Cryptojacking is a malicious practice where attackers secretly use a victim's computing power to mine cryptocurrency without their consent. An example of cryptojacking in cryptocurrency occurred when hackers compromised thousands of web servers and injected mining scripts into legitimate websites. These scripts exploited visitors' CPUs to mine Monero, a privacy-focused cryptocurrency, quietly generating profits for the attackers. In another incident, malware was distributed via phishing emails targeting corporate networks, enabling attackers to install cryptojacking software on compromised endpoints. This unauthorized mining operation significantly slowed down the affected systems, causing operational disruptions while bypassing traditional security detection methods. Mining cryptocurrencies like Monero through cryptojacking highlights the threat to both individual users and enterprises in the evolving crypto ecosystem.
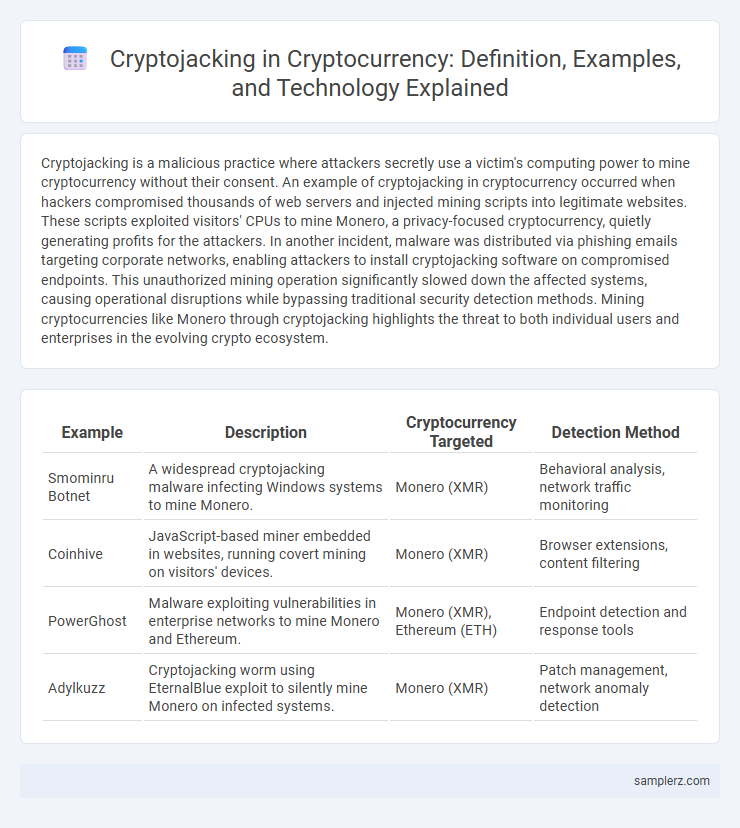
Table of Comparison
| Example | Description | Cryptocurrency Targeted | Detection Method |
|---|---|---|---|
| Smominru Botnet | A widespread cryptojacking malware infecting Windows systems to mine Monero. | Monero (XMR) | Behavioral analysis, network traffic monitoring |
| Coinhive | JavaScript-based miner embedded in websites, running covert mining on visitors' devices. | Monero (XMR) | Browser extensions, content filtering |
| PowerGhost | Malware exploiting vulnerabilities in enterprise networks to mine Monero and Ethereum. | Monero (XMR), Ethereum (ETH) | Endpoint detection and response tools |
| Adylkuzz | Cryptojacking worm using EternalBlue exploit to silently mine Monero on infected systems. | Monero (XMR) | Patch management, network anomaly detection |
Introduction to Cryptojacking in Cryptocurrency
Cryptojacking in cryptocurrency involves unauthorized use of someone's device to mine digital coins like Bitcoin or Monero, exploiting computational power without consent. This cyberattack typically occurs through malicious software or compromised websites that secretly execute mining scripts in the background. The surge of cryptojacking incidents has raised significant security concerns across blockchain networks and personal devices, emphasizing the need for robust cybersecurity measures.
How Cryptojacking Works: A Technical Overview
Cryptojacking in cryptocurrency involves unauthorized use of a victim's device to mine digital coins like Monero or Bitcoin by exploiting CPU or GPU resources without consent. Typically, attackers inject malicious scripts into websites or distribute malware that runs cryptomining code silently in the background, causing device slowdown and increased power consumption. Detection relies on monitoring unusual system performance, high CPU usage, and suspicious network activity linked to cryptomining pools.
Real-World Cases of Cryptocurrency Cryptojacking
Malicious actors exploited vulnerabilities in Android apps to secretly mine Monero on millions of devices, draining battery life and bandwidth. Websites like Pirate Bay unwittingly hosted cryptojacking scripts that harnessed visitors' CPU power without consent. In 2018, Showtime's website was compromised with hidden mining code targeting users, highlighting the widespread impact of cryptojacking on popular platforms.
Notorious Cryptojacking Attacks in History
Notorious cryptojacking attacks in cryptocurrency include the 2018 Coinhive exploitation, where hackers embedded malicious scripts on thousands of websites to mine Monero without user consent, generating millions in illicit profits. Another significant incident involved the 2017 Tesla cloud cryptojacking attack, where cybercriminals exploited Kubernetes consoles to deploy crypto-mining malware, highlighting vulnerabilities in cloud infrastructure. These attacks underscore the growing threat of unauthorized crypto mining leveraging high-profile platforms and advanced security loopholes.
Methods Hackers Use for Cryptojacking
Hackers employ methods such as embedding malicious JavaScript code into legitimate websites to secretly mine cryptocurrency using visitors' CPU resources. They also distribute malware through phishing emails or software downloads that install cryptomining scripts on victims' devices without their knowledge. Exploiting vulnerable networked devices and IoT systems enables continuous cryptojacking, leveraging weak security protocols to drain processing power for cryptocurrency mining.
Signs Your System Is a Victim of Cryptojacking
Unexpected spikes in CPU usage and sluggish system performance often signal cryptojacking activities, where malicious scripts mine cryptocurrency without user consent. Frequent overheating and rapid battery drain on laptops or mobile devices can also indicate unauthorized mining operations. Network latency and unexplained spikes in internet data usage further reveal that your system might be compromised by cryptojacking malware.
The Impact of Cryptojacking on Individuals and Businesses
Cryptojacking drains significant amounts of computing power, causing slower device performance and increased electricity costs for individuals and businesses. This unauthorized use of resources compromises data security, leading to potential breaches and loss of sensitive information. Financial losses escalate as organizations face downtime, reduced productivity, and expenses related to malware removal and system restoration.
Tools and Software Commonly Exploited for Cryptojacking
Cryptojacking commonly exploits web browsers through malicious JavaScript injected into websites, leveraging tools like Coinhive and JSEcoin to mine cryptocurrencies without user consent. Vulnerabilities in outdated software such as Adobe Flash and unpatched CMS platforms like WordPress also serve as entry points for cryptojacking scripts. Cybercriminals frequently target cloud services and compromised IoT devices due to their powerful computing resources, maximizing mining efficiency through tools like XMRig and other open-source mining software.
Preventing and Mitigating Cryptojacking in Cryptocurrency
Effective prevention of cryptojacking in cryptocurrency involves deploying advanced endpoint security solutions equipped with real-time malware detection and behavioral analysis to identify unauthorized mining activities. Implementing multi-factor authentication (MFA) and routinely updating software patches significantly reduce vulnerabilities exploited by cryptojackers. Network monitoring tools designed for anomaly detection help in early identification and swift mitigation of cryptojacking attacks within blockchain environments.
Future Trends and Emerging Threats in Cryptojacking
Cryptojacking in cryptocurrency is evolving with the rise of more sophisticated malware leveraging AI to bypass detection by traditional antivirus systems. Future trends indicate an increase in cloud-based cryptojacking attacks targeting decentralized finance (DeFi) platforms and Internet of Things (IoT) devices due to their high computational power and lax security. Emerging threats include cross-platform cryptojacking campaigns exploiting vulnerabilities in smart contracts and blockchain nodes, posing significant risks to the integrity and performance of cryptocurrency networks.
example of cryptojacking in cryptocurrency Infographic
 samplerz.com
samplerz.com