Zeroization in cryptography refers to the process of securely erasing sensitive data such as cryptographic keys from memory to prevent unauthorized access. Hardware security modules (HSMs) often implement zeroization by erasing keys immediately upon detecting tampering or unauthorized access attempts. This process ensures that cryptographic secrets cannot be recovered even if the device is compromised. Zeroization is crucial for maintaining the confidentiality and integrity of encrypted information in secure communications. Software implementations may overwrite key material in memory with zeros or random data before freeing the memory space. By eliminating remnants of sensitive data, zeroization reduces the risk of key leakage through memory dumps or forensic analysis.
Table of Comparison
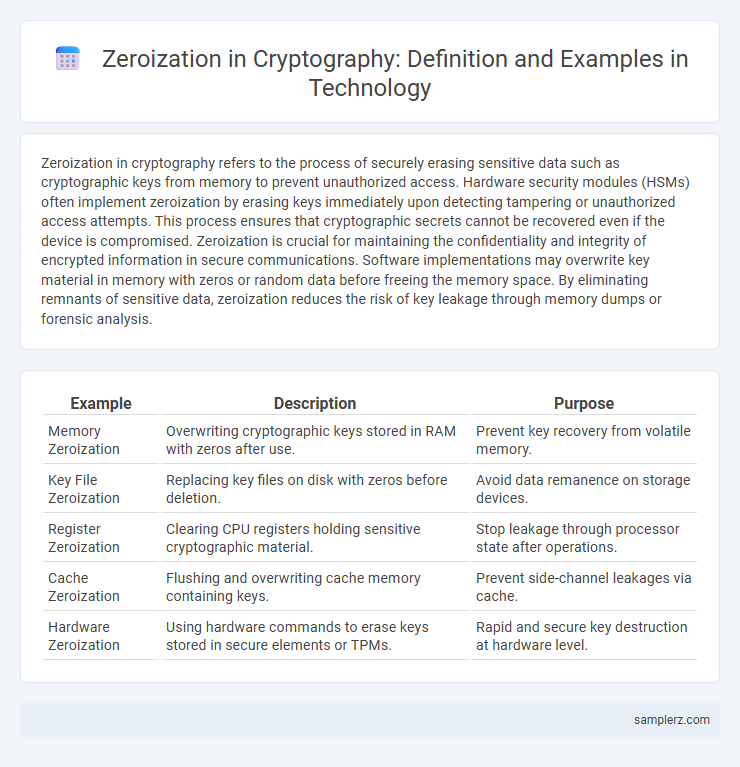
| Example | Description | Purpose |
|---|---|---|
| Memory Zeroization | Overwriting cryptographic keys stored in RAM with zeros after use. | Prevent key recovery from volatile memory. |
| Key File Zeroization | Replacing key files on disk with zeros before deletion. | Avoid data remanence on storage devices. |
| Register Zeroization | Clearing CPU registers holding sensitive cryptographic material. | Stop leakage through processor state after operations. |
| Cache Zeroization | Flushing and overwriting cache memory containing keys. | Prevent side-channel leakages via cache. |
| Hardware Zeroization | Using hardware commands to erase keys stored in secure elements or TPMs. | Rapid and secure key destruction at hardware level. |
Understanding Zeroization in Cryptography
Zeroization in cryptography refers to the process of securely erasing sensitive cryptographic keys and data from memory to prevent unauthorized recovery. This technique is critical in hardware security modules (HSMs), smart cards, and secure processors, where automated zeroization triggers upon tamper detection or system reset. Effective zeroization ensures that once cryptographic operations are complete, no residual information remains, thereby strengthening overall data confidentiality and system integrity.
Importance of Zeroization for Secure Systems
Zeroization in cryptography entails securely erasing sensitive data such as encryption keys and passwords to prevent unauthorized access or data leakage. Implementing zeroization techniques, like overwriting memory with random data before deallocation, is critical for maintaining the confidentiality and integrity of cryptographic systems. Secure zeroization safeguards against memory scraping attacks, hardware tampering, and minimizes residual data remnants that could be exploited by adversaries.
Common Algorithms Requiring Zeroization
Common cryptographic algorithms requiring zeroization include AES, RSA, and ECC, where sensitive key materials must be securely erased from memory after use to prevent unauthorized recovery. Zeroization ensures that secret keys stored in volatile RAM or hardware security modules are overwritten with zeros or random data, mitigating risks from memory dumps or side-channel attacks. Failure to zeroize cryptographic keys in these algorithms can lead to critical security vulnerabilities and potential data breaches.
Zeroization in Hardware Security Modules (HSMs)
Zeroization in Hardware Security Modules (HSMs) involves securely erasing cryptographic keys and sensitive data to prevent unauthorized access after use or during tampering attempts. This process typically employs physical destruction methods or overwriting key memory areas with random or zero data to ensure irrecoverability. Effective zeroization protocols enhance HSM security by mitigating risks of key extraction in environments requiring compliance with standards like FIPS 140-2 and Common Criteria.
Software Libraries Implementing Zeroization
Popular cryptographic software libraries like OpenSSL, libsodium, and Bouncy Castle implement zeroization to securely erase sensitive data such as encryption keys and passwords from memory. These libraries use dedicated functions to overwrite memory buffers immediately after use, preventing potential data leakage through memory dumps or side-channel attacks. Effective zeroization techniques in software libraries are critical for maintaining cryptographic security and protecting against unauthorized access to secret information.
Real-World Zeroization Attack Scenarios
Real-world zeroization attack scenarios demonstrate how attackers exploit improper cryptographic key erasure to retrieve sensitive information from devices such as hardware security modules (HSMs) or encrypted storage. In 2018, researchers revealed a vulnerability in certain IoT devices where residual cryptographic keys remained in memory after system resets, enabling unauthorized access. These incidents emphasize the critical need for robust zeroization protocols to prevent key leakage during device initialization and decommissioning.
Zeroization Best Practices in Application Development
Zeroization in cryptography involves securely erasing sensitive data such as cryptographic keys and passwords from memory to prevent unauthorized access. Best practices in application development include implementing explicit memory clearing routines immediately after key usage and leveraging hardware features like secure enclaves or trusted execution environments for enhanced data protection. Developers should also enforce strict key lifecycle management policies, ensuring cryptographic material is zeroized during application shutdown or upon detected security events.
Automated Zeroization Techniques and Tools
Automated zeroization techniques in cryptography involve systematically erasing sensitive data such as encryption keys from memory to prevent unauthorized access. Tools like hardware security modules (HSMs) and cryptographic libraries implement automatic zeroization during key lifecycle events, ensuring secure disposal of cryptographic material. These technologies enhance security by minimizing residual data exposure and supporting compliance with data protection standards.
Regulatory Standards Mandating Zeroization
Regulatory standards such as FIPS 140-3 mandate zeroization to ensure the secure erasure of cryptographic keys and sensitive data during device shutdown or tampering scenarios. Compliance with NIST guidelines requires cryptographic modules to implement zeroization procedures that prevent data remanence and unauthorized access. These standards are critical in sectors like government and finance, where strict data protection and cryptographic key management policies are enforced.
Future Trends in Zeroization for Cryptographic Security
Future trends in zeroization for cryptographic security emphasize automated hardware-based memory cleansing techniques that eliminate residual data immediately after cryptographic operations. Advanced secure enclaves and trusted execution environments increasingly integrate zeroization protocols to mitigate side-channel attacks and ensure ephemeral key material is reliably erased. Research in post-quantum cryptography accelerates the adoption of zeroization strategies that address emerging quantum-resilient algorithms and protect against novel forms of cryptographic key leakage.
example of zeroization in cryptography Infographic
 samplerz.com
samplerz.com