents highlight the critical security risks posed by undisclosed backdoors in widely used software frameworks and emphasize the need for robust code auditing practices.
Techniques for Detecting Backdoors in Code
Techniques for detecting backdoors in software code involve static and dynamic analysis methods, such as code review, pattern recognition, and behavior monitoring during runtime. Automated tools employing machine learning algorithms can identify anomalies and suspicious code snippets indicative of hidden backdoors. Integrating anomaly detection systems and leveraging signature-based detection enhances the identification and mitigation of unauthorized access points embedded within the codebase.
Preventing and Mitigating Software Backdoors
Implementing rigorous code reviews and utilizing automated static analysis tools significantly enhance the detection of software backdoors before deployment. Leveraging secure coding practices and integrating continuous monitoring systems mitigate risks by identifying anomalies indicative of unauthorized access. Employing multi-factor authentication and strict access controls further prevent exploitation of backdoors in software environments.
example of backdoor in software Infographic
 samplerz.com
samplerz.com