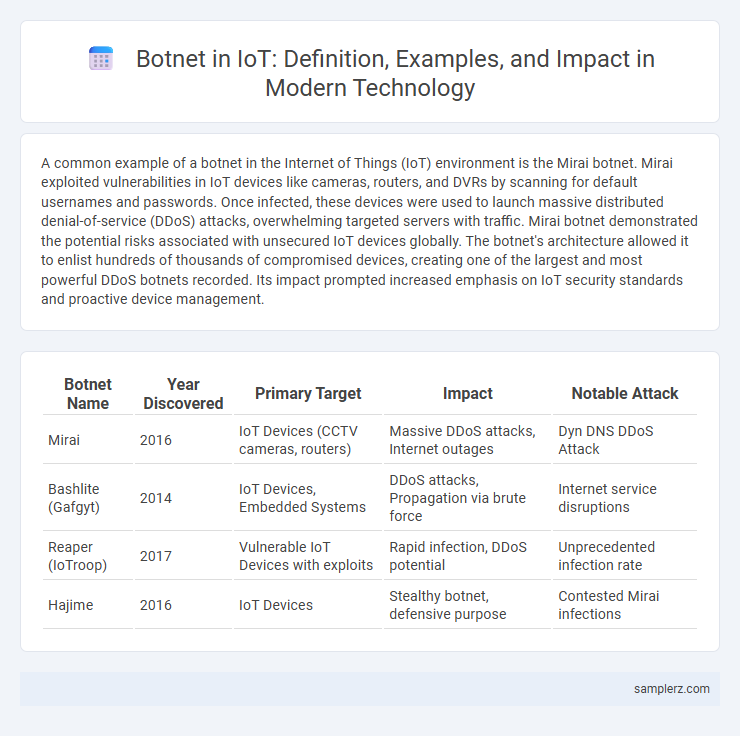
A common example of a botnet in the Internet of Things (IoT) environment is the Mirai botnet. Mirai exploited vulnerabilities in IoT devices like cameras, routers, and DVRs by scanning for default usernames and passwords. Once infected, these devices were used to launch massive distributed denial-of-service (DDoS) attacks, overwhelming targeted servers with traffic. Mirai botnet demonstrated the potential risks associated with unsecured IoT devices globally. The botnet's architecture allowed it to enlist hundreds of thousands of compromised devices, creating one of the largest and most powerful DDoS botnets recorded. Its impact prompted increased emphasis on IoT security standards and proactive device management.
Table of Comparison
| Botnet Name | Year Discovered | Primary Target | Impact | Notable Attack |
|---|---|---|---|---|
| Mirai | 2016 | IoT Devices (CCTV cameras, routers) | Massive DDoS attacks, Internet outages | Dyn DNS DDoS Attack |
| Bashlite (Gafgyt) | 2014 | IoT Devices, Embedded Systems | DDoS attacks, Propagation via brute force | Internet service disruptions |
| Reaper (IoTroop) | 2017 | Vulnerable IoT Devices with exploits | Rapid infection, DDoS potential | Unprecedented infection rate |
| Hajime | 2016 | IoT Devices | Stealthy botnet, defensive purpose | Contested Mirai infections |
Mirai: The Most Infamous IoT Botnet
Mirai stands as the most infamous IoT botnet, notorious for exploiting weak default credentials to infect and control hundreds of thousands of connected devices like cameras and routers. It launched massive distributed denial-of-service (DDoS) attacks, including the 2016 Dyn attack, which disrupted major internet services across the United States. Security researchers emphasize Mirai's impact as a wake-up call for hardening IoT device security and improving network defenses against botnet threats.
Hajime: A Self-Spreading IoT Threat
Hajime is a sophisticated self-spreading botnet targeting Internet of Things (IoT) devices by exploiting weak security protocols and default credentials. It propagates silently across millions of devices globally, creating a decentralized peer-to-peer network that resists takedown efforts. Security researchers highlight Hajime's advanced stealth techniques and its potential to disrupt critical IoT infrastructure through large-scale coordinated attacks.
Bashlite: Targeting Connected Devices
Bashlite is a notorious botnet primarily targeting IoT devices such as routers, cameras, and DVRs by exploiting weak or default passwords to gain unauthorized access. It propagates through Telnet brute-force attacks, enabling it to generate massive Distributed Denial of Service (DDoS) attacks. The persistent evolution of Bashlite underscores the critical need for robust device security and regular firmware updates in the connected device ecosystem.
Mozi Botnet: Peer-to-Peer IoT Attacks
Mozi Botnet exemplifies peer-to-peer IoT attacks by leveraging a decentralized architecture that targets vulnerable smart devices such as routers, DVRs, and IP cameras. Its propagation method exploits weak credentials and known exploits to form a resilient network resistant to takedown efforts. By continuously scanning for insecure IoT devices, Mozi orchestrates large-scale distributed denial-of-service (DDoS) attacks while maintaining communication through a peer-to-peer protocol.
LightAidra: Infecting Embedded Devices
LightAidra botnet exemplifies a sophisticated cyber threat targeting IoT ecosystems by infecting embedded devices such as routers, cameras, and industrial controllers. Exploiting vulnerabilities in device firmware and weak authentication protocols, LightAidra enables attackers to orchestrate large-scale DDoS attacks and data breaches. Its rapid propagation and stealthy operation highlight critical security challenges within interconnected IoT infrastructures.
VPNFilter: Multi-Stage IoT Malware
VPNFilter is a sophisticated multi-stage IoT malware that targets routers and network-attached storage devices, compromising millions of devices worldwide. It executes various malicious activities, including data theft, device manipulation, and network traffic interception, by exploiting vulnerabilities in IoT infrastructures. The botnet's complexity and persistence demonstrate significant risks to global internet security and underscore the urgency of enhanced IoT device protection measures.
Torii Botnet: Advanced IoT Infiltration
The Torii Botnet exemplifies advanced IoT infiltration by exploiting vulnerabilities in connected devices to create a vast network of compromised systems. This botnet leverages sophisticated command-and-control mechanisms via encrypted communication channels, enabling stealthy operations and persistent control over targeted IoT devices. Its capacity to launch large-scale distributed denial-of-service (DDoS) attacks highlights the critical security risks posed by unprotected IoT ecosystems.
IoTroop (Reaper): Evolving Botnet Tactics
IoTroop, also known as Reaper, exemplifies an evolving IoT botnet leveraging vulnerabilities in routers, IP cameras, and DVRs to orchestrate large-scale distributed denial-of-service (DDoS) attacks. Unlike traditional botnets, IoTroop integrates advanced techniques such as exploiting zero-day vulnerabilities and automated patching evasion, increasing its resilience and control over compromised devices. Its continuous adaptation highlights critical security challenges in managing the expanding IoT ecosystem.
Persirai: Attacking IP Cameras
Persirai is a notorious IoT botnet that specifically targets IP cameras, exploiting over 120 hardcoded default credentials to compromise devices. This botnet leverages vulnerable firmware in thousands of IoT surveillance cameras worldwide, transforming them into a massive network for launching distributed denial-of-service (DDoS) attacks. Its ability to hijack such a vast range of devices highlights the critical need for improved security measures and firmware updates in IoT ecosystems.
Amnesia: Exploiting IoT DVRs
Amnesia is a notorious IoT botnet that exploits vulnerabilities in digital video recorders (DVRs) to create massive distributed networks for cyberattacks. By targeting insecure default credentials and outdated firmware in IoT DVR devices, Amnesia gains unauthorized access and recruits these gadgets into its malicious infrastructure. This botnet demonstrates significant threats to IoT security, emphasizing the need for robust device authentication and timely software updates.
example of botnet in IoT Infographic
 samplerz.com
samplerz.com