Cold boot in data recovery refers to the process of retrieving data from a computer's memory immediately after a hard shutdown or power loss. This technique exploits the remanence effect in volatile memory modules, such as DRAM, where data remains temporarily after power is cut. Experts initiate a cold boot by powering on the system and quickly accessing the data to recover sensitive information before it fades away. This method is often used in forensic investigations and cybersecurity incident responses to recover encryption keys or other critical data. Cold boot attacks highlight vulnerabilities in memory security, emphasizing the need for robust encryption and memory cleansing. Technologies focusing on volatile memory protection are essential to prevent unauthorized data retrieval through cold boot methods.
Table of Comparison
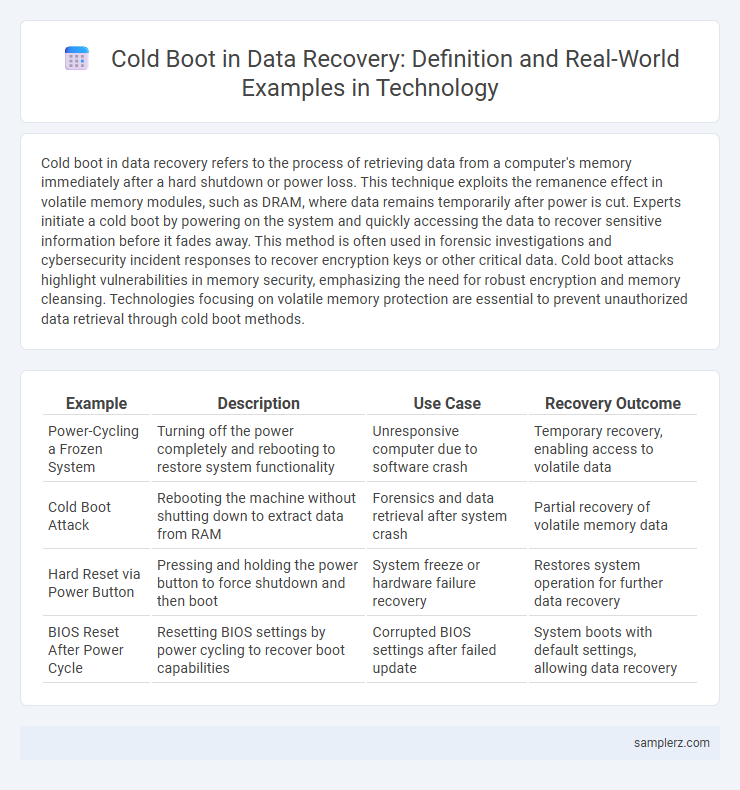
| Example | Description | Use Case | Recovery Outcome |
|---|---|---|---|
| Power-Cycling a Frozen System | Turning off the power completely and rebooting to restore system functionality | Unresponsive computer due to software crash | Temporary recovery, enabling access to volatile data |
| Cold Boot Attack | Rebooting the machine without shutting down to extract data from RAM | Forensics and data retrieval after system crash | Partial recovery of volatile memory data |
| Hard Reset via Power Button | Pressing and holding the power button to force shutdown and then boot | System freeze or hardware failure recovery | Restores system operation for further data recovery |
| BIOS Reset After Power Cycle | Resetting BIOS settings by power cycling to recover boot capabilities | Corrupted BIOS settings after failed update | System boots with default settings, allowing data recovery |
Understanding Cold Boot Attacks in Data Recovery
Cold boot attacks exploit the remanent data in a computer's RAM by physically rebooting the system without a proper shutdown, enabling recovery of sensitive information like encryption keys and passwords. This attack technique relies on the fact that data in volatile memory does not vanish instantaneously and can be retrieved before it decays completely. Understanding cold boot attacks is crucial for enhancing data recovery methods and implementing robust encryption standards to protect volatile memory contents.
How Cold Boot Techniques Retrieve Lost Data
Cold boot techniques retrieve lost data by exploiting the residual data remaining in volatile memory (DRAM) after a computer shutdown, enabling forensic experts to capture information before it dissipates. This process involves rapidly cooling the memory modules to slow data degradation, then extracting raw memory dumps using specialized hardware tools. These raw dumps are analyzed to recover encryption keys, passwords, or sensitive data that are otherwise inaccessible after power loss.
Real-World Examples of Cold Boot Data Recovery
In real-world scenarios, cold boot data recovery has proven effective in retrieving encryption keys from a compromised system's volatile memory shortly after shutdown, enabling forensic investigators to access encrypted drives. Notable cases include law enforcement agencies recovering critical evidence by freezing RAM modules to prolong data retention, which allows extraction of volatile data that would otherwise be lost. This technique underscores the importance of rapid response in memory forensics during digital investigations targeting encrypted or locked devices.
Step-by-Step Cold Boot Data Recovery Process
The cold boot data recovery process begins by powering off the computer and immediately rebooting it from a removable storage device containing specialized recovery software. Next, the software extracts residual data from the RAM before it dissipates, capturing volatile information like encryption keys and unsaved files. Finally, the recovered data is transferred to a secure storage medium for analysis and restoration, enabling retrieval of critical information after sudden system failures.
Hardware Requirements for Cold Boot Data Recovery
Cold boot data recovery requires a computer system equipped with volatile memory modules such as DDR4 or DDR5 RAM, which retain residual data briefly after power loss. Essential hardware components include a reliable memory imaging tool, a forensic workstation with high processing power, and specialized interfaces like PCIe or DDR memory readers to extract raw data. Maintaining a low ambient temperature through cooling devices can enhance data retention time, facilitating successful recovery from RAM during a cold boot attack.
Risks and Limitations of Cold Boot in Data Recovery
Cold boot data recovery involves retrieving information from a computer's RAM immediately after a reboot or power loss, but it carries significant risks such as data corruption and loss due to memory volatility. The process is limited by hardware encryption and modern memory management techniques that often render sensitive data inaccessible or overwritten quickly. Furthermore, cold boot attacks require physical access and specialized tools, reducing their practicality and effectiveness in secure or live environments.
Comparing Cold Boot With Other Data Recovery Methods
Cold boot data recovery leverages the residual data left in a computer's RAM immediately after a system shutdown, enabling forensic extraction of volatile information that traditional hard drive recovery methods miss. Unlike software-based recovery tools relying on intact file systems, cold boot attacks capture encryption keys and session data stored transiently, providing a unique advantage in retrieving sensitive information. This approach contrasts with disk imaging or logical recovery techniques by targeting hardware-level artifacts, offering a deeper layer of data salvage especially in encrypted or partially corrupted environments.
Tools Commonly Used for Cold Boot Data Recovery
Cold boot data recovery commonly utilizes memory imaging tools such as Volatility and Rekall to capture volatile data from a system's RAM immediately after reboot. Hardware-based tools like PCILeech enable direct memory access, allowing extraction of sensitive information during the cold boot process. Forensic toolkits integrating cold boot techniques often incorporate these software and hardware solutions to maximize data retrieval efficiency in volatile memory analysis.
Legal and Ethical Issues in Cold Boot Data Recovery
Cold boot data recovery involves retrieving volatile memory content after a system reboot, raising significant legal and ethical concerns regarding unauthorized access to sensitive information and potential violations of data privacy laws such as GDPR and HIPAA. Forensic investigators must ensure chain of custody and obtain proper legal authorization to prevent evidence tampering and uphold admissibility in court. Ethical use mandates transparency and adherence to organizational policies to protect individual rights and maintain trust in the data recovery process.
Protecting Your Data From Cold Boot Exploits
Cold boot attacks exploit residual data in a computer's memory to access sensitive information during system restarts, posing a significant threat to data security. Implementing full disk encryption and utilizing hardware-based security modules can effectively protect data from unauthorized retrieval after a cold boot. Regularly updating firmware and enabling memory scrambling features further mitigate the risk of cold boot exploits in data recovery scenarios.
example of cold boot in data recovery Infographic
 samplerz.com
samplerz.com