A botnet is a network of compromised computers or devices controlled by a cybercriminal to execute coordinated malicious activities. One notable example of a botnet in malware is the Mirai botnet, which targets Internet of Things (IoT) devices such as cameras and routers by exploiting default login credentials. Mirai was responsible for large-scale distributed denial-of-service (DDoS) attacks that disrupted major websites and internet services. Another prominent example is the Zeus botnet, which primarily targets Windows-based systems to steal banking information and commit financial fraud. Zeus malware infiltrates computers through phishing emails or malicious downloads, subsequently harvesting sensitive data from infected machines. Both Mirai and Zeus highlight the capabilities of botnets to cause extensive harm by leveraging networks of infected devices for malicious purposes.
Table of Comparison
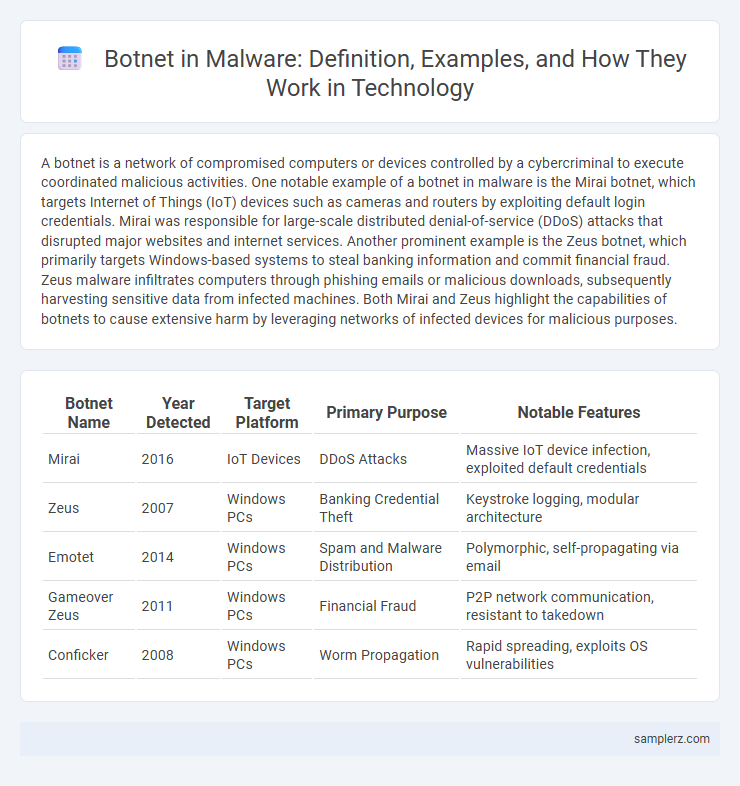
| Botnet Name | Year Detected | Target Platform | Primary Purpose | Notable Features |
|---|---|---|---|---|
| Mirai | 2016 | IoT Devices | DDoS Attacks | Massive IoT device infection, exploited default credentials |
| Zeus | 2007 | Windows PCs | Banking Credential Theft | Keystroke logging, modular architecture |
| Emotet | 2014 | Windows PCs | Spam and Malware Distribution | Polymorphic, self-propagating via email |
| Gameover Zeus | 2011 | Windows PCs | Financial Fraud | P2P network communication, resistant to takedown |
| Conficker | 2008 | Windows PCs | Worm Propagation | Rapid spreading, exploits OS vulnerabilities |
Notorious Botnet Attacks in Malware History
The Mirai botnet exemplifies a notorious malware attack that hijacked vast numbers of IoT devices to launch massive DDoS assaults, crippling major websites in 2016. Another infamous botnet, Zeus, specialized in stealing banking credentials, causing billions in financial losses globally. Conficker remains a persistent threat, infecting millions of computers by exploiting Windows vulnerabilities to form a resilient malware network.
Real-World Botnet Malware Examples
Mirai is a notorious botnet malware that infected IoT devices to launch massive DDoS attacks, disrupting major websites globally. Emotet started as a banking Trojan but evolved into a modular botnet spreading malware through phishing emails, compromising corporate networks. Another significant example is ZeuS, which targeted financial institutions to steal sensitive banking credentials and facilitate fraud.
Famous Botnets: Zeus, Mirai, and Beyond
Zeus, Mirai, and Emotet represent some of the most infamous botnets in cybersecurity history, each targeting distinct vulnerabilities to execute large-scale attacks. Zeus primarily infected Windows PCs to steal banking credentials, Mirai hijacked IoT devices to launch massive DDoS attacks, and Emotet evolved from a banking Trojan to a modular botnet facilitating various cybercrimes. These botnets highlight the evolving complexity and scale of malware-driven networks, posing significant threats to global digital infrastructure.
How Botnets Operate in Modern Malware
Botnets in modern malware operate by compromising large networks of vulnerable devices through automated malware distribution, creating a vast pool of interconnected systems controlled remotely by attackers. These hijacked devices, often IoT gadgets or personal computers, communicate with a command-and-control server that issues instructions for coordinated tasks like distributed denial-of-service (DDoS) attacks, data theft, or spam campaigns. Advanced botnets utilize peer-to-peer architectures and encryption to evade detection and maintain resilience against takedown efforts.
Case Study: Mirai Botnet DDoS Attack
The Mirai botnet exploited IoT devices by infecting millions of poorly secured cameras and routers, orchestrating one of the largest DDoS attacks in history with traffic exceeding 1 Tbps. This attack targeted major DNS provider Dyn in 2016, causing widespread internet outages affecting sites like Twitter, Netflix, and Reddit. Mirai's source code release highlighted critical vulnerabilities in IoT security, prompting urgent improvements in device authentication and network defense strategies.
Conficker: A Persistent Botnet Threat
Conficker, also known as Downadup, is a highly resilient botnet that exploited a Windows vulnerability in 2008, infecting millions of computers worldwide. This malware leveraged advanced evasion techniques to form one of the largest botnets, facilitating unauthorized access and facilitating large-scale malicious activities such as data theft and DDoS attacks. Persistent in nature, Conficker continues to pose a significant cybersecurity threat, illustrating the challenges in neutralizing sophisticated botnet infections.
Emotet: Evolution of a Malware Botnet
Emotet exemplifies the evolution of a sophisticated malware botnet, initially designed as a banking Trojan and later transforming into a modular, multi-purpose threat platform. Its advanced propagation techniques, including spam campaigns and exploit kits, enable widespread infection across corporate and government networks worldwide. Emotet's adaptive infrastructure continually updates payloads and evades detection, highlighting the persistent challenges in cybersecurity defense mechanisms.
Internet of Things (IoT) Botnet Examples
Mirai represents a notorious example of an Internet of Things (IoT) botnet, exploiting weak default passwords to compromise thousands of devices and launch large-scale DDoS attacks. Other IoT botnets like Gafgyt and Hajime utilize vulnerabilities in smart cameras, routers, and DVRs to infiltrate networks and propagate malware. These botnets highlight critical security risks posed by interconnected IoT devices with insufficient protection.
Botnet Malware: Impact on Cybersecurity
Botnet malware, such as the infamous Mirai botnet, has significantly impacted cybersecurity by commandeering thousands of IoT devices to launch massive distributed denial-of-service (DDoS) attacks, crippling websites and online services globally. These botnets exploit vulnerabilities in connected devices, enabling cybercriminals to execute large-scale cyberattacks, steal sensitive data, and disrupt critical infrastructures. The proliferation of botnet malware has intensified the need for robust cybersecurity measures, including real-time network monitoring and device hardening.
Prevention and Defense Against Botnet Malware
Botnet malware such as Mirai demonstrates how compromised devices can be controlled remotely to launch large-scale DDoS attacks, emphasizing the need for robust network security protocols and device hardening. Employing firewalls, intrusion detection systems, and regular firmware updates effectively mitigate the risks associated with botnet infections. User education on avoiding suspicious downloads and leveraging network segmentation strengthens defenses against botnet proliferation.
example of botnet in malware Infographic
 samplerz.com
samplerz.com