Steganography is a powerful technique used in data hiding that involves embedding secret information within ordinary digital files such as images, audio, or video. For example, a common method uses the least significant bit (LSB) of pixel values in an image file to conceal messages without visibly altering the image. This technique leverages the redundancy in digital data to maintain the cover file's appearance while securely transmitting hidden information. In the context of technology, steganography enhances data security by enabling covert communication, especially in encrypted messaging and digital watermarking. The technique is frequently employed in multimedia files, where slight modifications remain imperceptible to human senses but are detectable by specific extraction algorithms. Modern steganographic tools balance between payload capacity, robustness, and imperceptibility to optimize data hiding effectiveness.
Table of Comparison
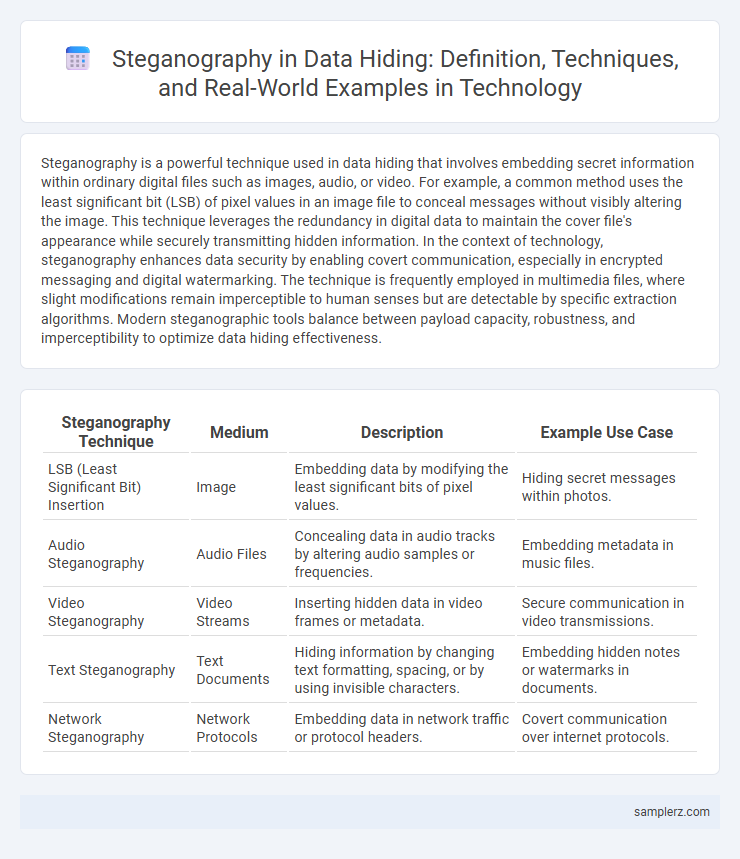
| Steganography Technique | Medium | Description | Example Use Case |
|---|---|---|---|
| LSB (Least Significant Bit) Insertion | Image | Embedding data by modifying the least significant bits of pixel values. | Hiding secret messages within photos. |
| Audio Steganography | Audio Files | Concealing data in audio tracks by altering audio samples or frequencies. | Embedding metadata in music files. |
| Video Steganography | Video Streams | Inserting hidden data in video frames or metadata. | Secure communication in video transmissions. |
| Text Steganography | Text Documents | Hiding information by changing text formatting, spacing, or by using invisible characters. | Embedding hidden notes or watermarks in documents. |
| Network Steganography | Network Protocols | Embedding data in network traffic or protocol headers. | Covert communication over internet protocols. |
Introduction to Steganography in Data Hiding
Steganography in data hiding involves embedding secret information within ordinary digital files, such as images, audio, or video, without noticeably altering the file's appearance or quality. Common techniques include least significant bit (LSB) modification, where data is hidden in the least significant bits of pixel values, and transform domain methods, which embed information in frequency coefficients to improve robustness. These methods enable covert communication by concealing sensitive data within innocuous media, enhancing secure information exchange in digital forensics and cybersecurity.
Classic Image-Based Steganography Techniques
Classic image-based steganography techniques include Least Significant Bit (LSB) insertion, where hidden information is embedded in the least significant bits of pixel values, preserving the visual quality of the image. Another method involves manipulating the discrete cosine transform (DCT) coefficients in compressed images such as JPEG, allowing secret data to be concealed without noticeable distortion. These methods enable covert communication by embedding data within digital images while maintaining the original image's appearance and reducing the risk of detection.
Audio File Steganography Methods
Audio file steganography methods embed secret data within audio signals by manipulating audio properties such as phase, amplitude, and frequency. Techniques like Least Significant Bit (LSB) coding, phase coding, and echo hiding enable efficient and imperceptible data hiding in WAV, MP3, and other audio formats. These methods maintain audio quality while providing secure communication channels against unauthorized detection.
Video Steganography: Concealing Data in Multimedia
Video steganography involves embedding secret information within video files by manipulating pixels, frames, or motion vectors without perceptible changes to the original content. Techniques such as Least Significant Bit (LSB) modification and transform domain approaches enable secure communication through concealed data in multimedia. This method enhances confidentiality and supports covert data transmission over widely used platforms like streaming services and social media.
Text Steganography: Hiding Information in Plain Sight
Text steganography embeds secret messages within seemingly ordinary text by manipulating font styles, spacing, or invisible characters, effectively concealing data without raising suspicion. Techniques like zero-width characters insertion or subtle formatting changes enable covert communication in digital documents and social media. These methods enhance data security by hiding information in plain sight, bypassing traditional encryption detection systems.
Network Steganography: Covert Channel Communication
Network steganography enables covert channel communication by embedding hidden data within normal network protocols such as TCP/IP headers, DNS queries, or HTTP traffic. Techniques like manipulating packet timing, altering unused header fields, or encoding messages in protocol-specific payloads allow data hiding without raising suspicion. These methods enhance secure information exchange by leveraging existing network infrastructure for stealthy communication.
Steganography in Email and Messaging Platforms
Steganography in email and messaging platforms involves embedding hidden messages within ordinary text, images, or attachments to securely transmit confidential information without detection. Techniques like hiding secret data in image pixels or manipulating email headers ensure covert communication while preserving message readability and format. This method enhances security by preventing unauthorized access and bypassing traditional encryption detection mechanisms used in cyber surveillance.
Real-World Applications of Steganography
Steganography is widely used in digital watermarking to protect intellectual property by embedding invisible marks within images, videos, or audio files. It enables covert communication in military operations by hiding sensitive messages in seemingly innocuous digital content, ensuring secure data transmission. Social media platforms employ steganographic techniques to prevent content tampering and verify authenticity through hidden metadata in shared media files.
Steganography Tools and Software Overview
Steganography tools like OpenPuff, Steghide, and SilentEye offer advanced methods for embedding hidden data within various digital media formats including images, audio, and video files. These software solutions utilize sophisticated algorithms such as LSB (Least Significant Bit) modification and DCT (Discrete Cosine Transform) to conceal information without noticeably altering the cover files. Widely used in secure communication and digital watermarking, these steganography programs ensure data confidentiality by masking the existence of the hidden content.
Future Trends in Steganography for Data Hiding
Future trends in steganography for data hiding emphasize the integration of artificial intelligence and machine learning algorithms to enhance detection resistance and embedding capacity. Quantum computing advancements promise to revolutionize steganographic techniques by enabling more complex and secure data embedding methods. Emerging applications include secure communication in IoT devices and blockchain technology, where data privacy and integrity are paramount.
example of steganography in data hiding Infographic
 samplerz.com
samplerz.com