A rootkit is a type of malicious software designed to gain unauthorized root or administrative access to an operating system while remaining hidden from users and security software. An example of a rootkit in an operating system is the Sony BMG rootkit incident in 2005, where the copy protection software installed on music CDs stealthily embedded itself into Windows systems, compromising security and privacy. Rootkits manipulate the kernel or system files, making detection difficult and allowing attackers to control affected systems covertly. In modern operating systems like Windows and Linux, rootkits can be categorized into user-mode and kernel-mode based on their level of operation. Kernel-mode rootkits are particularly dangerous as they tamper with core components such as device drivers or system call tables, providing attackers with deep control over system functions. Detection tools often rely on anomaly detection and memory scanning techniques to identify rootkit signatures or behavior patterns hidden within system processes and files.
Table of Comparison
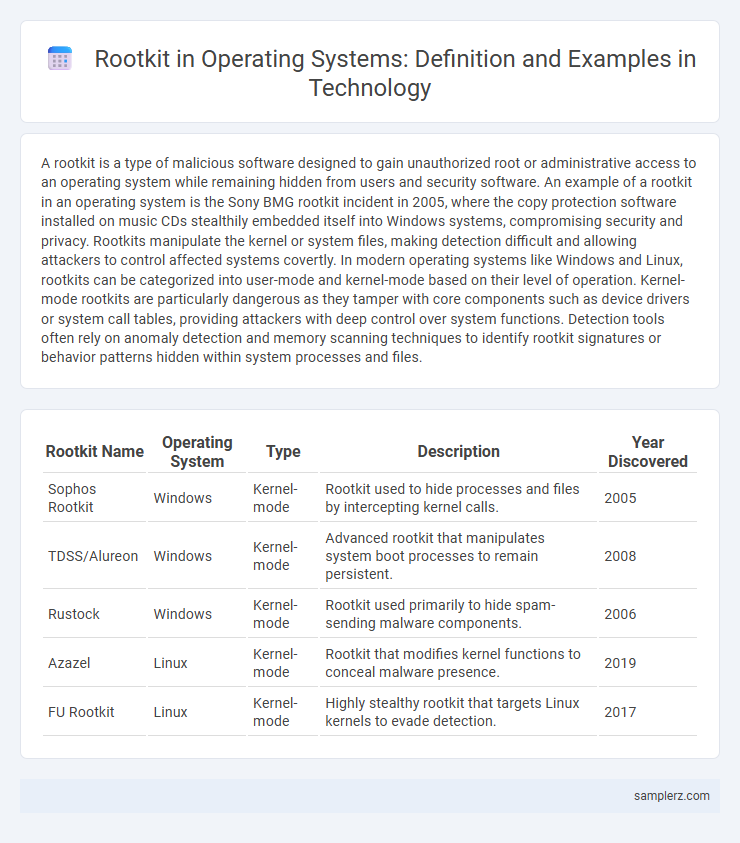
| Rootkit Name | Operating System | Type | Description | Year Discovered |
|---|---|---|---|---|
| Sophos Rootkit | Windows | Kernel-mode | Rootkit used to hide processes and files by intercepting kernel calls. | 2005 |
| TDSS/Alureon | Windows | Kernel-mode | Advanced rootkit that manipulates system boot processes to remain persistent. | 2008 |
| Rustock | Windows | Kernel-mode | Rootkit used primarily to hide spam-sending malware components. | 2006 |
| Azazel | Linux | Kernel-mode | Rootkit that modifies kernel functions to conceal malware presence. | 2019 |
| FU Rootkit | Linux | Kernel-mode | Highly stealthy rootkit that targets Linux kernels to evade detection. | 2017 |
Introduction to Rootkits in Operating Systems
Rootkits in operating systems are malicious software designed to gain unauthorized access while concealing their presence from users and security tools. A prominent example is the Sony BMG rootkit discovered in 2005, which embedded itself deep into Windows OS to hide copy protection mechanisms. These rootkits manipulate system-level processes or kernel modules to maintain persistent control and evade detection.
Notorious Historical Rootkit Examples
Stuxnet stands as one of the most notorious rootkits, targeting Windows operating systems to sabotage Iranian nuclear facilities through hidden malware components. The Sony BMG rootkit scandal involved a copy protection software embedded in music CDs that installed stealthy rootkit technology on users' Windows machines, compromising security and privacy. Another example is the Alureon rootkit, known for intercepting banking credentials and communications in Windows environments, illustrating the persistent threat of rootkits in operating system vulnerabilities.
User-Mode Rootkit Case Studies
User-mode rootkits manipulate operating system processes by injecting malicious code into legitimate applications to evade detection, exemplified by the Hacker Defender rootkit targeting Windows systems. This rootkit modifies Windows APIs at the user level to hide files, processes, and network activities from security software. Analysis of User-Mode rootkits like Hacker Defender highlights the sophistication of process manipulation techniques used to maintain persistent unauthorized access while bypassing kernel-level defenses.
Kernel-Mode Rootkit Instances
Kernel-mode rootkits like Sony BMG's XCP force audio CD DRM embed themselves deep within the Windows operating system, manipulating system calls to hide their presence. The Stuxnet worm exploited kernel-mode rootkit techniques to remain undetected while targeting industrial control systems. Fu exploiting vulnerable drivers, these rootkits gain privileged access, allowing persistent, stealthy control over critical OS components.
Firmware and Bootkit Rootkit Examples
Firmware rootkits like LoJax manipulate UEFI firmware to gain persistent, low-level control over a system, evading detection by traditional antivirus tools. Bootkit rootkits such as the Mebromi infect the Master Boot Record (MBR) or Volume Boot Record (VBR) to execute malicious code during the system startup, bypassing security mechanisms. These rootkits exemplify advanced threats targeting the firmware and boot processes to maintain stealthy, long-term access to compromised devices.
Real-World Corporate Rootkit Attacks
Sony BMG's 2005 rootkit scandal involved embedding stealth software within music CDs, enabling unauthorized access to user systems and evading detection by operating systems. Stuxnet, discovered in 2010, targeted Windows OS by using rootkit techniques to manipulate industrial control systems, exemplifying state-sponsored corporate sabotage. These incidents highlight the severe security risks that rootkits pose to operating systems in corporate environments.
Open Source Rootkit Demonstrations
Open source rootkit demonstrations like Azazel and OpenRDK provide valuable insights into stealth techniques used to exploit operating systems, particularly Linux variants. These rootkits manipulate kernel modules or user-space applications to gain unauthorized access and conceal malicious activities from standard detection tools. Researchers utilize these examples to develop more effective detection and mitigation strategies against advanced persistent threats in open source environments.
Rootkit Detection in Popular Operating Systems
Rootkit detection in popular operating systems such as Windows, Linux, and macOS relies on specialized tools like GMER, chkrootkit, and OSRFramework that scan for hidden processes, kernel-level modifications, and unauthorized system calls. Windows uses Windows Defender and Sysinternals Rootkit Revealer to identify stealthy rootkit behavior by monitoring system integrity and unusual disk activity. Linux-based systems incorporate kernel module integrity checks and audit frameworks, while macOS leverages built-in System Integrity Protection (SIP) to prevent unauthorized kernel extensions typical of rootkits.
Rootkit Removal Tools and Techniques
Rootkit removal tools like GMER, Malwarebytes Anti-Rootkit, and Kaspersky TDSSKiller effectively detect and eliminate stealthy rootkits from operating systems by scanning for hidden processes, files, and registry keys. Techniques such as boot-time scanning, signature-based detection, and heuristic analysis enhance the identification of sophisticated rootkits that evade traditional antivirus software. Employing system restore points and reinstalling the operating system remain essential steps when rootkit removal tools cannot fully eradicate deeply embedded threats.
Lessons Learned from Rootkit Incidents
Rootkit incidents such as the Sony BMG DRM scandal and the Stuxnet attack highlight critical lessons in operating system security, emphasizing the need for robust kernel-level monitoring and early detection mechanisms. These breaches revealed vulnerabilities in trusted computing bases, demonstrating the importance of timely patch management and strict access control policies. Insights from these cases drive the development of advanced rootkit detection tools and reinforce the necessity of comprehensive security audits to prevent covert persistence.
example of rootkit in operating system Infographic
 samplerz.com
samplerz.com