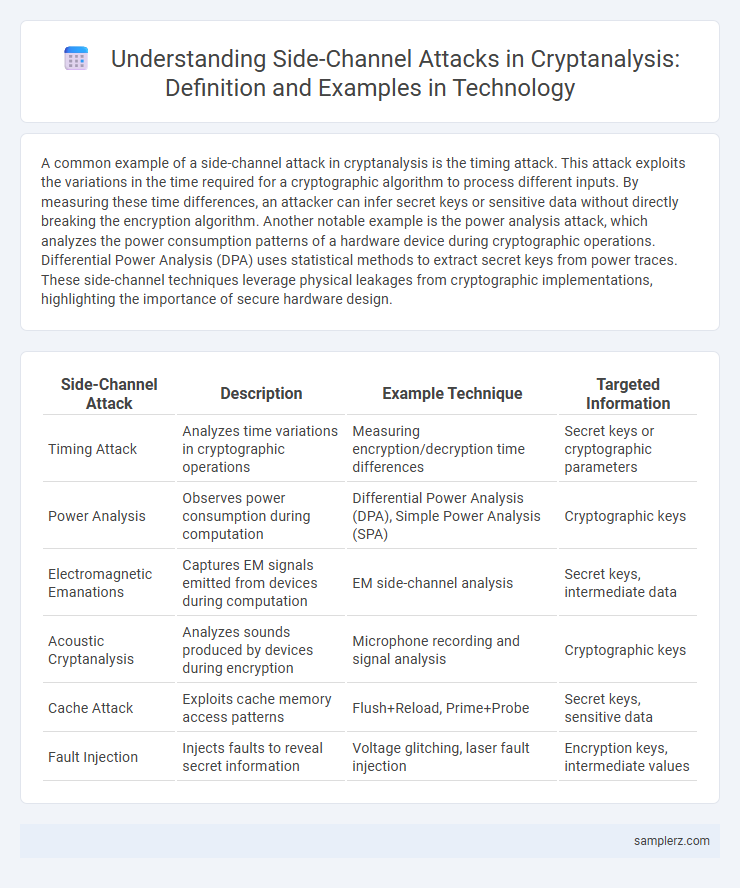
A common example of a side-channel attack in cryptanalysis is the timing attack. This attack exploits the variations in the time required for a cryptographic algorithm to process different inputs. By measuring these time differences, an attacker can infer secret keys or sensitive data without directly breaking the encryption algorithm. Another notable example is the power analysis attack, which analyzes the power consumption patterns of a hardware device during cryptographic operations. Differential Power Analysis (DPA) uses statistical methods to extract secret keys from power traces. These side-channel techniques leverage physical leakages from cryptographic implementations, highlighting the importance of secure hardware design.
Table of Comparison
| Side-Channel Attack | Description | Example Technique | Targeted Information |
|---|---|---|---|
| Timing Attack | Analyzes time variations in cryptographic operations | Measuring encryption/decryption time differences | Secret keys or cryptographic parameters |
| Power Analysis | Observes power consumption during computation | Differential Power Analysis (DPA), Simple Power Analysis (SPA) | Cryptographic keys |
| Electromagnetic Emanations | Captures EM signals emitted from devices during computation | EM side-channel analysis | Secret keys, intermediate data |
| Acoustic Cryptanalysis | Analyzes sounds produced by devices during encryption | Microphone recording and signal analysis | Cryptographic keys |
| Cache Attack | Exploits cache memory access patterns | Flush+Reload, Prime+Probe | Secret keys, sensitive data |
| Fault Injection | Injects faults to reveal secret information | Voltage glitching, laser fault injection | Encryption keys, intermediate values |
Power Analysis Attacks in Cryptographic Systems
Power Analysis Attacks exploit fluctuations in a device's power consumption to extract secret cryptographic keys, making them a critical threat in embedded systems security. Differential Power Analysis (DPA) and Simple Power Analysis (SPA) are prominent techniques that analyze power traces during encryption operations, revealing sensitive information without interrupting the cryptographic algorithm. Countermeasures such as power consumption masking and randomization are essential for protecting smart cards, secure microcontrollers, and IoT devices from these side-channel attacks.
Timing Attacks on Encryption Algorithms
Timing attacks exploit variations in the time taken by encryption algorithms to process data, revealing secret keys through precise measurement of execution durations. These side-channel attacks target algorithms like RSA and AES, where conditional branches or key-dependent operations introduce measurable timing discrepancies. Attackers use statistical analysis of response times to recover cryptographic keys without directly breaking the mathematical foundations of the algorithms.
Electromagnetic Emanations in Data Leakage
Electromagnetic emanations emitted during cryptographic operations serve as a critical side-channel that can expose sensitive data such as encryption keys. Attackers use specialized probes and spectrum analyzers to capture these unintentional signals, enabling them to reconstruct secret information without direct access to the cryptographic device. Understanding and mitigating electromagnetic leakage is essential for securing hardware cryptosystems against eavesdropping and data breaches.
Cache Side-Channel Exploits in Modern CPUs
Cache side-channel exploits in modern CPUs leverage timing differences in cache memory access to extract sensitive cryptographic keys. Attackers measure variations in cache hits and misses during encryption operations to infer secret data without direct access to the cryptographic algorithm. Techniques such as Flush+Reload and Prime+Probe are commonly used to exploit CPU cache architecture, posing significant threats to hardware security.
Acoustic Cryptanalysis Techniques
Acoustic cryptanalysis exploits sound emissions from computing devices to extract secret information, such as cryptographic keys, by analyzing variations in noises produced during cryptographic operations. Techniques like keystroke sound analysis and electromagnetic noise correlation have successfully retrieved RSA and AES keys from vulnerable hardware. These side-channel attacks highlight critical security risks in cryptographic implementations, emphasizing the need for hardware-level countermeasures against acoustic leakage.
Fault Injection Attacks in Cryptography
Fault injection attacks manipulate hardware or software components by introducing deliberate errors to extract confidential cryptographic keys. Techniques like voltage glitching, electromagnetic pulses, and laser injections cause faults during encryption, leading to erroneous outputs that reveal secret information. These side-channel attacks exploit physical vulnerabilities rather than algorithmic weaknesses, making them a critical security threat in cryptographic implementations.
Differential Power Analysis (DPA) in Practice
Differential Power Analysis (DPA) is a prominent side-channel attack in cryptanalysis that exploits power consumption patterns during cryptographic operations to extract secret keys. Practically, DPA monitors variations in the electrical power usage of hardware devices performing encryption, leveraging statistical methods to correlate power traces with key hypotheses. This technique has been effectively applied against smart cards, embedded systems, and IoT devices, revealing vulnerabilities in otherwise secure cryptographic implementations.
Simple Power Analysis (SPA) Vulnerabilities
Simple Power Analysis (SPA) vulnerabilities exploit variations in a device's power consumption to extract cryptographic keys by observing power traces during encryption or decryption processes. Devices implementing RSA or AES algorithms without adequate countermeasures are particularly susceptible to SPA attacks, where attackers identify key-dependent operations through distinct power consumption patterns. Mitigations such as constant power consumption techniques, masking, and algorithmic blinding help reduce the risk of key leakage through SPA in embedded systems and smart cards.
Rowhammer Attacks in Hardware Security
Rowhammer attacks exploit hardware vulnerabilities by repeatedly accessing specific memory rows to induce bit flips in adjacent rows, undermining memory integrity in DRAM modules. This side-channel technique enables attackers to bypass traditional security mechanisms, potentially escalating privileges or extracting sensitive cryptographic keys. Effective defenses include error-correcting code (ECC) memory, targeted refresh algorithms, and hardware-based isolation techniques to mitigate Rowhammer-induced faults.
Remote Side-Channel Attacks Over Networks
Remote side-channel attacks over networks exploit indirect leakages such as timing variations, power consumption, or electromagnetic emissions to extract cryptographic keys without physical access. Techniques like cache timing attacks and remote power analysis leverage network latency and data processing patterns to compromise encryption algorithms. These attacks emphasize vulnerabilities in hardware and software implementations of cryptographic systems accessible via network communication channels.
example of side-channel in cryptanalysis Infographic
 samplerz.com
samplerz.com